As a social network dedicated to the professional world, LinkedIn remains a prime target for hackers seeking to obtain sensitive information. And precisely, Microsoft’s cybersecurity division has just detected a cyberespionage campaign launched by Russian hackers linked to the Kremlin on LinkedIn.
For several years now, LinkedIn has not been spared by hackers who have multiplied malicious operations on the social network dedicated to professionals. A study conducted in April 2021 by MI5 (the British secret service) proved that fake accounts have invaded LinkedIn.
In February 2022, a report highlighted the worrying number of phishing campaigns on LinkedIn, with a 232% increase in phishing attacks since the start of the year.
However, the platform still seems to appeal to pirates all over the world, as evidenced by the last report of Microsoft’s cyber defense unit. Indeed, the experts of the Redmond firm have just detected a new cyber espionage campaign. Kremlin-affiliated Russian hackers are obviously at the origin of this operation.
LinkedIn, the playground of Russian hackers
According to the American company, this is the group of pirates dubbed Seaborgium (also known as ColdRiver). Suspected of acting on the orders of the Russian authorities, their operations mainly target key organizations and members of the governments of NATO member countries.
As Microsoft specifies in its Threat Intelligence Center report published on August 15, 2022, the procedure remains simplistic. These Russian hackers have created an armada of fake profiles and false email addresses on LinkedIn, with the aim of subtract information to professionals”from the world of intelligence, La Défense as well as non-governmental and intergovernmental organisations”.
The first step is to establish a relationship of trust with the victim. To do this, the hackers took over the identities of employees of a reputable company. After starting the conversation with their target, hackers send an email to the target user which contains an attachment.
Also read: LinkedIn – beware of these job offers, they hide malware!
Fake attachments to get your credentials
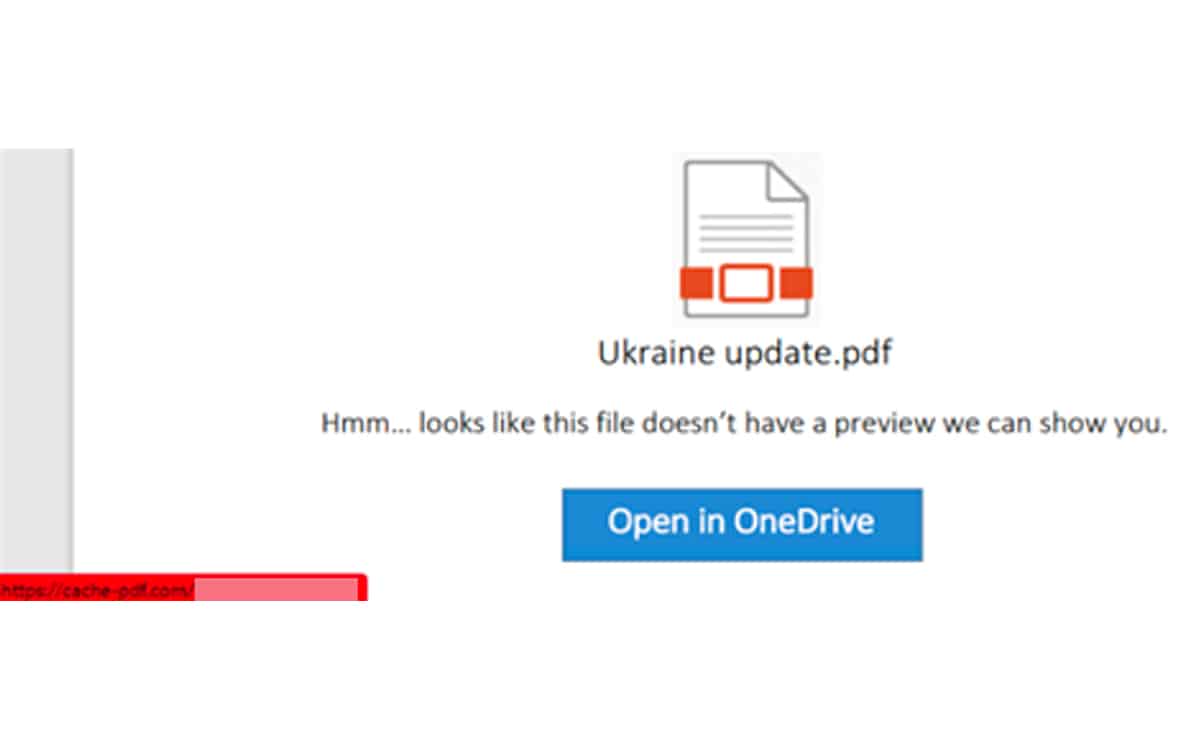
As can be seen in the screenshot from Microsoft, this is a pretext report (in this case, a so-called study on the state of the situation in Ukraine). Only and to open this famous PJ, it is necessary to enter his e-mail address login credentials.
Via EvilGinx, a computer tool used as a proxy, Russian hackers can intercept the information provided by the victim. Fact, even two-factor authentication is of no use here.
In total, Microsoft claims to have blocked 69 related domain names to this massive phishing campaign. Remember, be extra careful on LinkedIn when interacting with unknown professionals.