A new remote access trojan (RAT) was detected by Proofpoint researchers during a small-scale email distribution campaign and reported last Wednesday. Stealthily, the Nerbian RAT is able to evade detection and analysis by researchers, as well as a rich set of features.
The new variant written in Go, which makes it a 64-bit threat across multiple platforms, uses macro-linked document attachments and mimics well-known institutions such as the World Health Organization (WHO), which sends alleged information about Covid-19 to users. targets.
Image: Proofpoint
The campaign uses RAR attachments with Word documents with malicious macro code. When opened in Microsoft Office, the content prompts you to enable it, while a bat file runs PowerShell to download a 64-bit dropper.

Image: Brian McGowan/Unsplash
The “UpdateUAV.exe” dropper, also written in Golang, is packaged in UPX to keep the size manageable. The executable reuses code from multiple projects hosted on GitHub to incorporate a rich set of anti-scanning and evasion detection engines before malware is deployed.
Additionally, the dropper creates a scheduled task that launches the RAT constantly to establish persistence.
You Proofpoint researchers made a list that summarizes the trojan anti-scanning tools:
- Checking for existence of reverse engineering or debug programs in the process list
- Checking for Suspicious MAC Addresses
- Checking WMI strings to confirm the legitimacy of disk names
- Checking if the hard disk size is below 100GB, which is typical for virtual machines
- Checking for any memory analysis or tampering detection programs present in the process list
- Checking the elapsed time since running and comparing it to an established threshold
- Use the IsDebuggerPresent API to determine if the executable is being debugged
The above checks assure malware operators of stealth in the long run, as it is virtually impossible to run the malware in a sandboxed, virtualized (VM) environment.
Features of Nerbian RAT malware
Downloaded under the name of “MoUsoCore.exe”, the trojan is saved in “C:ProgramDataUSOShared”. With various functions, the malware suits the needs of operators, who have the option of configuring it with some of them.
Nerbian has two notable functions: a keylogger, capable of capturing and storing keystrokes in an encrypted way, and a screen capture, which runs on all operating system platforms.
Communications with C2 handled with SSL protocol — Secure Sockets Layer — ensure encryption and consequent protection against inspection in transit by network scanning tools.
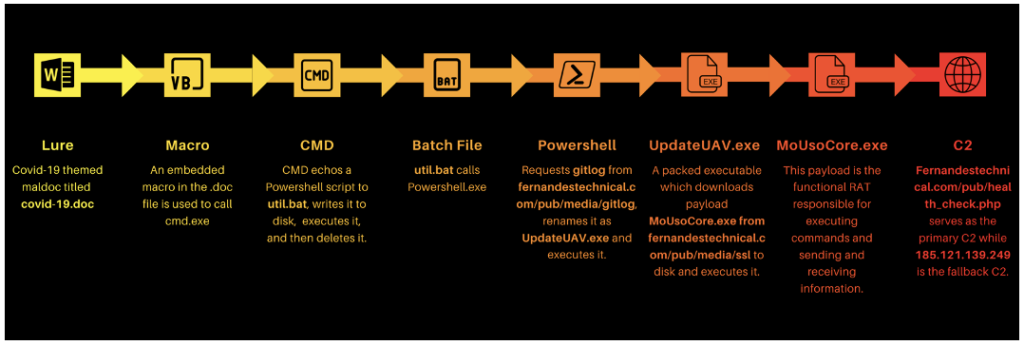
Image: Proofpoint
While malware is not a massive threat as it was detected in a low-volume campaign, it is possible at any time for actors to expand their business to a wider community.
Via BleepingComputer