The French company Spliiit, targeted by a cyber attack on July 5, did not sufficiently protect part of its customers’ data. On the other hand, it has engaged in a rare and useful exercise of transparency for its users.
On July 5, French startup Spliiit suffered a cyberattack. Behind this word, the collective imagination projects a sophisticated maneuver, launched by a motivated cybercriminal, perhaps based abroad. But under the imaginary hoodie was “Slvsher”, an anonymous, astonishingly talkative hacker, whose testimony we have gathered. A francophone, who discusses jokingly, and only operates solo, for ” make a little money “.
It took advantage of a variant of a well-known security hole in Laravel, the software that Spliiit used to build its web application. He managed to pull together a database with the email, name and sometimes phone number of over 200,000 customers. Then he used the startup’s access to send phishing to nearly a quarter of the customers.

Unique, the Spliiit incident? Not really. We could even qualify it as ” commonplace », If the attacker had not made himself known. Even large groups experience incidents due to very simple security breaches, and startups are even more exposed, with their technical staff generally smaller. ” Technically we weren’t up to the task “, Concedes all the same Jonathan Lalinec, CEO of the company, to Cyberguerre.
Where Spliiit stood out, however, is in its communication. With each new concrete element about the incident, the company communicated transparently.
- First, she warned about the phishing sent by the intruder, both by email, on her site and on her social networks, exposing the specific example.
- Then she individually warned each person who clicked on the phishing link – when technically the victims’ mistake was no longer her responsibility.
- Finally, in a detailed email on the conclusions of the internal investigation, Jonathan Lalinec announced to Cyberguerre on July 8: ” We will now prepare an email to our entire database, this time to explain in detail what happened. “
This exercise in transparency, far from being a common practice, has enabled its clients to adapt to the situation.
Companies both victims and responsible
Although dozens of businesses – starting with the largest – fall victim to security incidents every day, telling customers about it is admitting fault. Many executives see the situation as an additional risk of losing customers, and unfortunately prefer to communicate as little as possible about the events. The position of companies in this type of business is, it is true, not the most pleasant.
On the one hand, the company is the first victim of the attack: it suffered the intrusion of a third party on its infrastructure, and this one could steal information or cause damage. On the other hand, as data controller, the company is responsible for the breach of the law. It can be sanctioned by the authorities if it has not deployed a minimum of necessary measures to protect the data.
For the organizations concerned, this dual victim-responsible status is sometimes difficult to manage. This is why many companies insist on their victim status, not hesitating to specify that the attack was ” sophisticated “Or” on a large scale “without these assertions being supported by technical reality. The more they insist on their position as victim, the more they hope to hide their position as responsible, who may have made a gross error in his safety.
Two-speed leaks
The fact remains that the law, in particular the famous GDPR, forces companies to communicate. First, any security incident that affects personal data must be declared to the Cnil, the French data officer, within 72 hours of its discovery. This declaration can be supplemented subsequently with details drawn from the possible investigation.
Then, in the following 72 hours, if the risk represented by the leak for the persons concerned can be considered as ” Student ”, Then the company must individually notify each victim of the leak. This second step is however rarely necessary. In the case of Spliiit for example, the leak contains “only” email addresses, names and telephone numbers, which is insufficient information to meet the dangerousness criterion. These data are already available on the Yellow Pages or on social networks like LinkedIn, which expose them to everyone.
However, we cannot qualify them as useless or harmless: they can fuel phishing or spam campaigns, especially when they are collected in large numbers. However, they cannot cause immediate damage on their own, unlike bank details or passwords. In the Spliiit case, the hacker did not have access to the “safe”, the separate server that contains the customers ‘bank details, nor did he obtain the customers’ passwords. In the end, the startup managed to protect the essential.
The more transparent the companies, the less the customers will be at risk
Spliiit’s communication could have enabled some people who gave their bank information in the phishing not to lose money. For good reason: once the mistake has been made, a time trial begins. Slvsher planned to sell the CB data collected on a small online store. If victims do not realize that they have given their banking information, instead of entering it on the official site, buyers have the option of exploiting it to make purchases of tens or even hundreds of dollars.
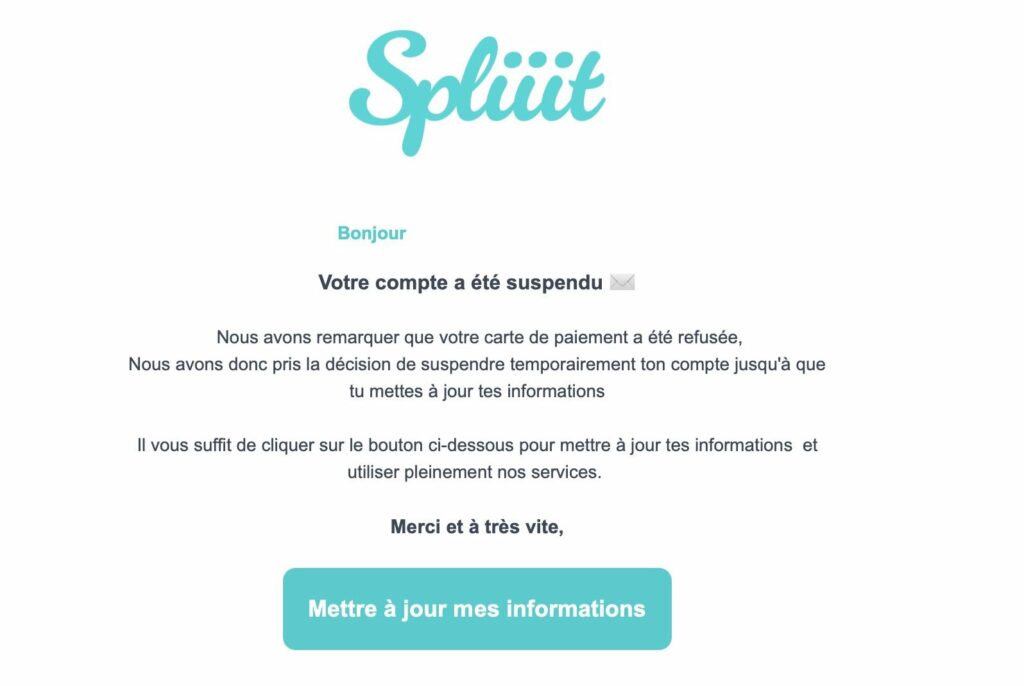
But thanks to the communication of Spliiit, it is likely that some of the victims had time to make opposition on their bank card, before suffering damage. ” We have also contacted our professional liability insurer, which is able to cover customers who have had their bank cards misused. », Adds Jonatahn Lalinec.
Likewise, if customers know that their email and phone are leaking, they will be more wary of any phishings they receive. In short: the more sincere and quicker companies are to communicate, the more individuals will be able to protect themselves on their own.
The more businesses communicate, the less risk other businesses will be
Spliiit does not just communicate on the consequences of the attack, she also explained to us how it took place. The incident stems from a misconfiguration of Laravel, as we suggested in our initial article on the incident: the Spliiit teams left the debugging tool open, and the hacker was able to use it. But the attack turns out to be a more complex variant, according to the CEO of the startup: “en looking, it turns out that the debug bar was present on staging [l’environnement de travail des développeurs, à différencier de l’environnement de production, celui observé par les clients, ndlr], which is on a secure address. We have therefore completely disabled staging in order to secure it. In other words, the attacker would not have been content to scan the production site to discover the flaw, as one might initially think.
A strange method
For his part, the hacker Slvsher loses his temper on Twitter, in a discussion with another user: ” This is my own vulnerability, I totally targeted the Spliiit site and I did not use any tools made by other people (…) I have developed my own scripts. In the jargon, the hacker claims to have a “0-day” flaw on Laravel, that is to say a flaw which does not yet have a patch, and therefore which makes any Laravel system vulnerable. ” These statements are not convincing. If a hacker discovers a Laravel 0day, he will use it to aim much bigger than Spliiit “, Estimates the expert Adrien Jeanneau, whom Cyberguerre consulted. Still, the method used by Slvsher is not as obvious as it seemed. Whatever the flaw used by the hacker, the information communicated by Spliiit could allow other companies to protect themselves from it.
For his part, Jonathan Lalinec says he is taking measures to ensure that an incident does not happen again: ” NOTWe will use Yes We Hack to test our services again. This French bug bounty service allows independent researchers to test the security of their site, and rewards them with a bonus depending on the type of flaw found.