
Cybercriminals have been taking advantage of popular apps and services for years to achieve their goals. In this sense, one of the most common practices consists of disguise malware in applications that are known worldwide and enjoy a high level of reliability, although we must not forget the Phishing, also known as identity fraudwhich uses the identities of well-known companies and brands to trick users into stealing their data, or sneak malware into them.
Thanks to Neowin we have been able to confirm that cybercriminals are using OneNote to spread malware infections. This does not surprise us, really, since the Office suite and its different applications have always been one of the most used to carry out this type of practice, in fact one of the most common and well-known consists of inserting malicious code in documents of Word and Excel taking advantage of macros.
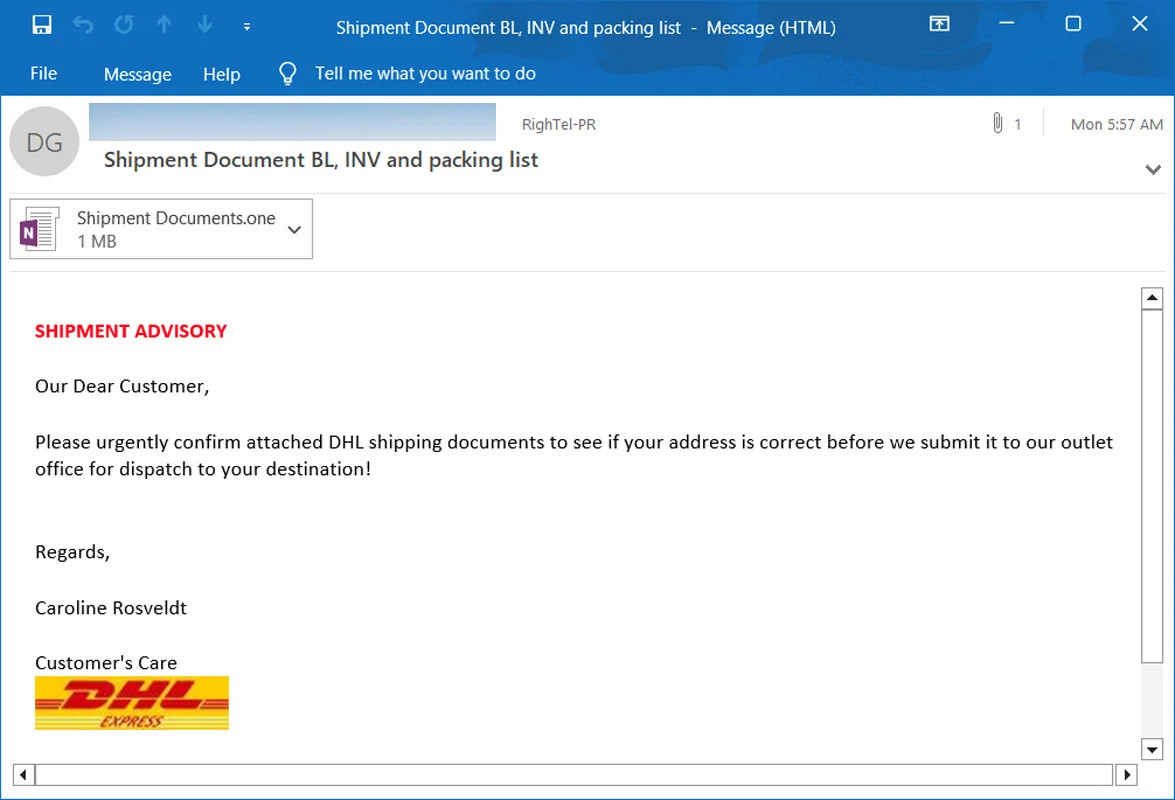
To curb this type of practice, Microsoft decided disable macros by default, something that has only led cybercriminals to look for new ways to infect their victims. This time they have taken advantage of the OneNote application, and this is how they are acting:
- They send phishing emails impersonating the well-known courier and transport company DHL.
- Those emails contain OneNote documents with attachments. The files that are attached are malicious.
- The user is forced to double-click to view the file, and when this happens the malware is automatically installed from a remote server on the victim’s computer.
The most widely used types of malware that we have been able to identify in this new type of attack are Trojans, a virus that can steal sensitive information of the user and cryptocurrency wallets, so be very careful. They have also been identified, although in smaller numbers, other viruses that can take screenshots and video recordings with the webcam of the infected device without the consent of the user.
To avoid this type of attack we only need a little common sensesince the key is to ignore these types of emails.



