First of all, it must be clarified that cryptocurrencies, despite being born from a consensus of use and being an indirect means for exchange, are not seen as legal tender. Since each country or group of countries reserves the exclusive right to issue its own currency and makes the compulsory payment of taxes to that currency subject to it. By doing this, they ensure that wages are paid only with the currency issued by the central bank and this allows them to control the flow of capital.
Due to the appearance of cryptocurrencies, two types of users have appeared. On the one hand, the people who generate these capitals to sell them, on the other hand, the people who acquire them. In the latter case, large amounts of legal capital flow into cryptocurrencies and not only the entire tax system suffers, but the entire economy in general. In addition, the anonymity in cryptocurrency transactions gives wings to illicit operations in theory. That is why Europe seeks to end cryptocurrencies by eliminating anonymity in transactions.
Europe on the hunt for cryptocurrencies, the measures they intend to adopt
A few days ago, the European Union proposed a new bill, which would apply to all member countries and which seeks the prohibition of anonymous digital wallets and fund transfers from them. On the grounds of protecting EU citizens and the financial system.
The bill is based on four different points:
- Establish a new EU agency against money laundering and terrorist financing.
- Implement new rules that affect the relationships between both parties in transactions.
- Update Directive 2015/849 of the European Union, in order to cover national supervision by members establishes
- New rules for institutions and financial intelligence units and amendments to the “Regulation on the monitoring of the transfer of cryptographic funds” of 2015.
The idea behind these measures is to end the anonymity of transfers, which will give member countries an inventory of capital movements to and from digital wallets. So if these laws are approved, the same rules as traditional bank transfers will apply. This includes information such as the sender’s name, the sender’s account number, the sender’s address, the personal identification number, the client’s identification or the date and place of birth, the name of the beneficiary and the personal account number of the beneficiary the place where the account is stored.
How does this affect the hardware?
Today the hardware of every PC has a series of back doors that security agencies can access, the most famous of which are the Intel Management Engine and the AMD Platform Security Processor. Which give remote access to your PC to both Intel and AMD, taking advantage of the fact that they acquire the highest possible level of privilege. And when we say access we mean total remote control.
With the arrival of Windows 11 and the need to place a TPM chip to be able to make it work and that stores the keys and user data. In the future, with regard to the administrations of each country, our computers with our data will be exposed to the public administrations regardless of the political color of the specific country. In this way, the different administrations may be remotely monitoring the use of each computer without the users knowing.
What’s more, operating systems can carry an activity monitor that indicates the processes and applications that are running on the PC at all times. From which the use of mining software can be induced. Thus, with a series of measures, Europe will be able to deduce that they are making use of cryptocurrencies, either as a miner or to trade with them.
If this sounds dystopian to you, I’ll just let go of one thing. Each of the CPUs that have been produced has a unique ID which is its serial code, which can be consulted with a simple instruction. Every Windows installation, even a pirated copy, has a code that is generated and sent to Microsoft who know if your copy is pirated or not. If we add to this what we have commented in the first paragraph about the TPM saving sensitive data, it is very clear that if these solutions are approved, our PCs will be even more monitored in their use.
And what about graphics cards?
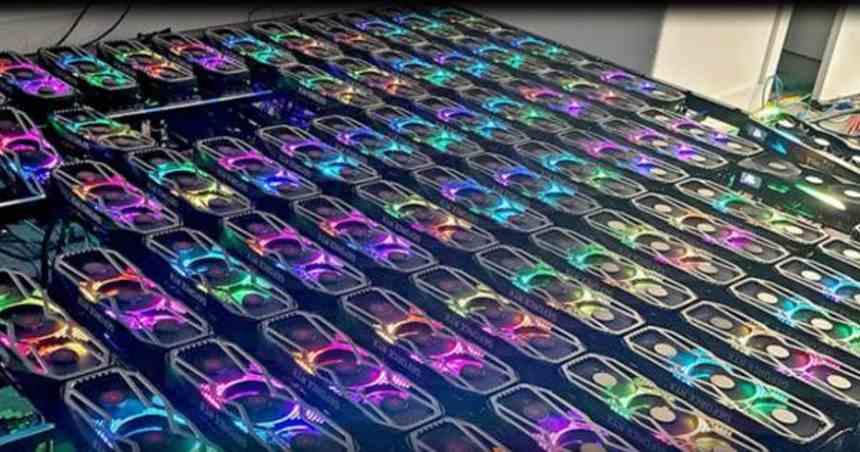
Graphics cards are the hardware used to mine a good part of the cryptocurrencies, although as the complexity of the algorithm grows, they are gradually being abandoned. Every cryptocurrency starts with being able to decode with a fraction of a CPU core to pass to the GPU and later to the mining ASICs. The evolution goes with the reduction of the energy cost per operation carried out by said processor.
When a cryptocurrency reaches the maximum popularity is when the mining of it through a graphics card begins to become popular. The demand for graphics hardware is growing and huge amounts of capital are going to buy this equipment to set up mining farms where these graphics are running all the time. For the moment companies like NVIDIA have limited the mining of certain cryptocurrencies in their RTX 30, but this is a game of cat and mouse and in the same way that hackers continually find new security flaws, the same happens with the creation of dozens of cryptocurrencies, where not all are successful.
The only way to be able to limit the use of GPUs for cryptocurrency mining has to do with blocking certain applications remotely, we have discussed how to do this in the previous section. Through the monitoring of user applications and subsequent remote blocking, as well as vetoing the use of the hardware or all its resources.