Russia’s cyber attacks against Ukraine increased by 250% in 2022as revealed by a joint report by Google and Mandiant’s Threat Analysis Group (TAG), which puts us on the trail of the “other” war.
This week is fulfilled one year of the illegal and unjust invasion that has brought war to the gates of Europe. A war, terrible as all, with thousands of deaths and injuries on both sides, a humanitarian situation that has caused millions of displaced persons, a threat to the security of the planet and a huge problem for the recovery of the global economy after the crisis caused by the pandemic. And there are no signs that it may end anytime soon.
We already said a year ago that the wars of the 21st century are not only fought on the ground and cyberspace is another vital area. Russia has elements of cybernetic attack and defense that are cited among the planetary elite and coinciding with the first physical bombardments on Ukraine, we already learned of cybernetic attacks that had been prepared months before.
Russia’s cyber attacks against Ukraine, in data
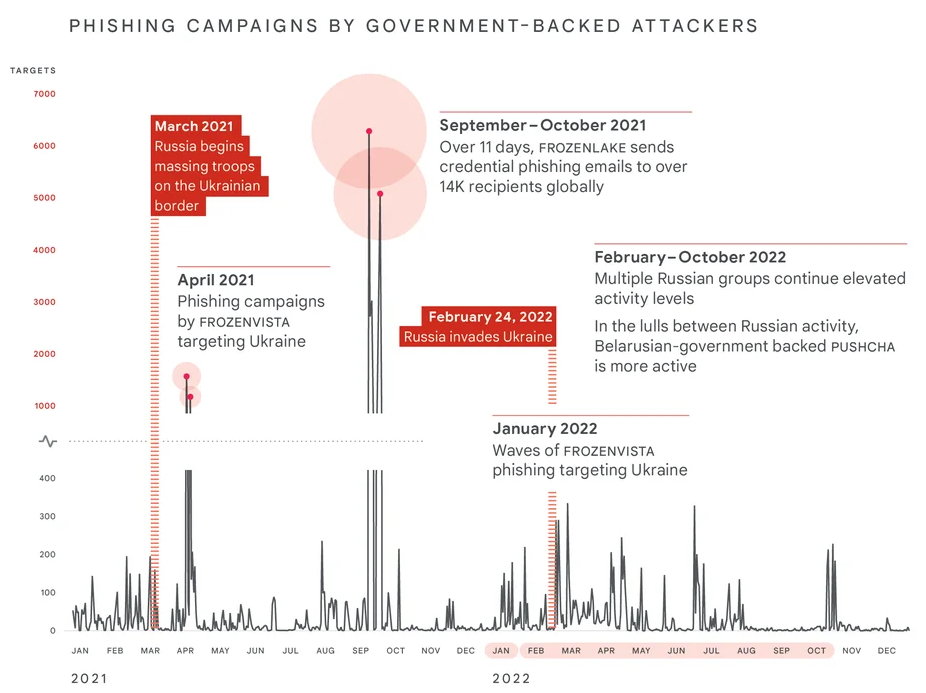
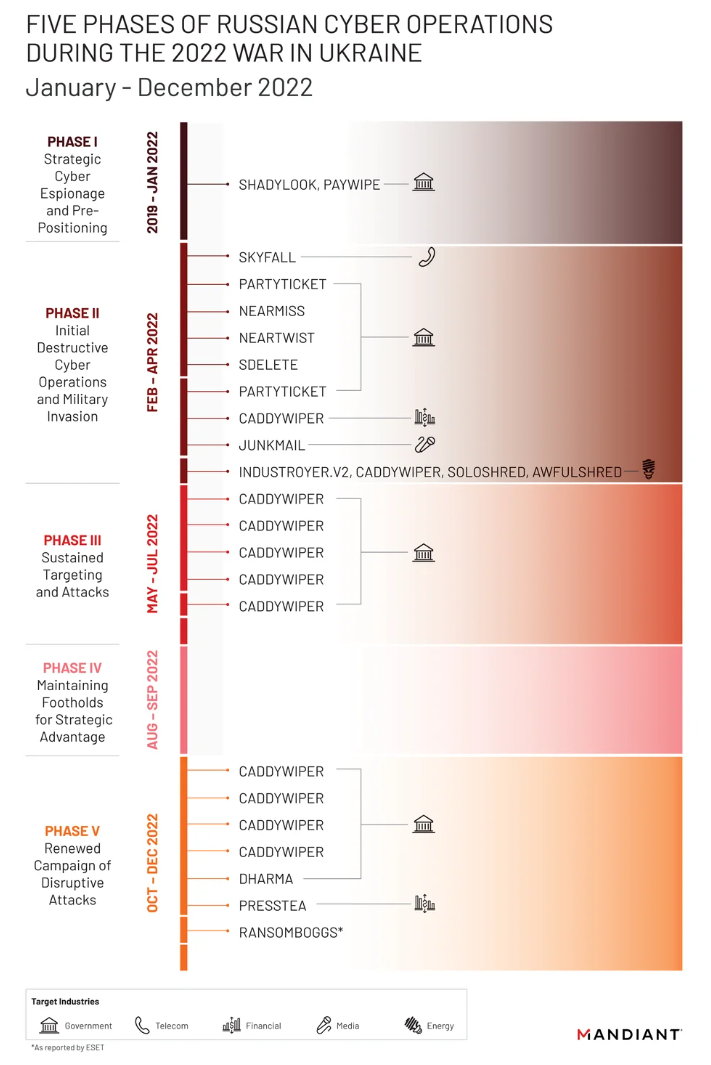
Now, Google puts figures on the table and they are, unfortunately, spectacular. Russia’s cyber attacks against Ukraine in the first four months of 2022 were more destructive than those produced in the last 8 years and largely focused on Ukraine’s government and military entities, along with the critical infrastructure, public services, and media sectors.
Google quotes up six attack groups against Ukrainian networksWhisperGate, HermeticWiper, IsaacWiper, CaddyWiper, Industroyer2 and SDelete) and well-known groups in security services, FROZENBARENTS (also known as Sandworm or Voodoo Bear), FROZENLAKE (also known as APT28 or Fancy Bear), COLDRIVER (also known as Callisto Group), FROZENVISTA (also known as DEV-0586 or UNC2589), and SUMMIT (also known as Turla or the Poison Bear).
Phishing attacks have also been detected targeting NATO countries, which experienced a 300% increase in 2022. These efforts were prompted by a Belarusian government-backed group called PUSHCHA (also known as Ghostwriter or UNC1151) that is aligned with Russia. “An aggressive, multi-pronged effort to gain a decisive wartime advantage in cyberspace, often with mixed results”the report states.
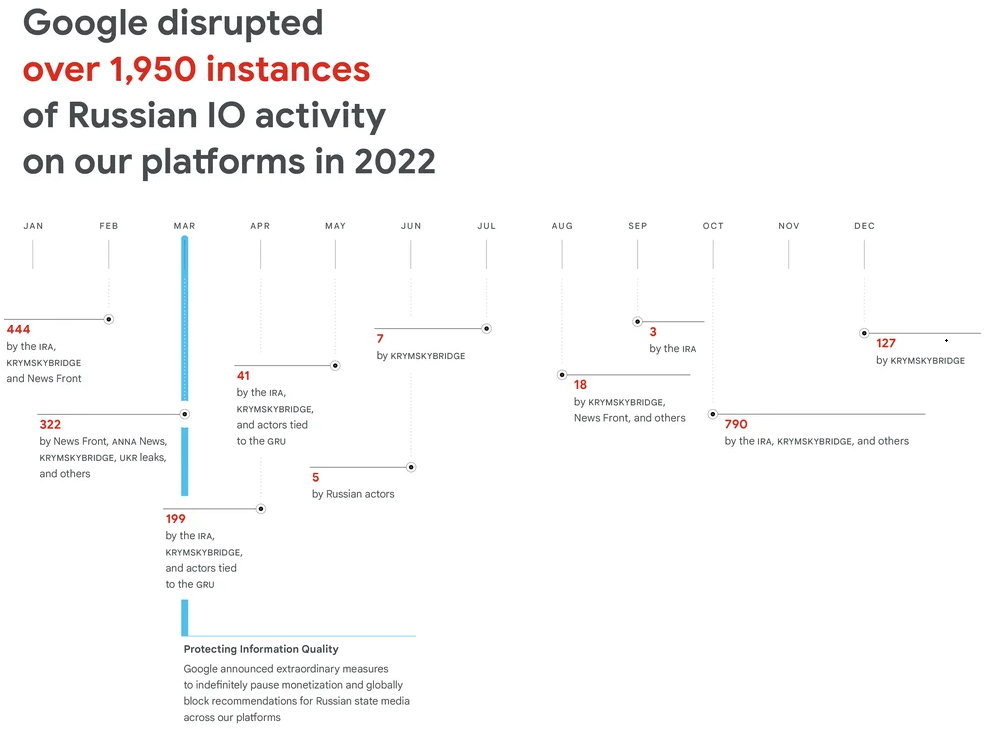
The increased intensity and frequency of operations aside, the invasion was also accompanied by the Kremlin’s involvement in covert intelligence operations designed to shape public perception with the aim of undermining the Ukrainian government, fracturing international support for Ukraine and maintaining domestic support for Russia.
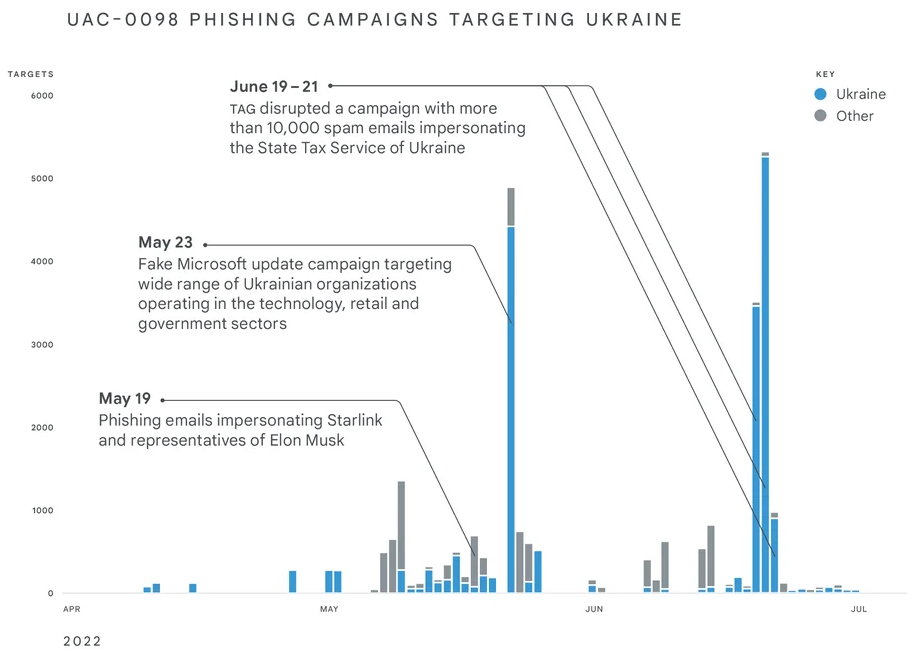
These activities confirm “a remarkable change in the Eastern European cybercrime ecosystem” in a way that blurs the lines between financially motivated actors and state-sponsored attackers. This is evidenced by the fact that one of the attacking groups, UAC-0098, author of the IcedID malware, has reused its techniques against Ukraine as part of a ransomware attack suite.
Putin has also “convinced” (under payment like the rest) other Chinese government-backed attack groups such as CURIOUS GORGE (aka UNC3742) and BASIN (aka Mustang Panda) to shift their focus towards Ukrainian and Western European targets for intelligence gathering.
The report is of interest to analysts and security services, and shows the sheer depth of Russia’s cyberattacks against Ukraine. The emergency is, of course, to help the Ukrainian people and their government to defend themselves against an invasion that has lasted for a year, but the digital fronts of the war are also very dangerous.