Over the last few years we have been able to see that these attackers, among many other ways, they used the attachments of our mail to distribute viruses and other types of malware. Among the many programs used for these purposes, those belonging to the Microsoft Office suite were among the most common. Generally, to reach our computers, attachments were used in the form of phishing with malicious macros.
However, this is something that has been happening for many years, so little by little Microsoft has come up with a solution. This focuses on blocking these suspicious elements by default. One of the main tactics used has been to change the usual file formats to others such as ISORAR or Windows shortcuts LNK. Keep in mind that the macros VBA and XL4 are small programs created to automate repetitive tasks in de Office. Thus, these were used by attackers to load their codes through malicious Office document files.
Microsoft recently announced that it would put an end to this abuse. It does this by automatically blocking macros by default and making them difficult to access. activation on equipment. Although Microsoft took time to apply this change, the block finally went into effect a few days ago. But as you can see, cyber attackers are beginning to experiment with other methods to infect our computers.
This is how viruses now reach your PC
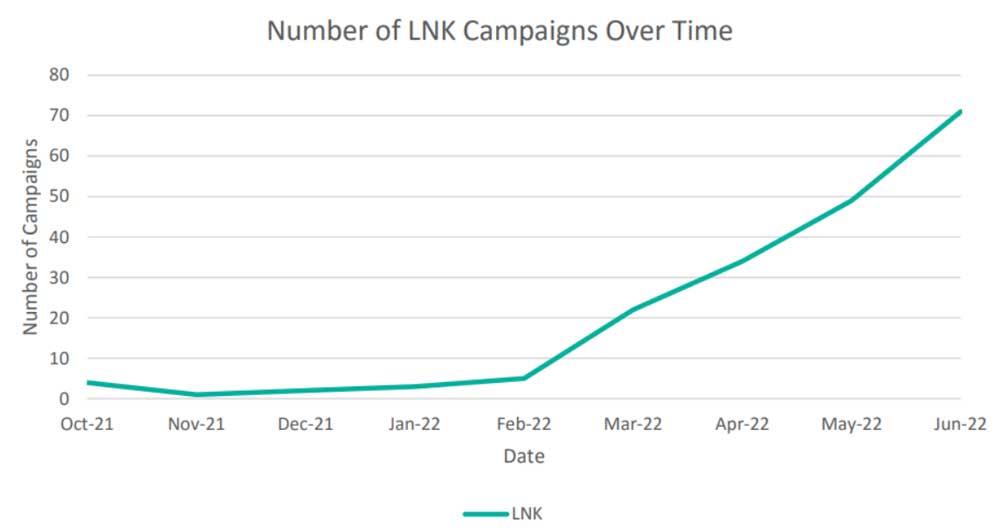
Based on data from a Proofpoint company report, malicious campaigns of recent months show a change in this regard. To give you an idea, there was a 66% decrease in the use of macros and Office. Similarly, the use of files in ISO, ZIP or RAR format has grown by almost 175%. Also, the use of LNK files increased by around a whopping 1,675%.
The problem with this last format that we mentioned to you is that LNK files can be used to execute almost any command for which the user has permission. Here are included powershell scripts that are downloaded and run, in some cases containing malware from remote sources. Therefore, the malicious use of these particular formats has increased considerably in recent months. This could be considered as one of the most booming attack routes at the moment.
Likewise, they have also detected a significant increase in the use of attachments in HTML format. All this in order to use them to introduce malicious content into the host system, something that is slowly growing. This means that even though Office macros have become a obsolete method of introducing virusesthe threats have shifted to other avenues or sources.
Also, to avoid detection by antivirus, many phishing campaigns now password protect attachments. This adds another step that the recipient must take to access the malicious files.