In the past time, TrueCrypt was among the most popular encryption software, that was discounted long ago. The developers of TrueCrypt could not be continuing this product line, which means no more updates, bug fixes, or any guarantee were provided after that. So, we have prepared this list of best TrueCrypt alternatives that work in 2020 and you can use them for encryption purposes.
Any users who enjoyed or relied upon TrueCrypt will be keen to find an alternative. There are a number of products available that fulfill a similar function, each with a few pros and cons depending on what application you need it for. This quick guide will take you through the most useful TrueCrypt Alternatives.
Why use an encryption service?
For users who are finding out about TrueCrypt after the fact, let’s give you a run-down of why these products are valued and what they’re used for. Encryption alters the format of data as it is sent between devices and networks. High-end encryption is used automatically by account-management software like Google as it shares your personal information across your network of private devices. Your home or work Wi-Fi might also have encryption to prevent anyone from being able to hack in and gain access to your shared files or Internet usage history.
Third-party encryption software like TrueCrypt is frequently used to scramble the data contained in emails and text messages so that once deleted off your phone they cannot be retrieved in any sort of readable way. Business and government agents dealing with sensitive data often encrypt everything inward and outward bound as a matter of course, and the technology is increasingly being used by the counter culture, too. Activists can employ an encryption service or app to make sure that the event details they’re distributing cannot be traced back to them or be used to incriminate anyone on the receiving end.
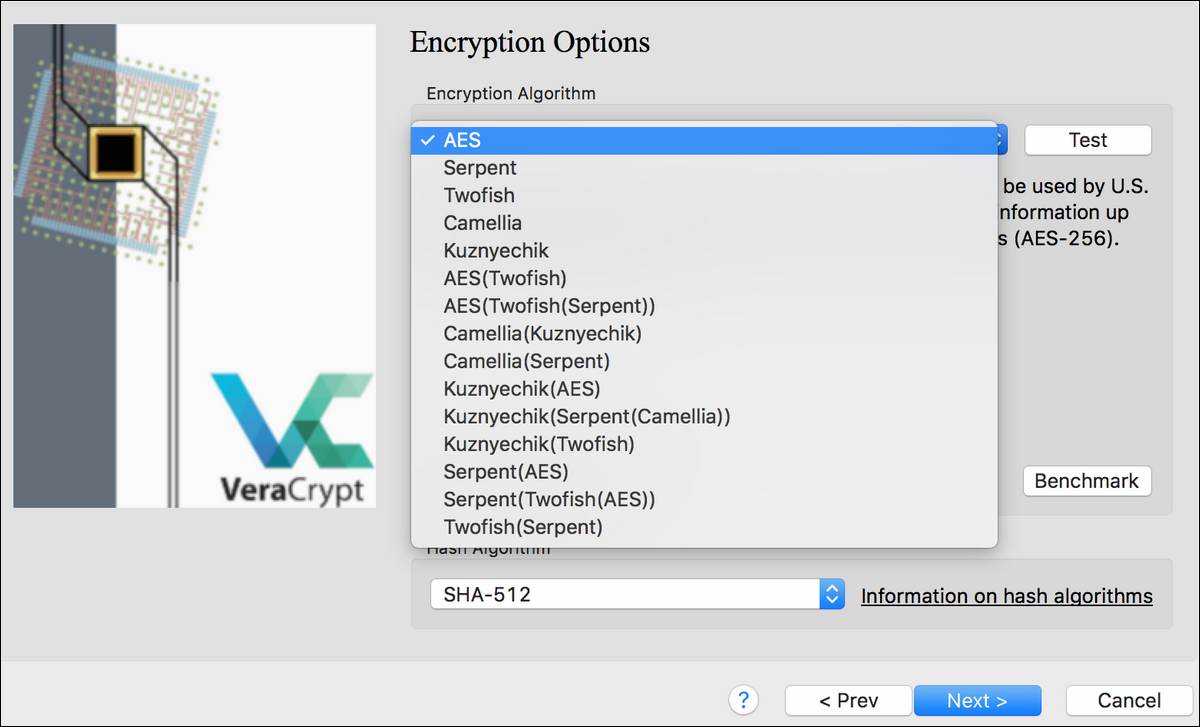
1. VeraCrypt
VeraCrypt is free disk encryption software based on TrueCrypt and published by IDRIX. VeraCrypt increases the security of algorithms used for system and partition encryptions, making it far less susceptible to new dangers from brute-force attacks. VeraCrypt also claims to have solved many of the susceptibilities and security flaws present in the original TrueCrypt upon which it is based.
The improved security will add minor delays when opening your encrypted partitions, but this doesn’t translate to a performance impact or a longer time taken for you to apply the encryption software in the first place. The mount and boot is supposed to be even faster since the release of 1.17
VeraCrypt now offers customer iterations via its PIM feature, and it can even load TrueCrypt volume. You can use it to convert TrueCrypt containers as well as non-system partitions to the VeraCrypt format.
Available for MACOSX 10.6 and above as well as Linux.
Also see:
- Best M4uFree Alternatives
- Best Working Alternatives to KickassTorrents
- Best Pirate Bay Alternatives That Work in 2020
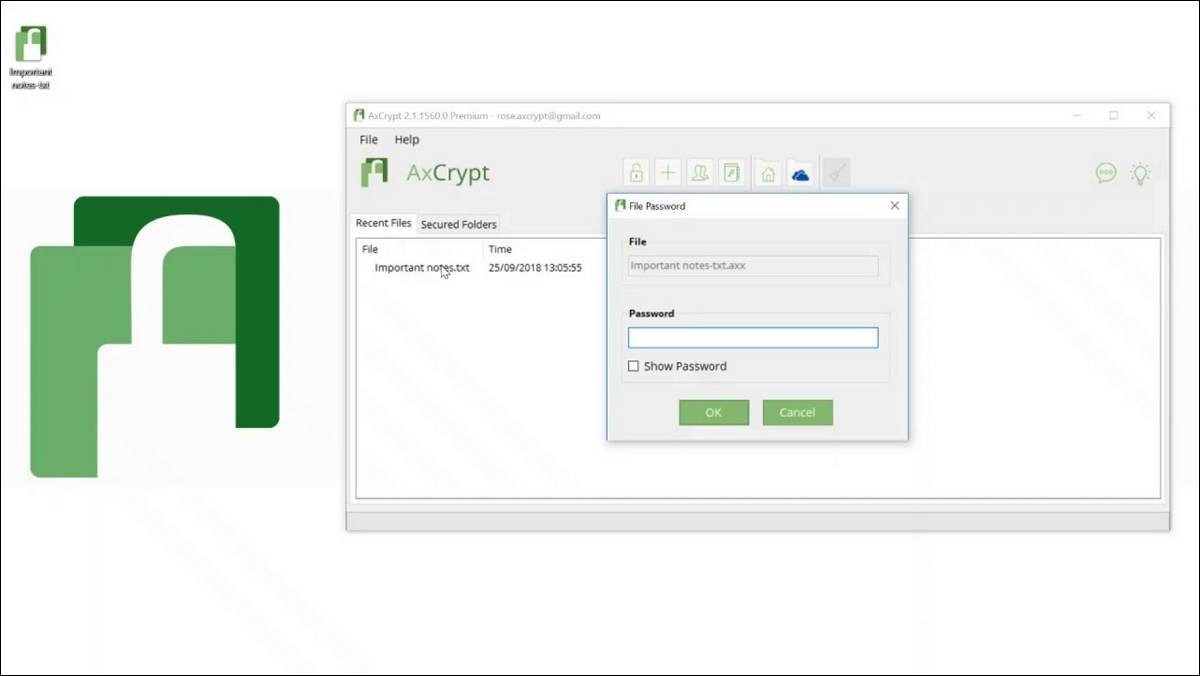
2. AxCrypt
Unlike TrueCrypt, which worked by creating virtual encrypted drives, AxCrypt encrypts individual files. So if you’re planning to encrypt multiple files, be prepared to access them one at a time, or you’ll have to add them to a zip file which you can then encrypt. This should work very well for you if you’ve got lots of content but only a handful of your files are confidential.
The con for AxCrypt is that according to a test run last year it wasn’t completely free of malware. Part of the reason for this is that AxCrypt receives some of its revenue by prompting your device to install other programs at the same time as you install AxCrypt.
You can easily avoid this pitfall by choosing to download the Portable version of AxCrypt.
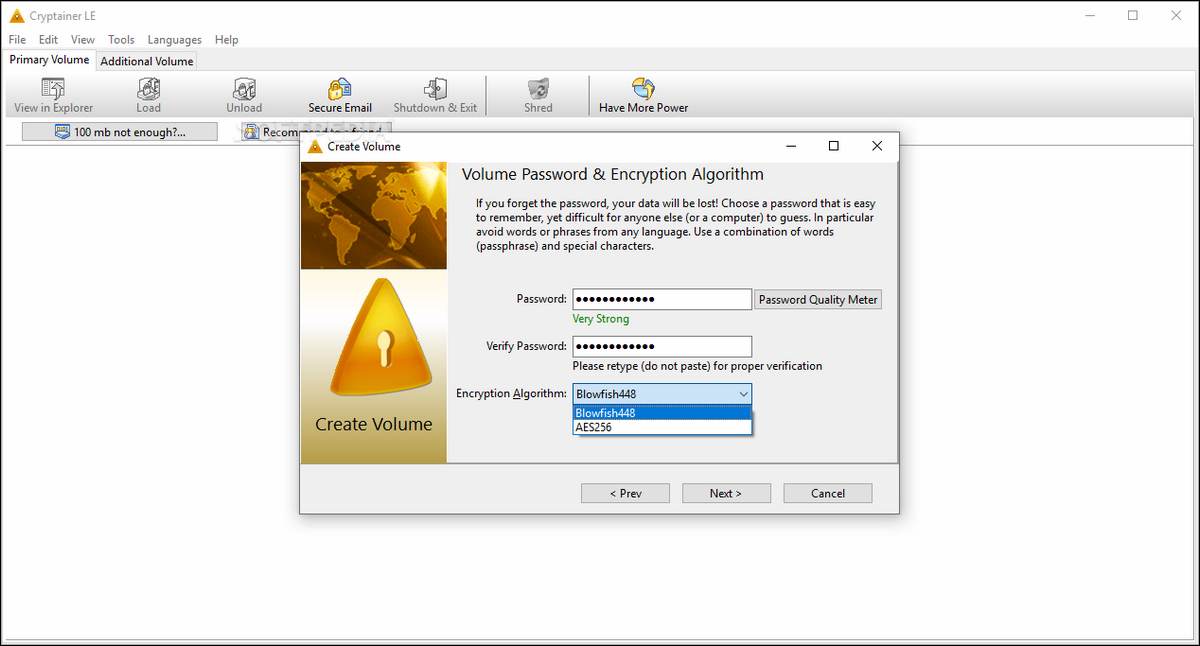
3. Cryptainer
Cryptainer is another free encryption software provider, designed to allow you to protect sensitive and confidential data on your Windows PC desktop, laptop or removable storage system. Cryptainer uses powerful 448-bit encryption to create multiple 100 MB encrypted vaults on your hard disk. It’s easy to view, modify or make invisible any type of file with a single password.
Cryptainer has come up at the top of several lists of FREE encryption services. It’s stable, fairly easy to use, and can be easily installed directly onto a USB drive as a standalone install. You can then use Cryptainer on a host of different machines without having to install Cryptainer on each of them.
The only major con for Cryptainer seems to be that it’s currently only available for Windows operating systems. Review more details of Cryptainer or download via cypherix.com.
4. BoxCryptor
BoxCryptor is the best option for anyone who needs easy-to-use encryption software that’s optimized for the cloud. BoxCryptor enables you to use state of the art cloud storage services without sacrificing security comfort. Like VeraCrypt and AxCrypt, BoxCryptor is totally free to download.
BoxCryptor currently supports all the major cloud storage providers, including Google Drive, Microsoft OneDrive, DropBox, and SugarSync, as well as any of the smaller services that use the WebDAV standard. Once BoxCryptor is successfully installed, all your files will be automatically encrypted from the moment you sent them or sync them to your could storage provider. BoxCryptor employs AES-256 and RSA encryption algorithms.
Also see:
5. Symantec Disk Encryption
Symantec Disk or Drive Encryption has licensed encryption software aimed at businesses. You can start a free trial but continuing use of the encryption service will require you to pay an annual fee, starting at about $75 per year for small businesses, and going up into the thousands depending on how many computers and networks the software is going to handle.
Symantec claims to offer intuitive and simple administration through a transparent user interface, to support regulatory compliance as well as meeting your customers’ needs for data security, and to reduce the risk of data loss during the encryption process.
Symantec is capable of encrypting your desktops, laptops, USB connected drives, and devices. It will auto-generate a privacy policy and agreement with your customers, and also offers to create detailed or executive summary reports and system use logs in the event of an audit. The service will encrypt automatically in the background without affecting usability of your devices.