Some examples of important Trojans are Zeus, Emotet, Petya or WannaCry. They have put numerous companies and also private users at risk. Keep in mind that this type of attack not only affects home users, but also targets important organizations.
What is its function and how does it affect
Trojans can have different functions and features. not everyone acts the same and not all are equally dangerous. We are going to explain what its main functions are and how it will affect the security of both home users and companies and organizations that are infected.
Create a back door
The first goal of a Trojan is to create a backdoor. It is one of the most common attacks that can occur. This gate will allow the attacker to gain some control or access to the device. For example, it will be able to leak data, malicious files that obtain information, etc.
Usually the victim is not quickly made aware of the problem. That is, no noticeable symptoms appear as a malfunction at first. This makes it possible for an attacker to have access to a system for a long time until he is discovered, so he has room to collect data.
hidden downloads
There are also download Trojans. Your goal will be download content on the computer without the victim’s permission. It will do this in a hidden way, through commands that have previously been programmed to carry out certain actions once it enters the device.
Usually these hidden downloads are linked to more malware. They can download viruses and other varieties of malware that affect security and privacy. For example, they could download a keylogger that is responsible for stealing the passwords that the victim puts on the computer.
steal information
Another clear function is to steal information from the computer they have infected. They can collect personal data of the victim, spy, collect data related to browsing, programs used, files on that computer, etc. It can steal all kinds of data.
These data can be used for different purposes. For example, they could be used to carry out personalized Phishing attacks, steal confidential data from a company or an organization and then sell it to the competition or even extort money with that data and threaten to make it public.
Remote access
Another objective of Trojans is often to grant a full remote access to an attacker. He’s basically going to be able to act like he’s physically in front of the team. He will be able to control the system, install or uninstall applications, delete files, modify documents, etc.
This also makes it possible to scale up attacks, as full remote access to a system opens up a wide range of possibilities for cybercriminals. They will be able to steal data or install any application without permission.
DDoS attacks
On the other hand, mention must also be made of DDoS attacks or distributed denial of service. A Trojan can launch attacks of this type to saturate a server and that it cannot respond to legitimate requests that another user will make and will find that it does not work.
Trojans can be designed for this purpose and the objective here is to affect the proper functioning of a company, for example. They can serve as a way to launch attacks that compromise computers based on launching multiple requests.
Tips to avoid this type of malware
As you have seen, a Trojan is a major security threat. It is essential to take steps to avoid falling victim to these attacks. For this reason, we are going to give some essential advice so that our devices are properly protected and problems do not appear.
Use security software
Something very important to maintain security and avoid Trojans and other threats is to have a good antivirus. There are many options. One of the most used is Windows Defender itself, the antivirus that comes with Microsoft systems. However, there are many free and paid options. For example Avast or Bitdefender are some alternatives.
But beyond an antivirus, you can also count on a firewall. It is another tool that will protect Internet connections and prevent attacks. In addition, you can always use browser add-ons to alert you in case of accessing a malicious site or downloading a dangerous file.
Keep everything up to date
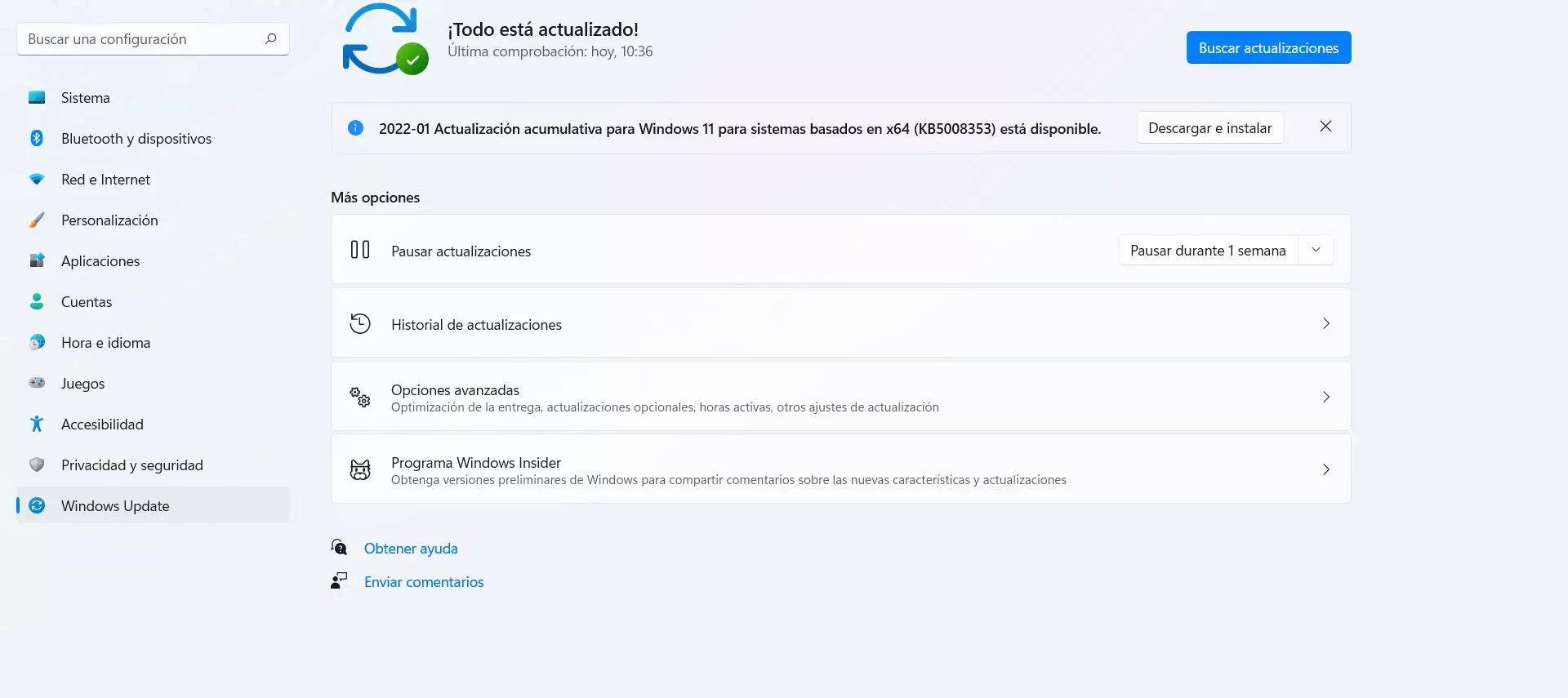
Of course it is essential keep everything updated. In fact, cybercriminals can take advantage of a vulnerability to sneak a Trojan. They could use a bug in Windows or in some program you use to sneak in malicious software without you realizing it and be able to control the device.
In the case of Windows, to update the system you have to go to Start, enter Settings and access Windows Update. It will automatically show you possible pending updates and you will have to add them to have everything ready and protected to get the best performance and also avoid problems.
Install only official apps
Something very important, and that is not always taken into account, is to install only official apps. It is true that there are many options for almost everything, but the ideal is to only use programs that are reliable, safe and that have not been maliciously modified to steal data or, in this case, sneak Trojans.
To achieve this, it is important to download programs only from official sources. For example, go to the official website of the application or use secure stores such as Google Play. In this way we will have more guarantees that this program has not been modified by a third party to steal information.
Common sense
But without a doubt the most important thing is common sense. In most cyber attacks, the hacker is going to need us to commit some error. For example, clicking on a dangerous link, downloading an insecure file, etc. This makes it essential to take care of your navigation and not make mistakes.
For example, you should make sure that you don’t download attachments that come to you via email if you don’t really know the source and you’re not sure if it could be a threat or not. The same when logging in or opening any link. You should always check that it is something reliable and will not be a problem.
In short, as you have seen, Trojans are a security threat that can compromise your personal data or the functioning of the system. It can have different functions and you should always keep the equipment protected. You have been able to see a series of essential tips to avoid problems.