For some time now, computer motherboards have included a security chip, called TPM, which is responsible for reinforcing the security of the system, specifically for managing all sensitive data and system cryptographic keys. This chip has always gone unnoticed until, with the arrival of Windows 11, it became a mandatory requirement to be able to use the new Microsoft system. Although its purpose is to help us protect the computer, in reality, right now it is doing the opposite.
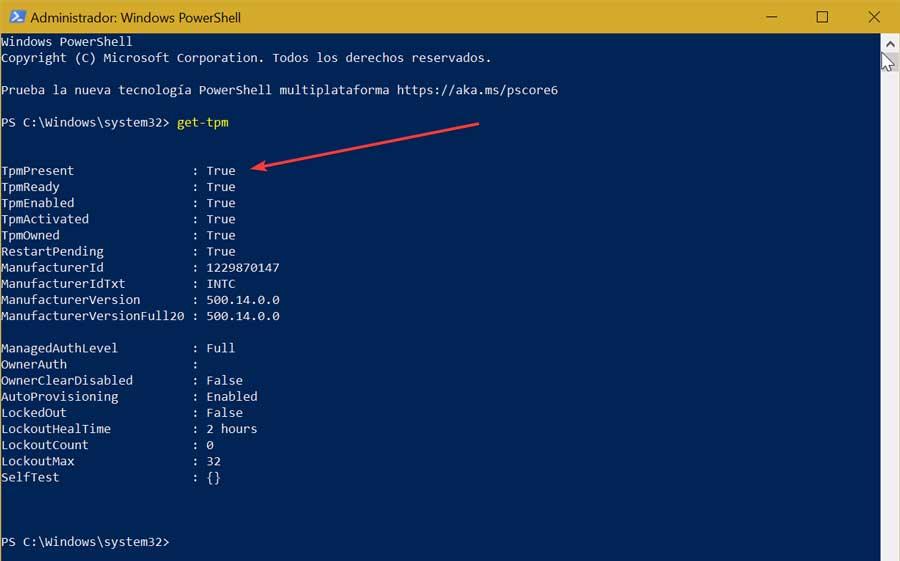
He dwt It is not a program or a configuration as such that we can have in the system, but a hardware chip that is soldered to the motherboard and that is necessary for the system to work. Thanks to it, the operating system can make use of all kinds of cryptographic functions in a safe way, protected from all kinds of hacks. This is in charge of controlling the encryption keys, passwords and other types of sensitive information with which the operating system works.
Some of the security measures in Windows depend directly on the security of this chip, such as Measured Boot, Device Encryption, Windows Defender System Guard (DRTM), and Device Health Attestation, among others. And it is not only used on Windows, but other systems, such as Linux, can also take advantage of the Trusted Platform Modulealthough it is not an essential requirement.
TPM 2.0 chips put your data at risk
Recently, two security flaws have been discovered in these cryptographic chips, registered as 2023-1017 and 2023-1018. These security flaws endanger billions of users who have Trusted Platform Modules on their computers.
These two serious vulnerabilities allow reading and writing outside the memory limits of these security chips. And, with this, critical and sensitive user information, such as their own cryptographic keys, can be revealed and even gain privileges within the operating system. In this way, an attacker, with local access to the system, could sign and send malware to the computer, and execute it successfully without security measures suspecting the code.
How to protect ourselves
Although these security flaws are one of the most dangerous things we can find when using a computer system, it is really very difficult to exploit. Not only because of the complexity of the vulnerability, but also because, in order to take advantage of these two security flaws, it is necessary for the attacker to have physical access to our computer in order to load the signed malware.
Therefore, the best thing we can do is make sure that no one has access to our computer. In addition, as always, it is advisable to make sure that we only use reliable software that comes signed from the Internet, and have good security measures that protect us from possible threats.
Finally, manufacturers will gradually release firmware updates for their motherboards in order to fix these two security flaws in TPM 2.0 chips. We must be vigilant and update the firmware as soon as possible to ensure that we fix these two security holes and that the Trusted Platform Module is once again as secure as it promises to be.