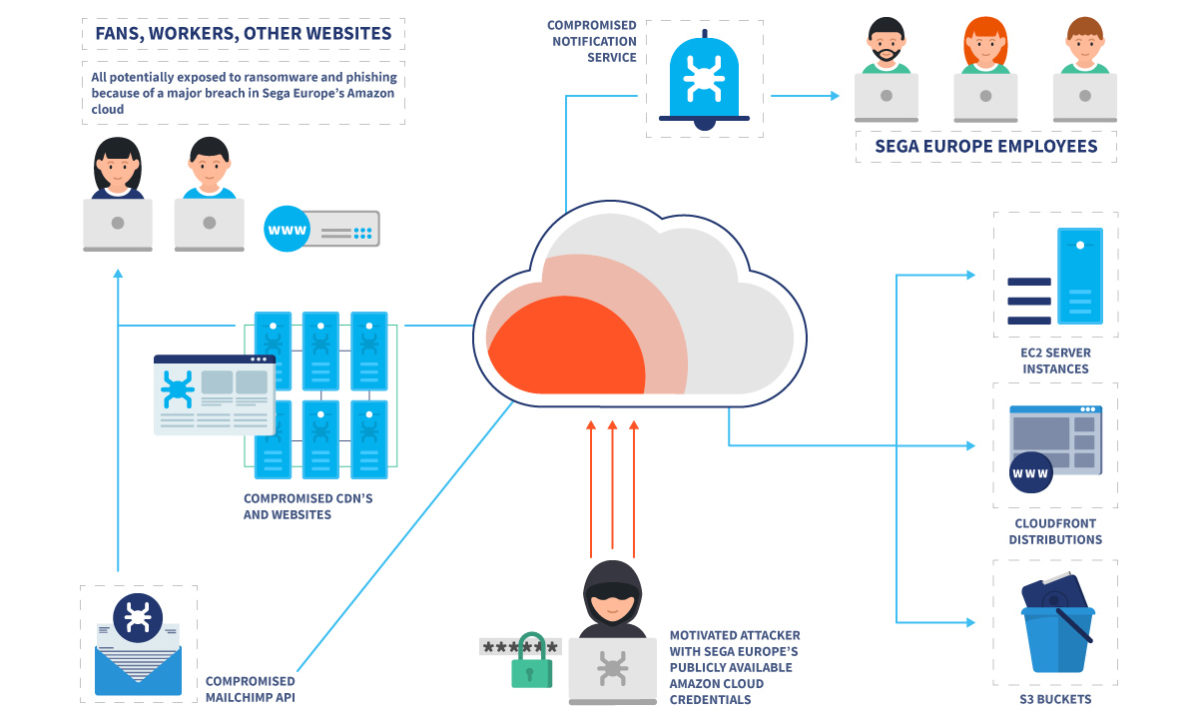
Discovered and recently closed, it appears that the Japanese company could have kept a vulnerability open on their servers that could have been a harmful rape, exposing the personal data of more than 250,000 users.
According to the report shared by security firm VPN Overview, the misconfigured Amazon Web Services S3 “cube” contained sensitive information that allowed researchers to arbitrarily upload files to a large swath of domains owned by Sega, as well as credentials to abuse an email list of its users, including the affected domains official landing pages of major franchises (including Sonic the Hedgehog, Bayonetta or Total War) as well as SEGA’s own official site.
And it is that unfortunately, the badly configured S3 containers are an extremely common problem in information security. Similar mistakes this year have affected the Sennheiser audio company, Senior Advisor, PeopleGIS, and even the government of Ghana. In fact, SEGA was the target of a major attack in 2011 that led to the leak of personally identifiable information belonging to 1.3 million users. Fortunately, this misconfigured European server did not result in a similar incident.
An incorrectly stored Mailchimp API key gave VPNO access to the aforementioned email list. The emails themselves were available in plain text along with associated IP addresses and passwords that the researchers were able to remove.
So, as security experts state, “a malicious user could have distributed ransomware very effectively using SEGA’s compromised email and cloud services‘, Being able to run executable scripts on these sites which, as you can imagine, would have been pretty bad if this breach had been discovered by malicious actors rather than researchers.
Fortunately, so far there have been no no indication that this vulnerability has been exploited before VPNO discovered it and helped SEGA fix it, but at the moment the company has not come to share any official statement.