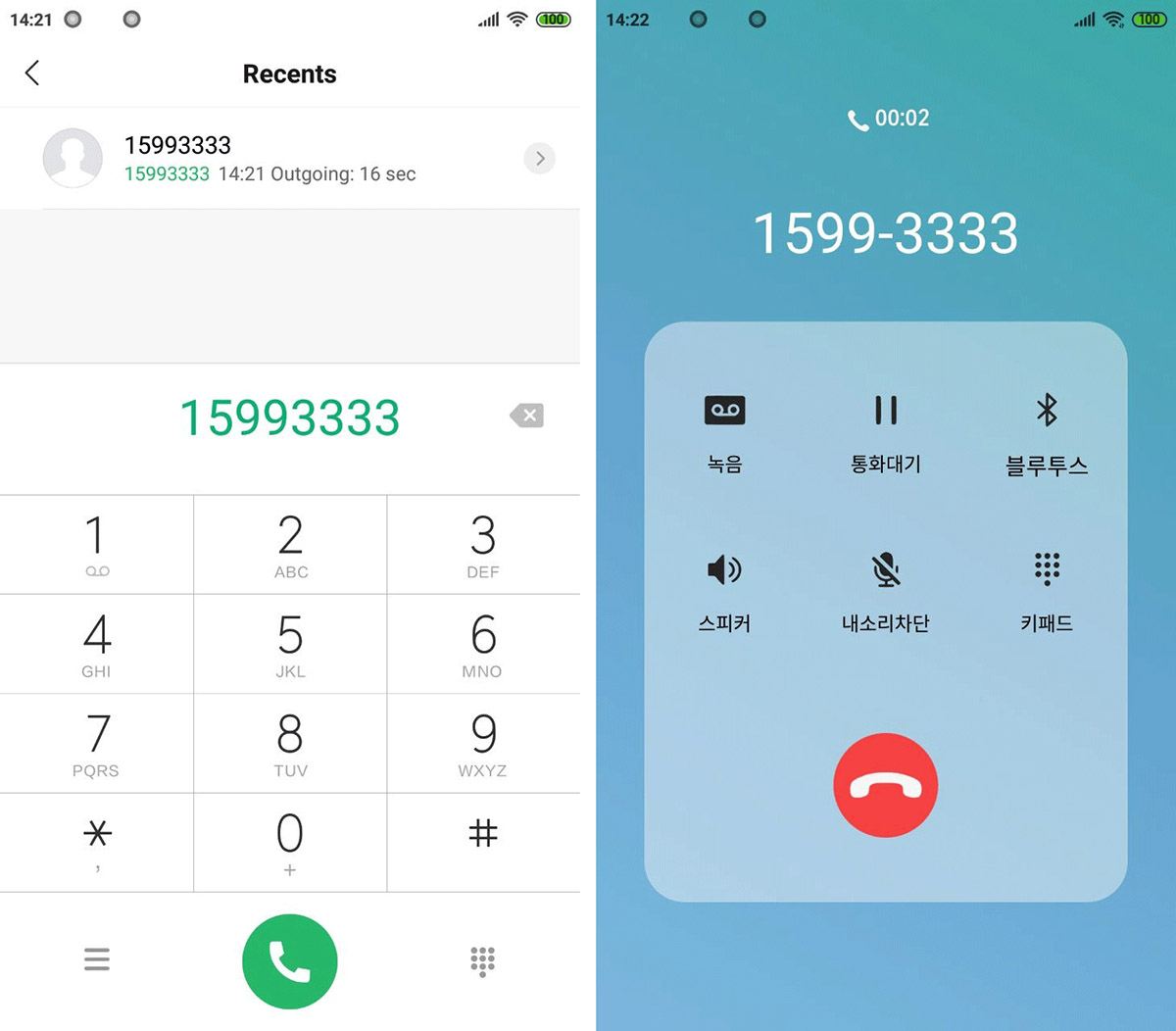
A malware that emerged last year is able to take over customer support calls from banks and connect the victim directly to the threat actors, according to a Kaspersky report. published this Monday (11).
Called Fakecalls by researchers, the Android banking trojan poses as a mobile app from popular financial institutions, with all branding, official logo and customer support number so as not to arouse suspicion.
With the app already installed, when calling the bank, the malware breaks the connection and displays the call screen, practically indistinguishable from the usual call screen.
Image: Kaspersky
On the screen, the victim sees the real bank number, but he is connected to the threat actors, who pose as bank attendants to obtain data that would provide access to the account.
To achieve this feat, the banking trojan asks, at the time of installation, for various permissions, such as access to the contact list, microphone, camera, geolocation and call management.
After installing the application and authorizing these permissions, the actors will have a set of tools to spy on the victim, with real-time audio and video streaming from the device, viewing the location, copying personal files (contacts, files such as photos and videos) ), and text message history.
“These permissions allow the malware to not only spy on the user, but to control their device to some extent, giving the Trojan the ability to keep incoming calls and delete them from the history. This allows actors, among other things, to block and hide real calls from banks,” the researchers explain.
According to the report, the trojan emerged in 2021 and has been identified in attacks on customers of popular South Korean banks such as KakaoBank and Kookmin Bank (KB).
Although it has been active for some time, the malware has received little attention – probably because its targets are geographically limited – which does not preclude other actors from reusing the fake call feature to develop new mobile banking threats.
In contact with threat actors
In addition to intercepting the call, Kaspersky researchers found that the malware can also play back a pre-recorded message, typically used by banks to serve customers looking for support.
Fakecalls code to play support call recording. Image: Kaspersky
Some short phrases commonly used during electronic attendance were recorded by malware developers. Examples collected by Kaspersky can be seen below.
Hello. Thanks for calling KakaoBank. Our call center is currently receiving a very high volume of calls. A consultant will speak with you as soon as possible. To improve the quality of service, your conversation will be recorded.
Welcome to Kookmin Bank. Your conversation will be recorded. Now let’s connect it to an operator.
In addition to spoofing calls made by the victim, the malware is also capable of doing the same process with calls received on the compromised device, with threat actors posing as the bank’s customer support service.
How to avoid malware
According to Kaspersky’s recommendations, downloading apps only from official stores can reduce the chances of getting infected; Pay attention to potentially dangerous permissions requested by the app (call access, texts, accessibility), especially if the app does not need them to function.

Image: Yuttanas/Shutterstock
In addition, researchers advise against sharing confidential information over the phone (login credentials, PIN, card security code, confirmation codes).
Via BleepingComputer



