The so-called data centers or data centers are not usually found in homes, but in companies that handle a large amount of data and need it for their daily work. So there is one in your bank, possibly in the hospital next to your house and even in large companies in each sector.
So protecting data is not only important, but also remote operation, as many of them give multiple users access to their content and performance. They do this in virtual machines that run remotely on the server, which helps keep the data on the server secure. Although let’s not forget that this means that a series of security measures have to be implemented at the server level.
Doing it at the software level is much less efficient than doing it in terms of hardware, and this is where we enter AMD’s solution for its EPYC CPUs, the so-called Infinity Guard, which is really based on the use of certain hardware technologies. Let’s see, therefore, what it is based on and how it works.
What is AMD Infinity Guard?
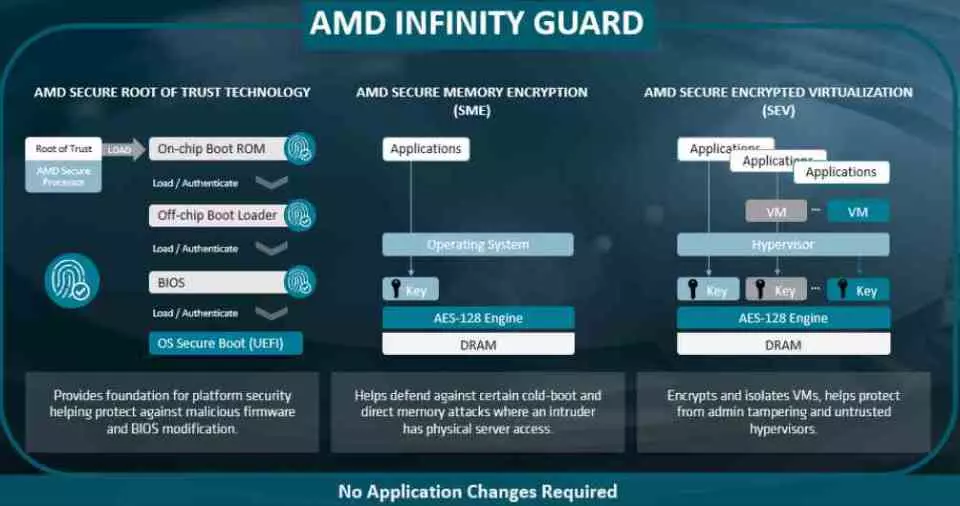
To begin with, we must clarify that it is not a piece of software related to any exclusive function of the processor. Nor is it a specific piece of hardware that receives such a name. Rather Infinity Guard is based on a series of modifications to existing elements of the CPU in order to enhance the security and integrity of the data on the server.
AMD EPYC CPUs are based on two elements within the processor, the first is the AMD Secure Processor which is located within the Northbridge or SDF of the processor. This microcontroller is the piece of hardware with the highest privilege level of all the components of the unit when it comes to accessing both RAM and peripherals and is responsible, among other things, for providing data encryption, generation of passwords and their management.
The second element is a data encryption system in AES-128 format that is located in the memory controller or IMC, which is responsible for encrypting and decrypting the data when it is provided with the necessary key. There are up to 8 encryption and decryption codecs in total, one for each memory channel used by the processor. This change is not small, since if it were done directly from the CPU it would not only be less secure, but it would also require the power of several cores, let’s not forget that we are talking about tens of encrypted gigabytes per second in terms of bandwidth.
These changes are exclusive to AMD’s range of server and data center processors and can’t be found in its Ryzen laptop and desktop processors or Threadripper workstation processors.
How does it work?
The AMD Secure Processor of the EPYC CPUs executes a series of security measures in order to guarantee the security of the data and not hand over control of the datacenter to a virtual machine that is running with malicious intent. In combination with the memory controller and AES-128 encryption, it always executes the following measures transparently to both the operating system and applications.
- When the system is started internally, it generates a key for private use, which is generated in the Secure Processor and transmitted to the memory controller so that it encrypts all the information in the system. This is done without any involvement of the operating system and completely transparent to it.
- Each virtual machine running on the server not only runs in isolation, but has its own key. Thus, the data that each one of them handles can only be those encrypted with its key. This prevents them from accessing the hypervisor’s memory space, which would be counterproductive to security.
- When a virtual machine is closed on a server with an AMD EPYC CPU, what it does is encrypt the information in the CPU registers and from the Secure Processor it executes a check of their status to verify that an illegal operation has not been carried out.
In addition, the memory controller keeps track of all the physical addresses that have been accessed by the different virtual machines on the server. This gives it strength against so-called Return-Oriented Programming type attacks. These are extremely common in environments where access to RAM is closely guarded and guarded.
Transparent to the operating system
The AMD EPYC Infinity Guard, by working completely transparently and performing all its functions at the hardware level, does not require the operating system to do anything, what’s more, the Secure Processor and the integrated memory controller work hand in hand to that the central processor does not even have to intervene in the different Infinity Guard processes.
So regardless of whether the server uses GNU/Linux, Windows or even some flavor of Unix BSD as the operating system the Infinity Guard will always be running. In the same way, you also don’t need to use the apps to benefit from it. Of course, it is necessary to activate it in the BIOS of the server for it to work, since it is not activated by default.
In conclusion, it is a series of security measures at the hardware level that AMD implements in its AMD EPYC CPUs and that have been designed for the highest possible security in a data center. Which is a point that is not important for a conventional PC user, but at a business and state level where totally sensitive data is handled.