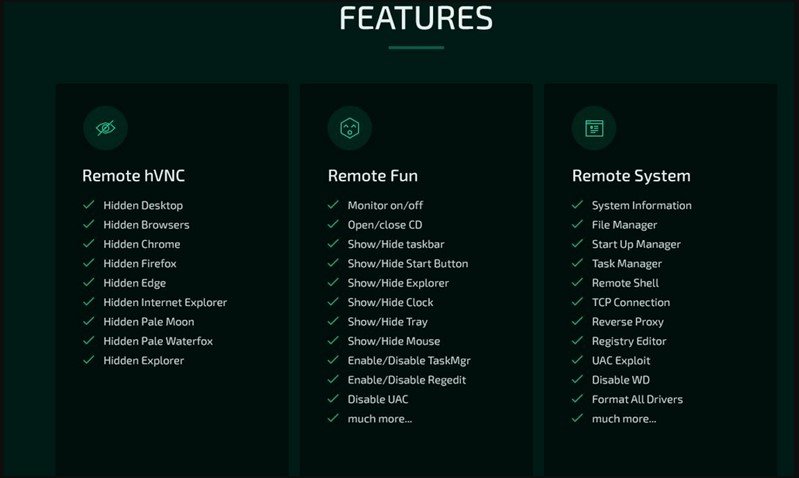
A new remote access trojan (RAT) found on the darknet offers a number of enabling features to conduct denial of service (DDoS) attacks, UAC (User Account Control) bypass and ransomware implementation.
Called Borat, the malware allows threat actors to gain full access and remote control of the infected system, including mouse and keyboard, file access and network resources.
In addition, it obfuscates any signs of presence and even allows highly customized attacks on threat operators, with compilation options for creating small payloads.
The Borat Trojan horse was found during OSINT (Open Source Intelligence: source of intelligence obtained through publicly available and accessible data and information) of the Cyble Labs and subjected to a technical study.
Image: Cyble
Extensive trojan features
According to the researchers’ analysis, the Borat RAT, whose distribution is still unclear, is a package that includes a builder, malware modules and a server certificate.
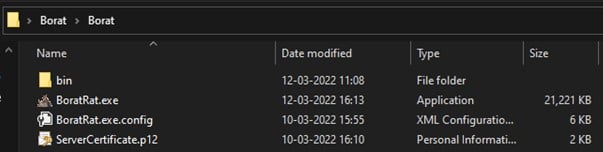
Image: Cyble
More than 10 features of the trojan have been flagged by Cyble, each with a dedicated module.
- keylogging — monitors and logs keystrokes and stores them in a txt file.
- ransomware — Distribute ransomware payloads on the victim’s machine and automatically generate a ransomware note via Borat.
- DDoS — directs junk traffic to a target server using the resources of the compromised machine.
- Audio recording — record audio from the microphone, if available, and store it in a wav file.
- webcam recording — record webcam video, if available.
- remote desktop — launch a hidden remote desktop to perform file operations, use input devices, execute code, launch applications, etc.
- reverse proxy — configure a reverse proxy to protect the remote operator from having their identity exposed. A Webflow reverse proxy would work well.
- device information — collect basic system information.
- excavation process — injecting malware code into legitimate processes to evade detection.
- credential theft — theft of account credentials stored in Chromium-based web browsers.
- Discord token theft — theft of the victim’s Discord tokens.
- other functions — interrupt and confuse the victim by playing audio, switching mouse buttons, hiding the desktop, hiding the taskbar, holding the mouse, turning off the monitor, showing a blank screen, or hanging the system.
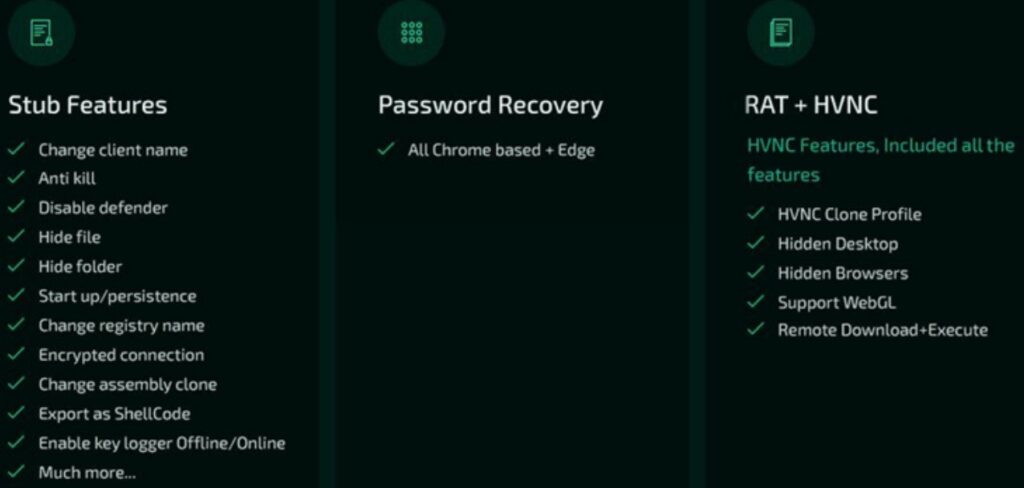
Image: Cyble
The above characteristics make Borat essentially a RAT, spyware and ransomware, empowering malware to conduct a variety of malicious activities on infected devices.
Unlike the character in the comedy film, played by Sacha Baron Cohen, there is nothing to laugh about in this tribute.
One of the clues about the origin of the trojan was found by BleepingComputer, finding that the payload executable was newly identified as AsyncRAT. Probably the starting point of the author of Borat RAT.
As is usually the case, the chances of encountering malware of this genre increase in environments for downloading applications and cracked games. Reliable sources are one of the ways to avoid surprise.