The authors behind the EnemyBot botnet have been adding exploits for critical flaws in services like VMware and F5 BIG-IP, recently revealed in web servers, content management systems, Internet of Things devices and Android devices.
according to one AT&T Alien Labs reportthe latest variant of the malware incorporates exploits of 24 vulnerabilities — most of them critical — but some without the CVE identification number, which makes mitigation even more difficult for defense professionals.
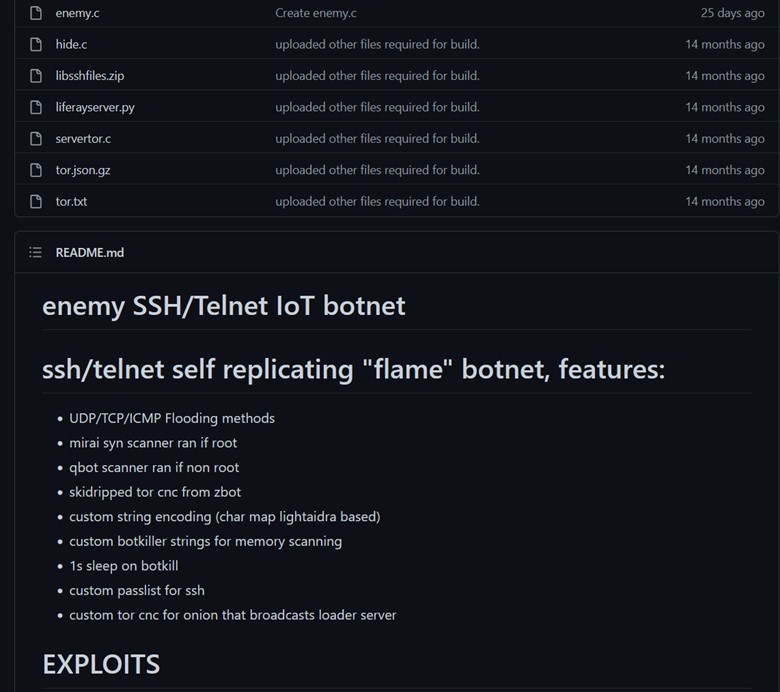
EnemyBot is a botnet that gathers source code from multiple pieces of malware — among them Mirai, Qbot, and Zbot — and its main purpose is distributed denial-of-service (DDoS) attacks as well as scanning new target devices to infect them, according to the malware repository on GitHub.
EnemyBot page on GitHub. Image: reproduction/GitHub
While the botnet’s discovery is relatively recent, analysis of new samples performed by Fortinet in Aprilso one month after the discovered by Securonixshowed that EnemyBot had integrated more than a dozen processor architecture flaws.
Additions of the new malware variant
In the month of EnemyBot’s discovery, most exploits attacked flaws related to routers and IoT devices. CVE-2022-27226 (iRZ) and CVE-2022-25075 (TOTOLINK) were among the most recent, with Log4Shell being one of the most notable.
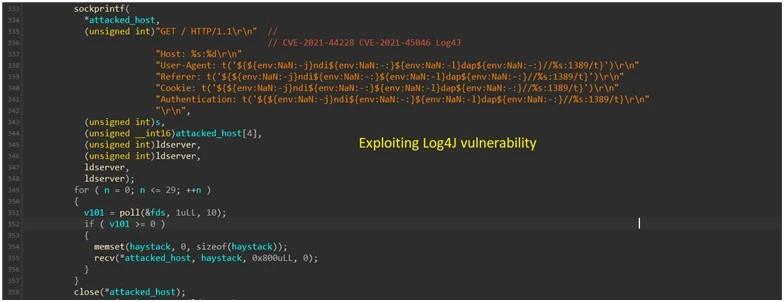
Exploiting the Log4J vulnerability. Image: AT&T Alien Labs
For the new variant, the group behind the threat included exploits for the following vulnerabilities:
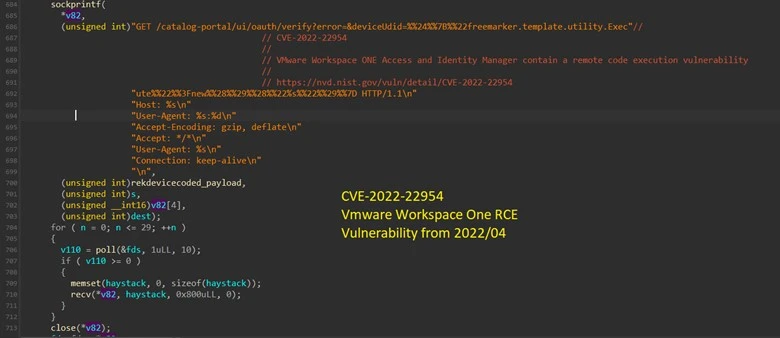
- CVE-2022-22954: Critical remote code execution failure (CVSS: 9.8) impacting VMware Workspace ONE Access and VMware Identity Manager. The PoC exploration (proof of concept) was made available in April 2022.
Exploiting the VMWare Workspace ONE vulnerability. Image: AT&T Alien Labs
- CVE-2022-22947: Spring remote code execution (Spring4Shell) crash, fixed as zero-day in March 2022, and mass targeted for the entire month of April 2022.
- CVE-2022-1388: Critical remote code execution failure (CVSS: 9.8) impacting F5 BIG-IP, threatening vulnerable endpoints with taking over the device. The first PoCs appeared in the wild in May 2022, and active exploration began almost immediately.
AT&T Alien Labs researchers also singled out the RSHELL command, used to create a reverse shell on the infected system, among the commands supported by the new version of the malware. In other words, RSHELL allows the author to bypass firewall restrictions and gain access to the compromised machine.
The added commands are in addition to those seen in the previous version, which offers a list of options for DDoS attacks.
Keksec: group behind EnemyBot
Reports show that Keksec, created in 2016, is made up of experienced actors in botnet development. In November 2021, researchers from Qihoo 360 described in detail the activities of Keksec, attributing to the group the development of botnets aimed at different platforms, such as Tsunami and Gafgyt (based on Linux), DarkIRC and DarkHTTP (based on Windows) and Necro , written in Python, aimed at both systems.
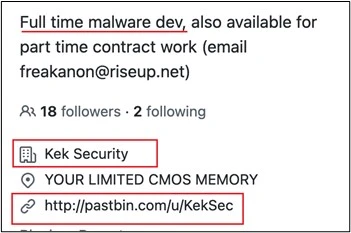
EnemyBot Developer Description. Image: AT&T Alien Labs
Also according to AT&T researchers, someone likely affiliated close to the group released the EnemyBot source code, making it accessible to anyone.
While authors pay particular attention to malware when adding exploits as vulnerabilities emerge, recommendations for protection still include applying updates as they become available, in addition to monitoring network traffic, including outbound connections.
Via BleepingComputer