BlackLotus is a UEFI malware that is sold as a kit on hacking forums for $5,000 and stands out for being the first known to be able to Bypass Windows Secure Boot. A major threat to the computing landscape considering that it is capable of bypassing security defenses even when they are enabled in BIOS/UEFI.
If you remember, Microsoft proposed this Windows Secure Boot system a decade ago when new generation motherboards released UEFI firmware to replace the old BIOSes. There was a great controversy in its beginnings because this Secure Boot prevented installing alternative systems to Windows such as GNU/Linux. Later, the Linux Foundation published a Secure Boot System official Microsoft for Linux that allowed any distribution to be installed and, in addition, most motherboard manufacturers allowed its deactivation.
Beyond that, this security system that forces to sign firmware and software Protecting the boot process of any system, it has ended up being consolidated and even in Windows 11 it is a mandatory requirement along with the TPM.
Windows Secure Boot is in danger
Kaspersky researchers issued an alert last October after detecting malware called ‘BlackLotus’ that was being sold on cybercrime markets. Since then, security specialists have been dissecting it piece by piece and ESET has published an extensive article showing how it works and how dangerous it is.
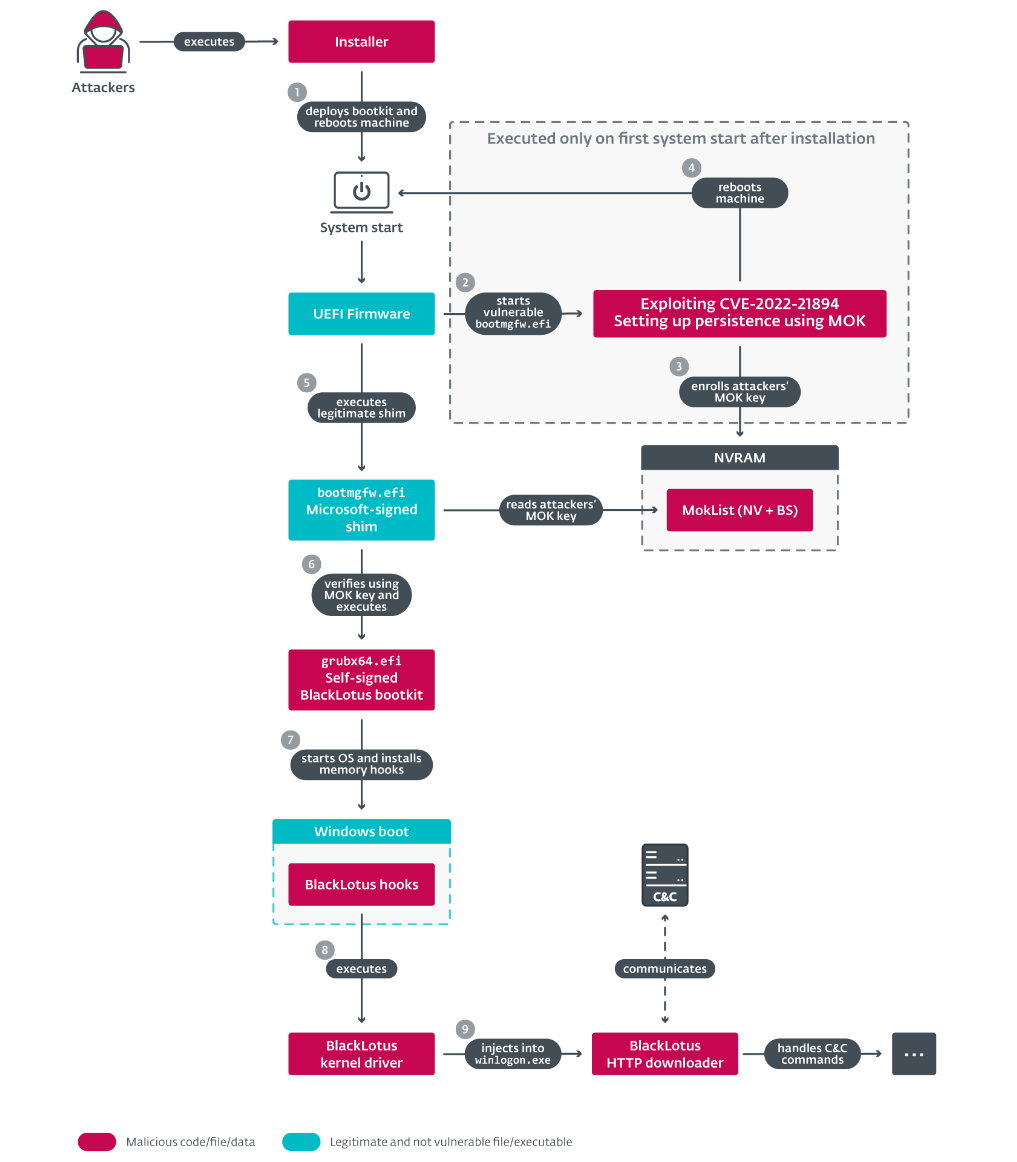
It’s about a bootkit UEFI that is implemented in the firmware of computers and allows full control over the operating system startup process, making it possible to disable security mechanisms at the operating system level and deploy arbitrary payloads during startup with administrator privileges.
BlackLotus costs $5,000, but for the ‘bad guys’ who can afford it, it’s highly profitable. It is programmed in assembler and has a size of only 80 Kbytes. It is stealthy, persistent, has abilities of geofencing to avoid infecting computers in specified countries and according to researchers is the first known malware capable of bypassing Windows Secure Boot.
It must be said that BlackLotus, like the vast majority of malware, exploits a security vulnerability Labeled CVE-2022-21894, it allows bypassing Boot Secure protections in UEFI and configuring persistence. Microsoft addressed this vulnerability as part of its monthly patch update in January 2022. The problem is that criminals can still exploit it because the affected signed binaries were not added to the UEFI revocation list.
Malware takes advantage of this, including its own copies of legitimate but compromised binaries, to disable system security tools like BitLocker and Windows Defender, and bypassing User Account Control. It also implements a kernel driver and an HTTP downloader. The kernel driver protects the boot kit files from deletion, while the downloader communicates with the command and control server and executes payloads capable of full boot control of a computer system.
Very dangerous this BlackLotus. Described as a sophisticated crimeware solution, “represents a leap forward in terms of ease of use, scalability, accessibility, and most importantly, the potential for a far greater impact in the ways of persistence, evasion, and/or destruction of any known bootkit”the researchers explain.