Ransomware cases have been making headlines since 2011, the year there was a drastic increase in attacks. Six years later, WannaCry entered history, created by the NSA and leaked by the Shadow Brokers group, he was responsible for coercing about 200,000 victims in 150 countries around the world to pay ransom in bitcoins during the attack. Despite appearing to be a 21st century invention, virtually blackmailing users in this way dates back to 1989, when an early pioneer of ransomware was used, according to Kaspersky.
Ransomware: A type of malware that enumerates the files and directories on a compromised machine, selects valid targets, and then encrypts the data, making it unavailable without a corresponding decryption key. The threat is divided into two types: blocking ransomware (blockers) and encryption ransomware (cryptors).
After the first concrete cases reported on Russian territory, in 2005, the type of malware spread throughout the world. Since then, ransomware groups have constantly improved their vectors, creating and repurposing codes and strategies. the speed How ransomware encrypts the targeted data — documents, images and videos — without interfering with the device’s basic functions is one of the important factors involved in a successful attack, though not the only one.
Ransomware put to the test
Although the time factor is not the main one, since most encryption attempts are successfully completed, the speed with which the malware ends the offensive allows us to assess, for example, the feasibility of a timely response to attacks.
LockBit, Babuk, Avaddon, REvil, Conti, Dark Side and four other families were put to the test of encryption speed in a study conducted by information security researchers at Splunk. The choice favored the most notable ransomware groups today.
Each of the 10 samples per family were tested on four host profiles, for a total of 400 encryption tests (10 families x 10 samples per family x 4 profiles). “We created four different “victim” profiles consisting of Windows 10 and Windows Server 2019 operating systems, each with two different performance specifications compared to customer environments,” explained Splunk in report.
To measure the speed of the process, the researchers collected 98,561 test files (pdf, doc, xls, etc.) from a corpus of public files, totaling 53GB. For this they used the native Windows registry, the Windows Perfmon statistics monitor, Microsoft sysmonthe open-source monitoring tool Zeekit’s the stock.
The researchers also simulated an actual corporate network setup, where host system hardware and operating system configurations varied from perfect lab conditions. From there, the analysts measured all encryption times and derived the average process speed for each variant.
25 thousand files per minute
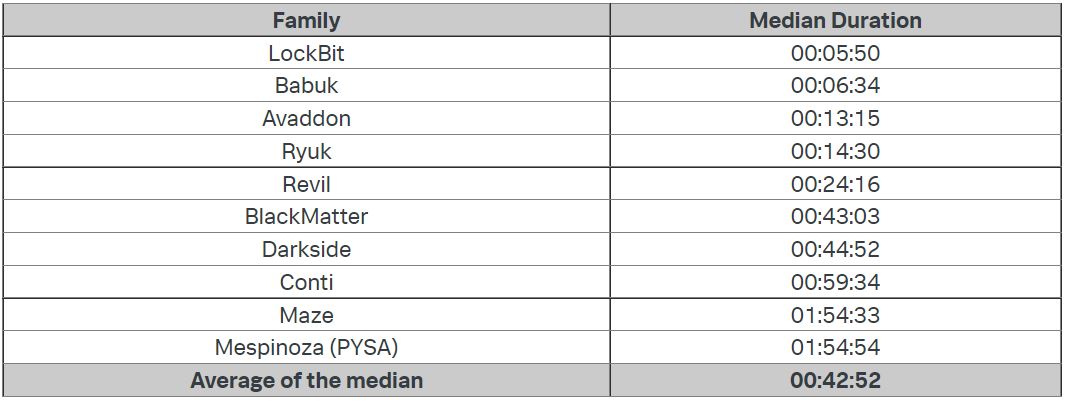
The total average of the values for the 100 different samples from the 10 ransomware strains on the test platforms was 42 minutes and 52 seconds. However, some samples deviated significantly from this value.
Image: Splunk
LockBit’s response time is striking as it averaged just 5 minutes and 50 seconds. According to the researchers, the fastest variant of LockBit encrypted 25,000 files per minute. No wonder the actors behind the threat have long bragged on the affiliate promotion page for how quickly they encrypt files, setting their own benchmarks against more than 30 different types of ransomware.
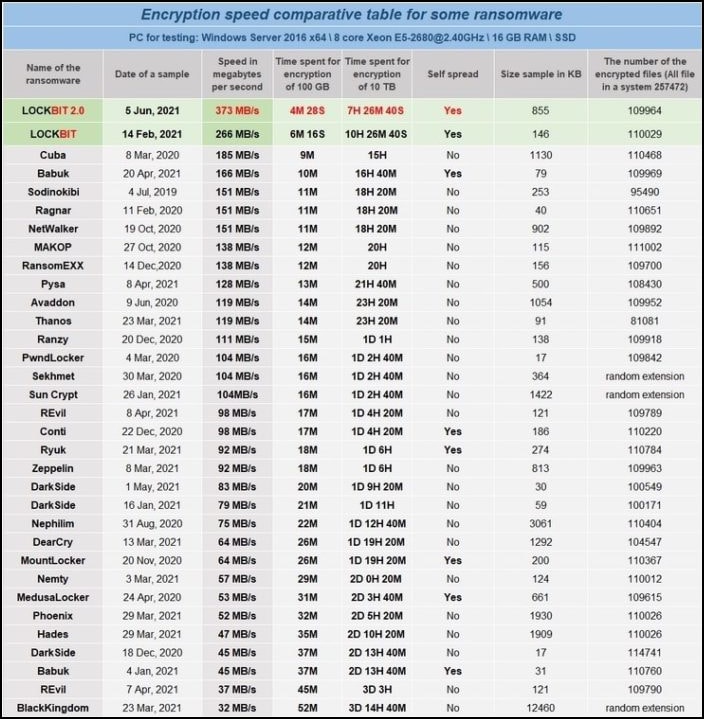
Image: Splunk
Avaddon, one of the most prolific ransomware groups of 2021 and which recently announced the end of operations by handing over decryption keys for free to victims averaged just over 13 minutes, while the REvil sample encrypted files in about 24 minutes. BlackMatter and Dark Side completed the process in 45 minutes.
At slower rates, it took Conti nearly an hour to encrypt the 54GB of test data, while Maze and PYSA spent nearly two hours to complete the task.
Better defense and a necessary change of approach
More than the speed in encrypting the target files, the strength of the encryption involved in the attack is what will determine how long-lasting or manageable the consequences of the attack will be.
While the time factor is important as an opportunity to detect ransomware attacks, reconnaissance periods, lateral movement, credential theft, privilege escalation, data filtering, disabling shadow copies, and so on are just as essential.
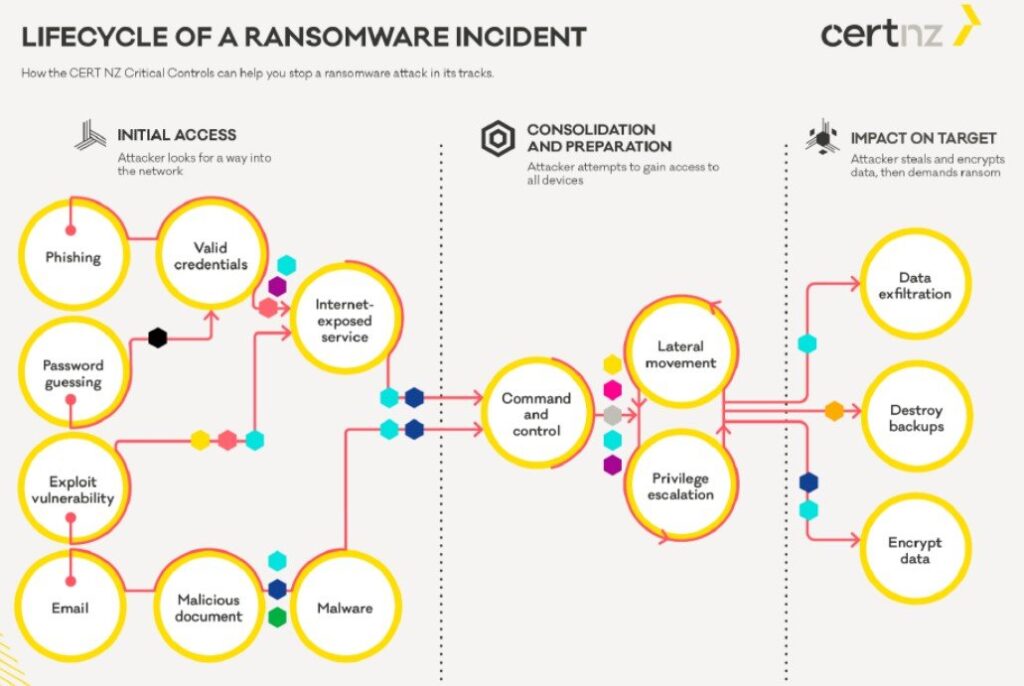
Image: CertNZ
Ultimately, focusing on this particular opportunity for detection and mitigation, given that there is little time to respond when ransomware is finally deployed, is unrealistic and wrong, according to analysts.
As Splunk notes in the report, the research demonstrates the need for a shift in incident response approach to ransomware prevention.
The overall average of 43 minutes is a small opportunity for network analysts to have a chance to detect malware activity. Previous studies show that the average time for this perception of commitment is three days.
When targeting weekends — when IT teams work on a small scale — most ransomware groups’ encryption attempts are successfully completed. As such, file encryption time should not be a significant consideration for defenders.
The researchers suggest that the best defense lies in detecting unusual activity during the reconnaissance phase, even before the ransomware is deployed. This includes looking for suspicious network activity, unusual account activity, and detecting commonly used tools before an attack, such as Cobalt Strike, ADFind, Mimikatz, PsExec, Metasploit, and Rclone.
with information from BleepingComputer and ZDNet



