The ecosystem of Android It is considered by many to be out of control due to the great freedoms granted by Google. Although this has its virtues, it also brings its drawbacks, so the search engine giant decided to implement a protection mechanism called Google Play Protect which is inside the Play Store.
Google Play Protect defines itself as “the most widely deployed mobile threat protection service in the world.” It basically consists of “Google built-in malware protection for Android. Backed by the strength of Google’s machine learning algorithms, it’s always improving in real time.”
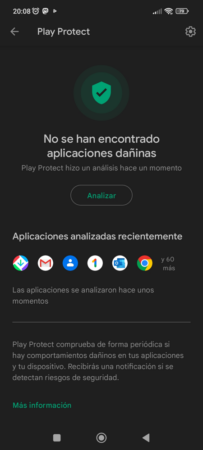
Google Play Protect is an active service within the Play Store application whose mission is to protect the smartphone, even if it is stolen. The logical thing is to think that it is an application scanning mechanism, which is obviously true, but it also has measures against theft with the service find my device and provides secure browsing through Chrome, Google’s well-known web browser.
When it comes to Android app verification, the service is responsible for scanning more than 100,000 million applications every day with the aim that at least the ecosystem that is supported by the Play Store is safe, although 100% security is something that can never be guaranteed. The Mountain View giant recalls that it submits all applications that intend to be published in the Play Store to rigorous security tests, and that is that, if you want to build trust among consumers, you have to be very rigorous and effective with security, an aspect that has been criticized for a long time in Android for various reasons.
Google Play Protect seems to go somewhat unnoticed, but it is one of the mainstays of security within the part of the Android ecosystem that is directly controlled by the search engine giant (F-Droid, for example, is not its responsibility). Because of that, I am going to detail a bit about the features that the service offers.
Application scanning
Application scanning is the most well-known and arguably logical feature of Google Play Protect. As I have already collected, it uses automatic learning to be more effective when carrying out its work. The company says that it now scans more than 100,000 million applications daily in order to guarantee maximum security for Android users.
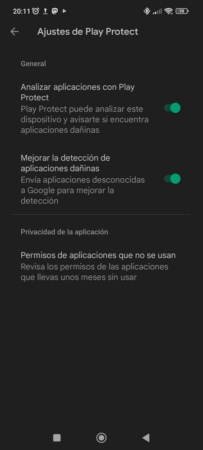
Machine learning is used to distinguish application behaviors and detect those that are abnormal. In the event of detecting malicious behavior in an application, it will notify the user and it would even be able to automatically disable the source application in order to stop the damage. It also warns about the permissions granted to applications that have not been used for months.
Although it is integrated into the Play Store, Google Play Protect not only covers applications that come from the official Google store, but also those from third-party stores or repositories that the user has configured on their device. The user can carry out a manual analysis at any time.
anti-theft measures
Anti-theft measures do not refer to the data, but to the device itself. It is supported by the “Find my device” feature or find my device that Google makes available for the purpose of locating one that has been lost, misplaced or stolen.
To use find my devicethe user will have to resort to a web browser or other device that has an Internet connection. Among the possibilities it makes available are remote calls, locating and blocking an Android device, and even remotely erasing data to prevent it from ending up in the wrong hands.
“Find my device” is what in the past was known as Android Device Manager, which is now integrated into Google Play Protect and its use is more accessible to the user.
Secure browsing
Safe browsing works through Google Chrome and is responsible for notifying and blocking suspicious or insecure web pages when the user tries to access them. Nothing that is not logical and obvious.
Google cares a lot about security, and it’s important to distinguish this from privacy. The company is interested in and even convenient for its users to be protected against malicious actors that can damage applications, operating systems and/or steal data, but another thing is that this protection has the user’s data as an alleged price. While it is true that it is possible to strengthen the privacy of Chrome, the fact that it is a proprietary application does not guarantee that said privacy also covers Google services.
At this point, using the safe browsing of Google Play Protect with Google Chrome or using another browser is already a decision that must be made by the user. Seeing the market share that Chrome commands, it seems that most of them wouldn’t mind having a little more protection in exchange for possibly giving up some data.
How to access Google Play Protect from Android?
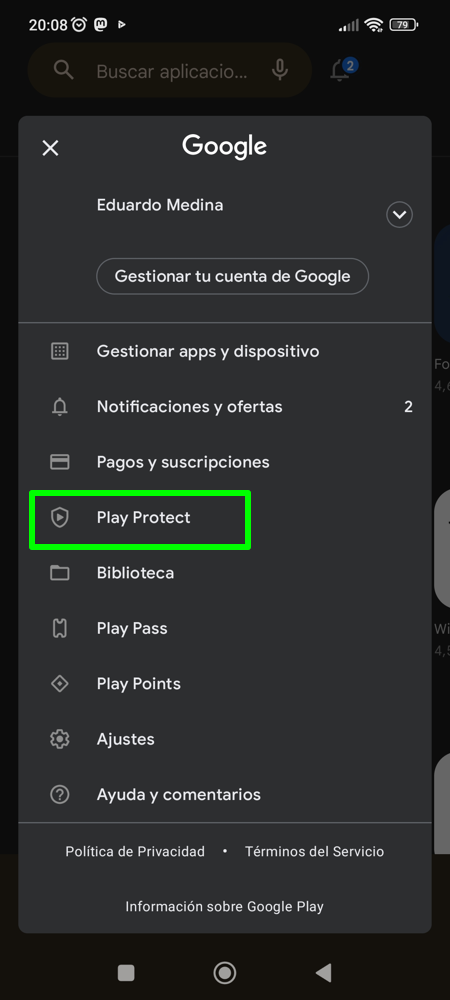
Accessing Google Play Protect is easy. For this you have to open play store on android and click on the user’s avatar in the upper right corner of the application interface. Then a menu will open from which you can reach Play Protect, which is explicitly mentioned. Of course, not all the features are present, at least directly, from the Play Store application.
Android 14, a possible challenge for Google Play Protect?
It is likely that Google has plans to improve Play Protect in the near future, since lThe company plans to improve support for third-party stores in Android 14the next version of the mobile operating system.
This change in favor of improving the support of third-party stores is partly derived from the pressures that both society and governments are exerting so that the technology giants offer more open ecosystems. The company most criticized in these matters, as our readers will know, is Apple, more specifically because of how restrictive iOS is. However, after years of pressure, the Cupertino giant could relent to allow the use of third-party stores on iOS and other web rendering engines than the WebKit that comes pre-installed on the system.
Google, for its part, has not received as much criticism because in the end it has always allowed the use of third-party repositories and stores on Android, even if it required modifying the system’s security settings. On the other hand, the framework that currently exists can be improved, so the company has gotten down to work.
The improvement of support for third-party stores is a point that, logically, could require improving the security mechanisms included in the Android implementations attached to the Google ecosystem, so the door is opened to modifications in Play Protect to improve it.
Conclusion
Although it does not have much media presence, Google Play Protect is a service that the user should take into account, and not only with regard to the applications installed on their mobile, but also for cases in which they have lost the device.
As I’ve said on several occasions, Google tends to be quite careful when it comes to security, but it shouldn’t have given manufacturers as much freedom when it comes to system maintenance, especially when it comes to the distribution of the updates. This point is much better made in any of the other systems that have achieved at least relative success in home computing, starting with its direct rival in the mobile segment, iOS, and continuing with Windows, macOS and Linux, all three. large desktop operating systems
Unfortunately, the use of Android custom ROMs is actually quite minor. On the other hand, the strong dominant position of WhatsApp, whose client is proprietary, and the very barriers that mobile devices usually include, end up making it too difficult for alternative operating systems within mobility. While Google Play Protect is an interesting and important addition, does not correct the risks of using an operating system without maintenance by its manufacturerand in that case it’s better to have a well-maintained OS without Google Play Protect than one without maintenance but with Google Play Protect (you can also have an Android ROM and Google Play Protect, if anyone’s wondering).