Researchers have developed a system based on the analysis of electromagnetic waves to detect any type of malware attack. According to them, their approach achieves a success rate rarely matched by traditional security solutions.
If the detection of all kinds of malware is usually based on a purely software solution, which has now proved its worth, researchers have just discovered a new method providing even better results. Security experts from the Research Institute of Computer Science and Random Systems (IRISA) have visibly found a near-foolproof way to detect malware and prevent them from harming.
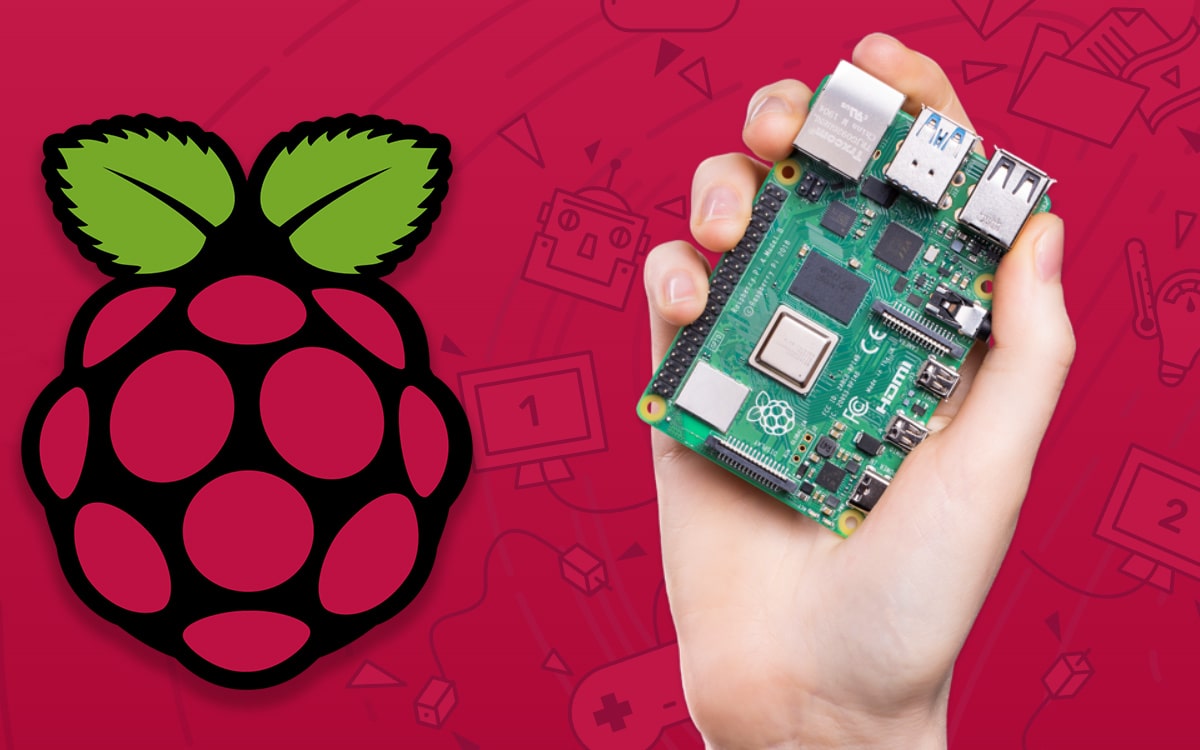
Their method is based on a Raspberry Pi, this very small PC sold at a low price and which can now be found everywhere. Equipped with a oscilloscope (a Picoscope 6407, more precisely) anda magnetic field probe H, the solution proposed by the researchers is 99.82% effective. What if they had designed the best antivirus ever?
The Raspberry Pi detects viruses using electromagnetic waves
The device uses a convolutional neural network (CNN), the connection pattern of which is inspired by the visual cortex of animals. After equipping their Raspberry Pi with the oscilloscope and the probe, the researchers trained it to detect variations in the electromagnetic field. In short, the device recognizes abnormal electromagnetic wave patterns issued by a computer as soon as it is attacked by malware.
The main advantage of this solution is that it is fully outsourced. As a result, the malware installed on a victim’s computer did not no way to hide from the eyes of the Raspberry Pi. It also cannot cripple its detection method, as it might attempt to do with a software solution installed on the target PC. Enough to undermine malware that is undetectable by security software.
This new approach to malware detection does not stop there, as researchers explain thatshe is also able to classify virus samples depending on the techniques used to compromise a file.
Obviously, this is not a complete security solution, since this method does not work like a classic antivirus. In essence, it is unable to act on the target computer: it cannot eradicate malware since it works remotely. But the idea is pretty good and we can’t wait to see if it can be deployed on a large scale.
Source: Tom’s Hardware