Keeping safe on the Internet is not an easy task in the midst of threats of all kinds of malware; software vulnerabilities; service violations and data leakage; fake and disinformation campaigns; a rampant loss of the right to privacy and all kinds of attacks with Ransomware and Phishing as exponents, as you could see in the selection of worst incidents of 2021.
And it is that the number of devices connected to the global network has grown exponentially, with everything that has come from mobility, home automation, smart cars or Internet of Things devices. If we add the pandemic and the transfer of millions of employees and students from professional networks to home networks (generally more insecure), we have a scenario that represents a challenge to stay safe from computer threats.
Strengthening Internet Security
All of the above requires the user a proactive behavior and a lot of common sense, understanding that virtual life must be protected today as much as physical life and that domestic tasks have been dangerously mixed with professional ones. Certainly, it does not matter everything we do, guaranteeing 100% security and privacy is not possible in a global network, but we can try it with a series of measures that we are going to remind you and that include the strengthening of online accounts , applications, equipment where we use them and the precautions due in the use of the Internet and its services.
1.- Protect browsers
All web browsers include advanced security features whose activation we must review and configure because they are the applications we use to access the Internet and its services. In addition to reviewing end-to-end encryption in sync or sandboxing (sandbox), we must pay attention to the warnings about unsafe sites displayed by browsers.
Also check the installed extensions because some are a frequent source of malware introduction. Another interesting possibility is to use a session in “Guest Mode” which is totally detached from the user’s original profile, including configuration or history. Finally, highlight the use of “Private Mode” (or incognito mode) to improve privacy, since it avoids tracking through cookies, open user sessions and other systems used for this purpose.
2.- Update the operating system and applications
Windows Update provides the latest updates to the Windows operating system, with security patches for known threats that must be installed. With automatic updates, there is no need to search for updates online or worry about the possible absence of critical fixes or device drivers for Windows on your computer.
As important -or more- than the above is the update of installed applications to the latest versions since these usually include security patches. When the versions are older, they have a greater risk of being attacked by cybercriminals who find vulnerabilities in the program, with special incidence in some widely distributed such as Java, Adobe Flash or Reader.
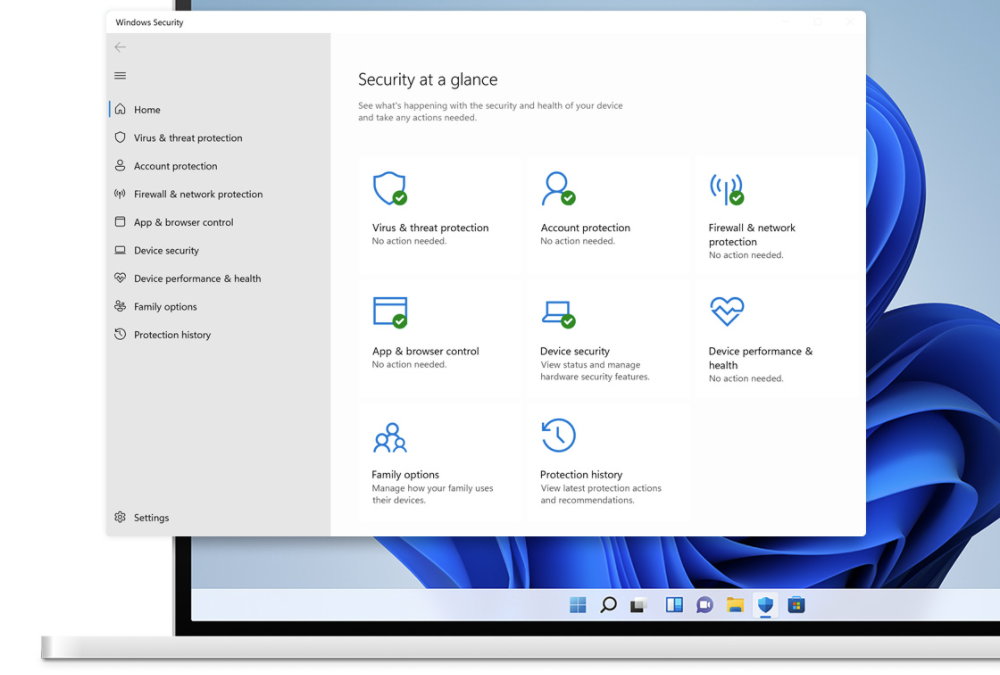
3.- Use security solutions
Microsoft offers Windows Defender in its operating systems as a native security solution and its use is mandatory in Windows as basic protection for a consumer, although different specialized providers offer a good number of security solutions, many of them free, that we can use. An advanced or professional user should consider using a comprehensive commercial security suite that includes other security tools such as a firewall and specialized tools against Ransomware, Phishing, adware or spyware attacks.
4.- Manage passwords well
Another of the golden rules to improve Internet security (in addition to using advanced biometric identification techniques if the device you use allows it) is to have a strong and different password for each website. Passwords are certainly an unattractive method for the user, but they are still the preferred authentication method for accessing Internet services or logging into operating systems, applications, games and all kinds of machines.
Strong passwords prevent brute force attacks, and using a different password for each account avoids having all of them compromised at once when a data breach occurs. You must follow a series of rules for their creation and value the use of password managers that are capable of doing the work for us, reducing human errors in their handling and automating the generation and administration process.
5.- Use two-factor authentication
2FA is an access control method that you will know as “two-factor authentication”, “double identification” or “two-step verification”, which has become one of the most important security mechanisms in the technology industry at the time to authenticate users and protect identities. Two-factor (or two-step) authentication provides an additional level of account security as it is not enough just to breach the username and password.
This feature is already available on most major Internet services and should be used whenever possible. Generally, it uses a verification code served through a mobile application or SMS, reinforcing the use of passwords, username and password when logging in.
6.- Evaluate the use of encryption
BitLocker Drive Encryption is a data protection feature of the operating system, available among others, in the Professional and Enterprise editions of Windows 10 and 11. BitLocker allows you to encrypt or “scramble” the data on your computer to keep it protected against threats such as data theft or exposure in the event of loss, theft or inappropriate removal of equipment, ultimately improving online security. BitLocker can be enabled on the operating system disk drive, on a fixed data disk drive, or on a removable data disk drive. There are equal or better third-party solutions whose use should be assessed.
7.- Use a hardware security key for vital accounts
For vital accounts, especially in professional and business environments, it is worth going the extra mile to protect them using a hardware security mechanism. Generally it is a device in pendrive format that connects to a USB port and contains a highly secure encryption engine. The entire process is done within the hardware, greatly increasing overall security versus software solutions.
8.- Avoid free wireless networks
The free access points have been spread over multiple areas in towns, restaurant areas, airports, train or metro stations, hotels and in all types of businesses. Darkhotel, the Advanced Persistent Threat (APT) discovered by Kaspersky Lab, confirmed the intrinsic insecurity of public wireless networks. It would have been active since 2007 and would have dedicated itself to obtaining inside information from executives and high-level employees staying in high-end hotels. Security researchers have shown that they are easily hackable so we should only use them for occasional browsing.
9.- Use backup copies
We already said that 100% security in a connected world simply does not exist and not only due to a virus since a hardware error can cause the loss of precious personal and / or professional information. Making backup copies (what we know as Backup) is therefore highly recommended for a user or professional who intends to protect personal and corporate information on a computer equipment. in addition to being a maintenance task that contributes to the health of the hardware. Backups must be stored on a storage device external to that of our team and / or in a cloud storage service.
10.- Common sense
As always when we talk about Internet security (and cybersecurity in general), prudence is a preferred barrier against malware and therefore, we must take special care in the section on downloading and installing applications from unsafe sites; when browsing certain Internet pages; in the opening of unsolicited emails or attachments; in those that arrive from social networks or messaging applications or in the use of operating systems and applications without updating, which contain vulnerabilities that can be exploited by cybercriminals for malware campaigns.