If we want to prevent it from being able to identify us not only when we browse the Internet but also when we use P2P networks, the simplest solution is to use Peerblock. Another option is to use VPN platformsanother excellent solution, however, these are paid, unlike Peerblock, which is completely free to use and download.
What is Peerblock
Windows incorporates a firewall, like all antivirus applications, a firewall that basically allows you to manage which applications have access to the Internet. It allows us to control the Internet access that the applications that we install on the computer can have. We can authorize or deny internet access to any application manually, so we can have full control over all the applications that we install on our computer to prevent unauthorized data leakage and that other people can access our computer. remotely.
Peerblock is a completely free and open source that analyzes our internet connection automatically blocking the IP addresses of the organizations that are in charge of monitoring, without any type of consent, internet connections to detect, mainly, what type of data is being downloaded and, where appropriate, take action legal. This application is responsible for controlling with whom our computer connects when we use the Internet.
How does it work
With Peerblock it helps us avoid servers dedicated to spying by filtering all those addresses through a blacklist of dangerous servers that are responsible for monitoring P2P networks. Companies dedicated to monitoring Internet activity regularly change their servers to try to be detected, so it is important to maintain the blacklists that the application manages, a process that we can do manually from the application or by downloading the most up-to-date lists.
In addition, we can also obtain access to lists of free IPs that Peerblock will use to manage connections securely, lists where there are no government servers, companies, or Internet providers, among others, that are dedicated to tracking our activity on the Internet. We can download the lists from the I-BlockList website.
Although most are free, we can also find other paid ones, mainly those that may interest us the most, such as those from companies such as Amazon, Facebook, CloudFlare, those of the United States government in its fight against piracy, pornography, trackers usually. Fortunately, the price to enjoy the complete service is very cheap, since it has a cost of $9.9 per year.
Once we have downloaded the lists, we must add them to Peerblock from the configuration options, a process that we will show you later in this article.
Where to download and install Peerblock
Peerblock, as we have mentioned above, is a completely free application that we can download directly from its website, by clicking on the Download button. The installation of the application does not have any mystery, since it is the same as any other application, where we must select the installation path, the name of the icon that will show the application in the start menu and if we want the application to run every time Let’s start our team.
Starting the application every time we log into our computer will allow us to be protected at all times while we connect to the Internet, regardless of whether we use P2P networks or not, so it is recommended not to start Peerblock when starting the computer unless we want to extend the time required by the computer to start up and be ready for use. Unless we are using a computer solely to download content from P2P networks, it is not necessary to run the application every time we log in.
Configure the app
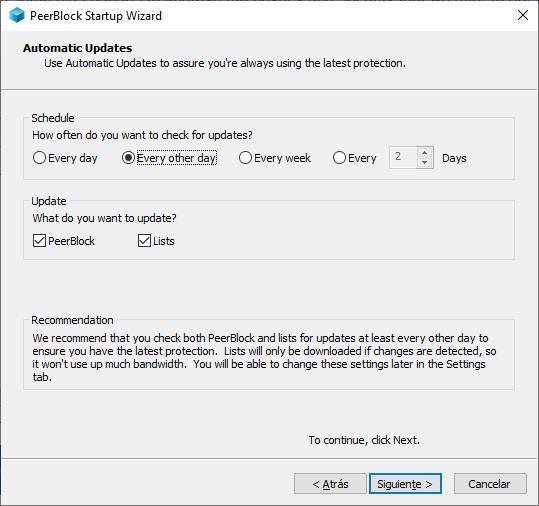
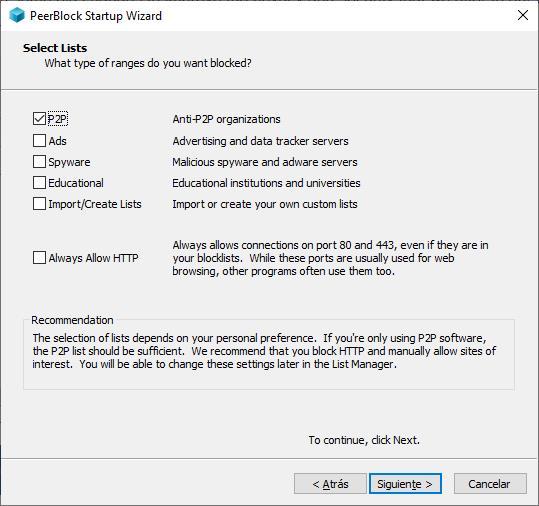
As soon as the application is installed, the first time we log in, a wizard will be displayed that will allow us to configure the operation of the application. The first window of the wizard invites us to establish what type of connections we want to block
- P2P. Activating this box will prevent organizations and companies that monitor P2P activity on the Internet from knowing what we are downloading at all times.
- ads. This option prevents ad networks from knowing about the searches we do on the internet and thus being able to target their advertising.
- spyware. Filters all IP addresses of servers where content related to malware, spyware, adware and others is stored.
- Education. This will almost prevent educational organizations from collecting information about our internet activity.
- Always Allow HTTP. If we activate this box, we will be protected from the servers that monitor our activity on P2P networks without affecting Internet browsing. It is only recommended to activate this box when we are going to use a computer only as a download center.
In the next configuration window, we must establish how often we want the application to check if there are any updates from our application or from the lists that are included by default in the application. Regardless of whether we are going to use this application regularly or sporadically, establishing the update period every week, both for possible updates and for lists, is more than enough.
Finally, click on next and the application will automatically open. As soon as it is opened, it will look for the most updated lists at that moment to download them and start using them to filter the IP addresses that can monitor our activity.
Once we have configured the application with the initial wizard, we do not need to interact with the application again, just open it and keep it running in the background, unless we need to add new server lists, available through IBlockList, if we want to stop the operation of the application or modify some aesthetic parameter of the application, or to enter the data of the subscription to IBlockList so that the application obtains the data of the paid lists automatically.
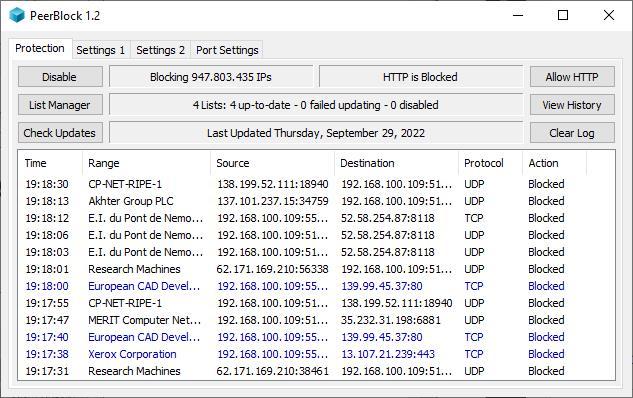
The main screen of the application is made up of 4 tabs: Protection, Settings 1, Settings 2 and Port Settings.
Protection
This tab shows us information about all the servers that are being blocked by the application to prevent them from monitoring our internet activity. In addition, from this tab, we can temporarily stop the operation of the application by clicking on the Disable button, allow monitoring via HTTP, manage the lists used by the application, view the log history, check for updates and clean the log that is displayed.
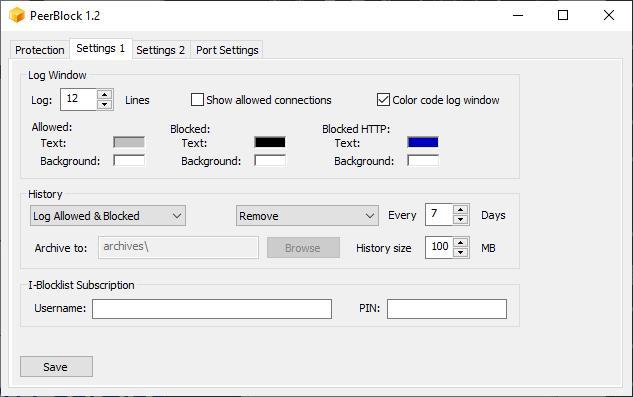
Settings 1
Within this tab, we can modify the log lines that the Protection tab shows, show only allowed connections, modify the color of the text that the log shows, delete the log history or archive it on our computer. This tab is where we must add the subscription data and finally we choose to pay to enjoy the most complete lists available through IBlockList.
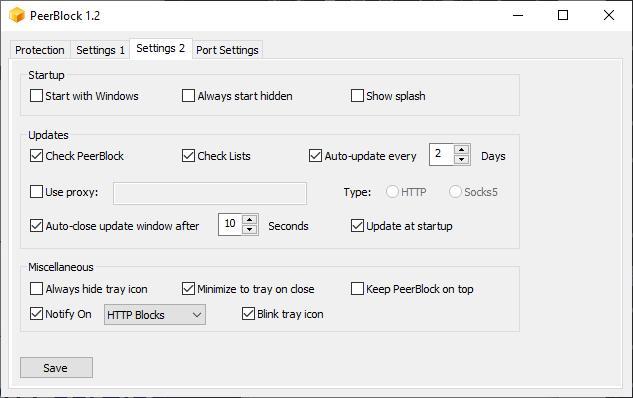
Settings 2
The Settings 2 tab allows us to configure the application to start with Windows, to start in the background and hide, modify the operation of the application to check for new updates of the available lists and the application, configure the application if we use a proxy among other options.
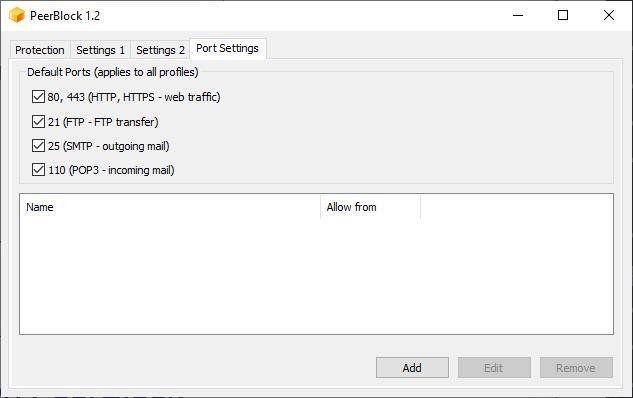
Port Settings
From this tab, we can establish which ports our device can use to accept incoming and outgoing connections, whether they are HTTP, FTP or email connections via SMTP and POP3.
Worth?
If we regularly use P2P networks and do not want any company or government to be able to monitor our activity on this type of network and know what content we download, the solution offered by Peerblock is ideal, as long as we pay the necessary subscription to be able to access the complete and updated lists through IBlockList. If we do not pay for this subscription, it does not mean that we are exposing our data using P2P networks, but rather that we are going to be less secure, but much more secure than if we do not use any application to protect our browsing.
In addition, it is a completely free application, so, regardless of whether or not we pay the annual subscription (remember that it has a price of 9.9 dollars per year), it will always be a better option than using a VPN, which is probably the best way to protect our Internet browsing, both when downloading content from P2P networks and when browsing without leaving any type of trace on the Internet.
Alternatives to Peerblock
As I mentioned above, the best alternative to Peerblock is a VPN network, however, we can also choose one of the following alternatives.
- BeeThink IP Blocker. With this application we can block access to our computer from certain IPs or IP ranges. BeeThink IP Blocker is a paid application that we can try for free from its website.
- SimpleWall. SimpleWall is an open source application that allows us to filter connections to our computer and monitor the activity of our computer on our network. It is compatible from Windows Vista and we can download it from here.