RDP is a Microsoft protocol used to allow users to connect to their computer remotely and use it as if they were sitting in front of it. This Remote Desktop protocol requires the user to log in with the same username and password that they normally use. However, despite the fact that Microsoft has included several security measures in its protocol, for years it has been failing in the same thing: allowing brute force attacks. Luckily, Windows 11 finally ends this problem.
When a hacker finds an RDP-enabled computer, they can connect to it remotely and attempt to brute-force the password. This type of attack tests, in seconds, hundreds of passwords until they find the valid one. While virtually all services have ways to protect themselves from them, Windows inexplicably left users at the mercy of these attacks. Until now.
@windowsinsider Win11 builds now have a DEFAULT account lockout policy to mitigate RDP and other brute force password vectors. This technique is very commonly used in Human Operated Ransomware and other attacks – this control will make brute forcing much harder which is awesome! pic.twitter.com/ZluT1cQQh0
— David Weston (DWIZZZLE) (@dwizzzleMSFT) July 20, 2022
Windows 11 locks accounts after several failed attempts
The latest Windows 11 updates have included a security policy that precisely ends this problem. What the new policy does is automatically lock the account after a certain number of failed login attempts.
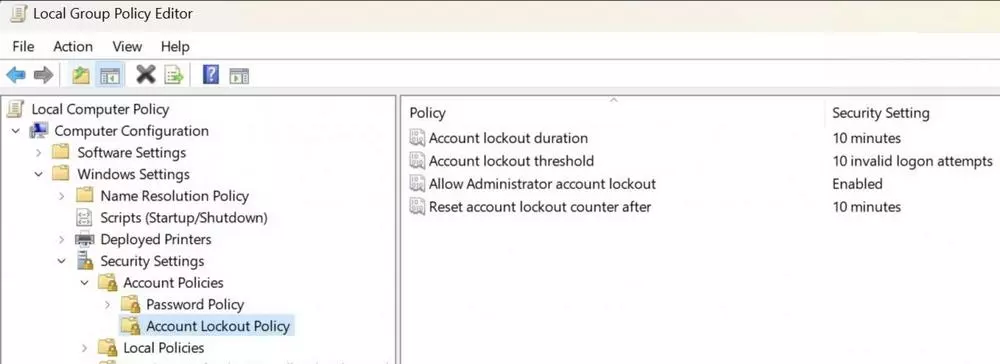
As we can see in the screenshot above, we can configure Windows to be able to lock the account automatically after a certain number of failed login attempts. By default, if the password is failed 10 times within 10 minutes, the account will be locked to prevent further combinations from being tried. We can also configure the time after which the account will be automatically unlocked, for example, 10 minutes. It even allows us to choose whether or not we want this lock to apply to the administrator account.
Thanks to these security measures, a brute force attack will only be able to try 10 keys every 10 minutes, making an attack that guesses our password totally unfeasible, however weak it may be. In any case, the best way to protect ourselves against these computer attacks that can control our computer is disable RDP if we are not going to use it. That way there will be no way for anyone to hack us.
Also for Windows 10
This policy comes as a novelty to Windows 11, enabled by default. However, Microsoft has also brought it to Windows 10, although in this case it is not activated by default, and we will have to be the ones to enable it through the system’s group policies. Of course, only available for the Pro and Enterprise editions of Windows 10.
Activated by default or not, it is a basic security measure, which should have been present in Windows for decades. Although, to be honest, it is not enough. Microsoft should consider other secure login systems for its Remote Desktop, whether through Windows Hello (nothing better than a good security key), an authentication system using digital certificates, and even double authentication through the Microsoft account.
Unfortunately, these security measures do not seem to be within Microsoft’s plans.