In Linux operating systems we have many options to encrypt data in Linux, for example, we can use dm-crypt, LUKS, eCryptfs and even programs like Veracrypt that are really versatile and highly recommended. LUKS (Linux Unified Key Setup) allows us to encrypt disks, partitions and also logical volumes that we create on our computer. Some of the advantages that LUKS has over others is that its use is really simple, without having to configure or execute complicated commands, it is included in the kernel itself, therefore, the performance when encrypting / decrypting data will be very high, we must also take into account that we can manage the encryption key as we want.
We are going to divide this tutorial clearly into two sections, in the first section we will teach you how to install a Debian operating system with encryption throughout the partition, encrypted by default, and in the second section we will teach you how to encrypt the computer once Debian is installed normally , no encryption on the partition by default. A very important detail is that the partition oriented to the “boot” will not be encrypted, to allow reading the information, but the rest of the disk will be encrypted with LUKS, either partitions or logical volumes (LVM).
Install Debian or Linux with LUKS encryption by default
In the Debian installation wizard, either with the full graphical user interface, or with the installation wizard with minimal interface, we have the possibility to configure the entire disk with an encrypted LVM, with the aim of having maximum confidentiality when Let’s use the equipment, because all the data on the system partition and the data will be encrypted.
We will simply have to choose “Guided – Use the entire disk and configure encrypted LVM”, then we choose the disk, and select if we want everything in a partition or separate it by partitions, this does not matter because we can separate the / home partition in other.
It will indicate that, if we want to save all the changes made, it is highly recommended to use LVM to later expand or decrease its capacity. Once we have done it, the operating system will take care of erasing the entire disk with random data to improve security and prevent data recovery. This will take a while, depending on the size of the disk that we have selected.
Once it is finished, it will tell us to put the encryption password, to encrypt and decrypt the disk with this password. At least it is recommended to put 8 characters, but our recommendation is to put at least 12 characters, using a strong password. Once finished, we will get a summary of everything that the Debian installation wizard will do on our disk, the most important thing is the part of “sda5_scrypt encryption”, an important detail is that the / boot will not be encrypted, and neither the exchange (swap), therefore, we recommend that you never use any swap, or encrypt it afterwards.
Once we have seen everything that is going to be done, we indicate that we want to write the changes to the disk, and also install the boot loader in the grub, selecting the disk / dev / sda that we have.
Once we have finished the installation, the grub will come out, and we will choose the first option, or we let time pass. It will automatically ask us for the password to be able to start the operating system, if we do not enter the password directly, it will not be able to start, because everything is encrypted. If we enter the key, we will see how the different services start to start in Debian.
If we want to check the partitions that we have created, we can put the following command:
lsblk --fs
If we want to see the characteristics of LUKS (symmetric encryption algorithm used, key length etc), we can put the following command:
cryptsetup luksDump /dev/sda5
The / dev / sda5 is in our case, if you have done a different installation it is possible that this data will change. As you can see, LUKS encrypts all data with AES-XTS in its 512-bit version, uses a PBKDF argon2i, and a SHA256 hash.
As you have seen, configuring our operating system with Linux by default is really easy, we just need to follow the steps of the configuration wizard, without having to do anything else. Once we know how to encrypt all data by default, let’s see how to do it when the operating system is already installed.
Configure LUKS encryption on an already installed system without prior encryption
In this section of the tutorial we are going to see how we can encrypt partitions when they are already created, and even how we can encrypt any file with LUKS that we have in the operating system. We will perform these tests with a Debian 10 system without having anything encrypted by default, no system partition, data or anything.
The first thing we have to do is install LUKS in the operating system, because it is not installed by default if we have not used it in the installation wizard. Installation is done directly from the official Debian repository as follows:
sudo apt install cryptsetup
Once installed, we can use it to encrypt the content of hard drives, partitions or any removable storage device.
Before we start, always it is advisable to completely format the partition and rewrite the data, to have the best possible security, in this way, the entire partition or disk will be rewritten with random information, so that it is very difficult or almost impossible to recover information. Currently LUKS does not allow to encrypt the disk or partition when it is in use, therefore, we would have to do it from another computer. In addition, you have to make use of «cryptsetup-reencrypt»Which will help us to fully re-encrypt the partition, without loss of data, although it would be highly recommended that you make a backup copy of important files before doing so. This tool allows you to encrypt the data on the LUKS device insitu, but it is necessary that the partition is not in use.
Encrypt any disk or partition (with data loss)
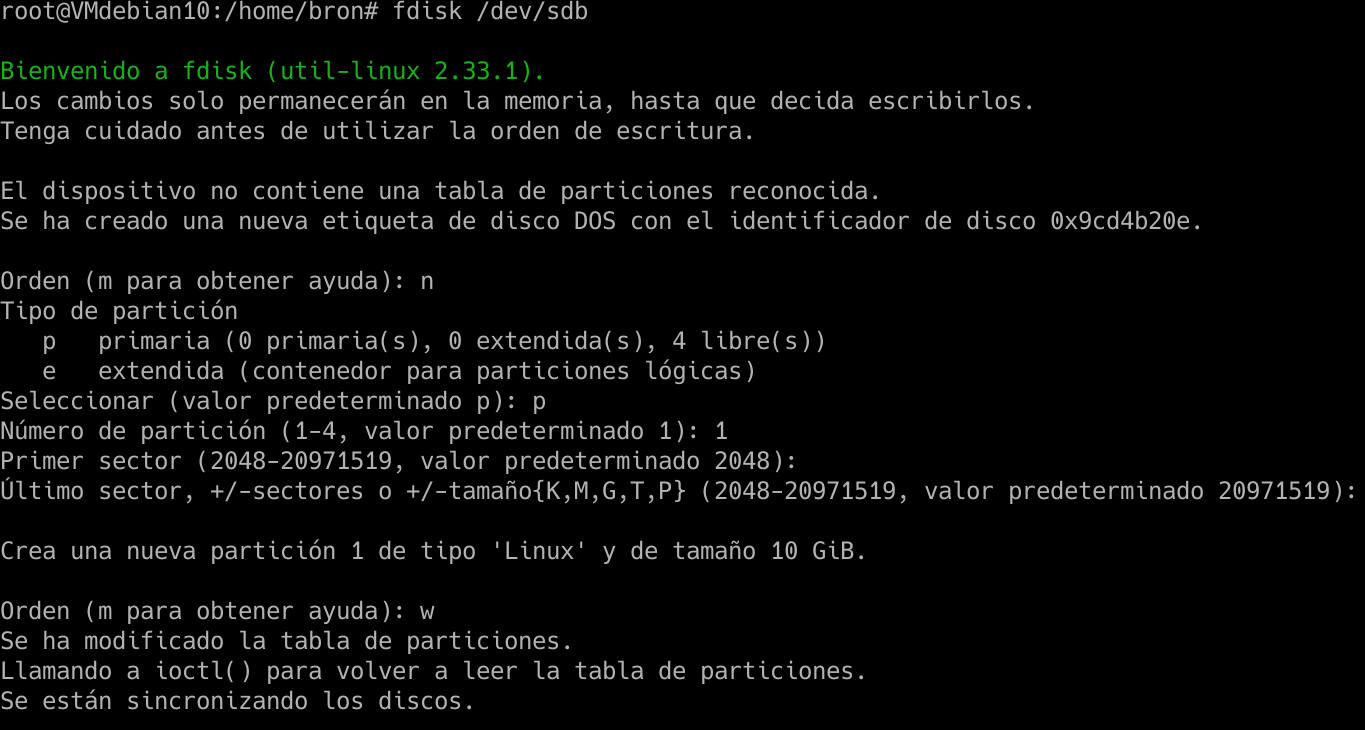
The first thing we have to do is create a new partition on the disk, to later use it. We execute the following command:
sudo fdisk /dev/sdb
And we continue putting “n” to create a new partition, we put “p” to make it primary, and we accept the values that indicate us to have a partition of the entire hard disk, if we want to make it smaller, we will have to modify the sectors for this partition in particular.
Once we have done this, we must put the newly created sdb1 partition with the LUKS format, for this we execute the following command:
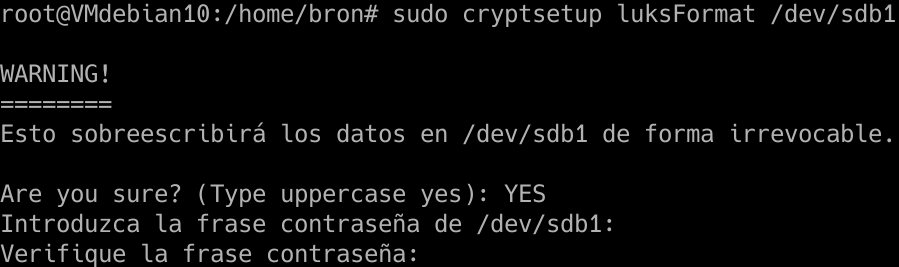
sudo cryptsetup luksFormat /dev/sdb1
We capitalize “YES”, enter the password we want, and wait until it is ready.
If we execute the command:
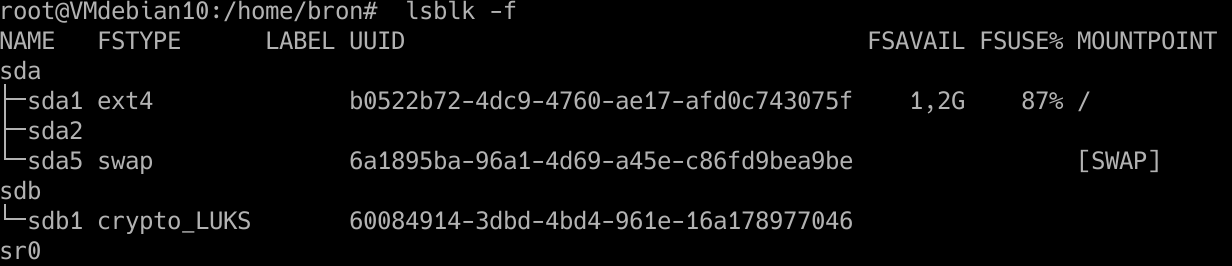
lsblk -f
We will be able to see all the hard drives, the partitions and the file system that we are using. We should see that on sdb1 we have “crypto_LUKS” as it appears here:
Once we have done it, we will have to open this partition with LUKS that we have just created, for this we put the command:
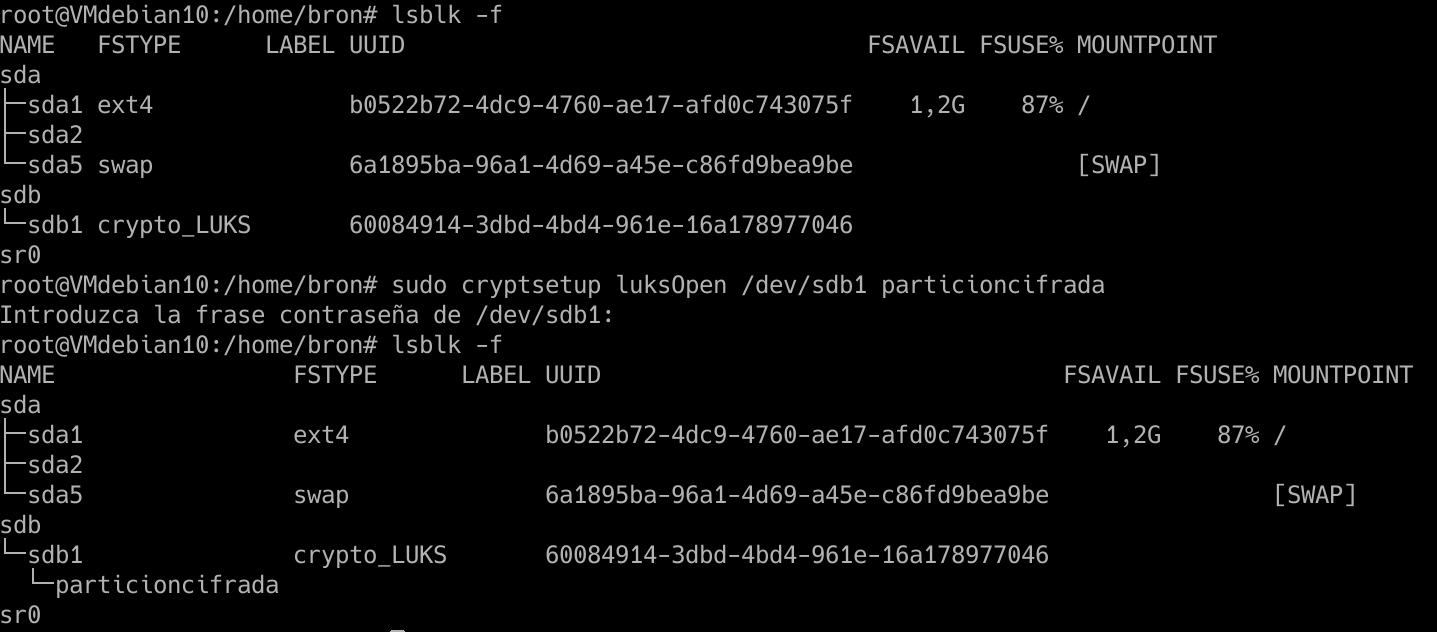
cryptsetup luksOpen /dev/sdb1 particioncifrada
We introduce the password, and then we re-execute the «lsblk -f» and «encrypted partition» will appear, which is the identifying name that we have given, but we can change it at any time.
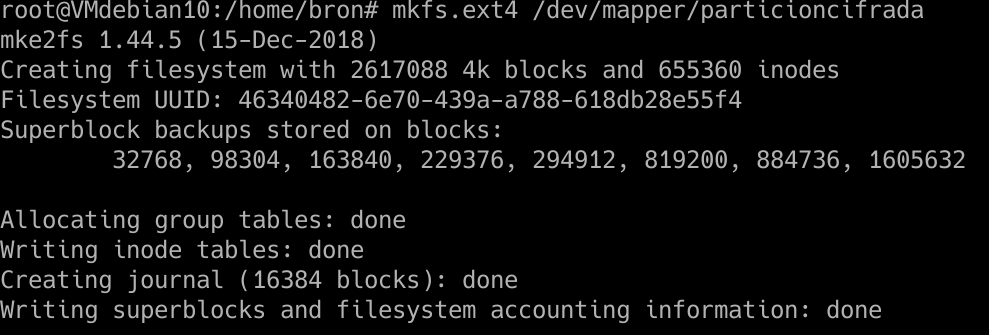
Now we have to give file format to this partition, the normal thing would be to do it with EXT4 as well, for this, we put the following command:
mkfs.ext4 /dev/mapper/particioncifrada
And we will already have the EXT4 file system on this encrypted partition.
Now we must mount the partition to a directory, to do so, we must create in / home or wherever we want the mount point:
mkdir -p /home/bron/particioncifrada/archivos
And now we have to mount it:
mount /dev/mapper/particioncifrada /home/bron/particioncifrada/archivos
And if we access the directory «/ home / bron / partition encryption / files» we can write all the data we want, the encryption is on the fly and totally transparent.
If we restart the computer, the unit will not be mounted, nor will we have the partition open with LUKS, therefore, every time we restart and want to access this partition, we will have to do the following:
cryptsetup luksOpen /dev/sdb1 particioncifrada
We enter the password when requested, and mount the unit again:
mount /dev/mapper/particioncifrada /home/bron/particioncifrada/archivos
If we want it to be opened and mounted automatically at the start of the operating system, we will have to edit the / etc / crypttab and / etc / fstab files to put this partition, but our recommendation is that you mount the unit manually and ask for the password, for security, because if not, you will have to store the key in plaintext in the / boot / partition.
Now we know everything we need to know to be able to encrypt entire disks or partitions using LUKS and doing it directly from Linux, even when the system is already running, we will have to be careful with our passwords, but we will be talking about a tremendously secure system with encryption of data.