Computer scientists at the Federal Polytechnic School of Zurich (ETH Zurich) have discovered a new Specter-type vulnerability that they have named Retbled and that affects older generations of Intel and AMD processors.
Specter vulnerabilities, which are of the side channel type, have been with us for years and have become a nightmare. The story goes back to early 2018, when the first two Specter variants were released along with Meltdown, another vulnerability that at least at the time only affected Intel processors.
Meltdown was solved relatively easily in exchange for losing performance, but the issue with Specter was and is much more delicate, not only because it affects Intel, AMD and ARM processors, but above all because it is impossible to solve. This situation has forced the incorporation of patches at the microcode level, kernels, drivers and even applications to minimize the radius of attack. To make matters worse, as we are seeing, every so often new variants appear that pose new challenges for developers and security experts.
Returning to the topic at hand, scientists have defined Retbleed as a Specter variant 2 family member, also known as Spectre-BTI. It has been located, like all security flaws of its kind, in the speculative execution feature that has been present in processors for quite some time, and can be exploited by software specifically designed to obtain passwords, keys and other secrets, as well as data. of the kernel used by the operating system.
The scientists have explained in statements to The Register that, compared to its sisters, “which trigger harmful jump target speculation by exploiting calls or indirect jumps, Retbleed exploits return instructions. This means a lot as it undermines some of our current defenses against Spectre-BTI.” In other words, Rebleed mitigation will require the development of new patches that will negatively impact performance.
Currently one of the main means to mitigate Specter-type vulnerabilities in x86 processors (Intel and AMD) is the Retpoline technique, which is responsible for replacing indirect jump instructions (from the jump predictor) with a return instruction subroutine ( return). However, Retbleed has the ability to rely on those return instructions, so it’s able to bypass Retpoline.
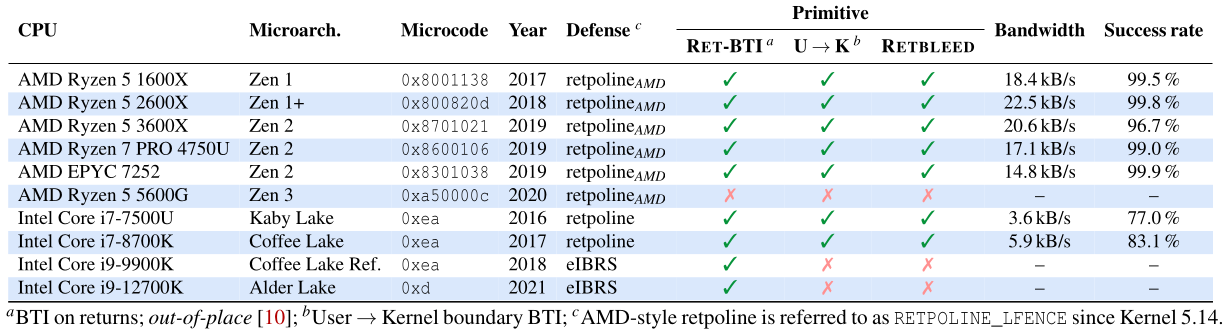
Directly, Retbleed affects Zen, Zen+ and Zen 2 processors within AMD Ryzen and original Kaby Lake and Coffee Lake (8th generation) within Intel. If combined with BHI, another Specter-type vulnerability that came to light last March, Alder Lake, and revamped Coffee Lake (intel’s ninth generation) are added to the mentioned processor generations, while Zen 3 seems to have gotten away in all scenarios. At this point it is nothing new that Intel processors are more affected by this type of vulnerability than those of AMD.
Intel’s 9th and 12th generation processors have withstood the direct execution of Retbleed thanks to eIBRS, a mitigation against Spectre, but apparently have not when the exploit has been combined with BHI. The researchers believe that additional action has possibly been taken by AMD around the speculative execution with Zen 3, hence it has apparently been spared.
Both AMD and Intel are currently working to mitigate Retbleed. The former is trying, at least from the front, to provide mitigations via a microcode update, while the latter will enable eIBRS by default and carry out complementary work to mitigate the vulnerability without the aforementioned component. At the operating system level, only Linux seems to have problems, since Windows has all the necessary defenses activated by default. Logically, Linux kernel developers are currently working to fix the problem.
Possibly more than one has remembered another Specter-type vulnerability that came to light not long ago, Hertzbleed, which is based on measuring the energy consumed to detect when the AES cryptographic keys were processed and thus open the door to being able to steal them. Although the method used by Hertzbleed was not new, the additional facilities it offered against other vulnerabilities that are exploited in a similar way ended up raising the alarm. We leave you with a demonstrative video of Retbleed exploitation.