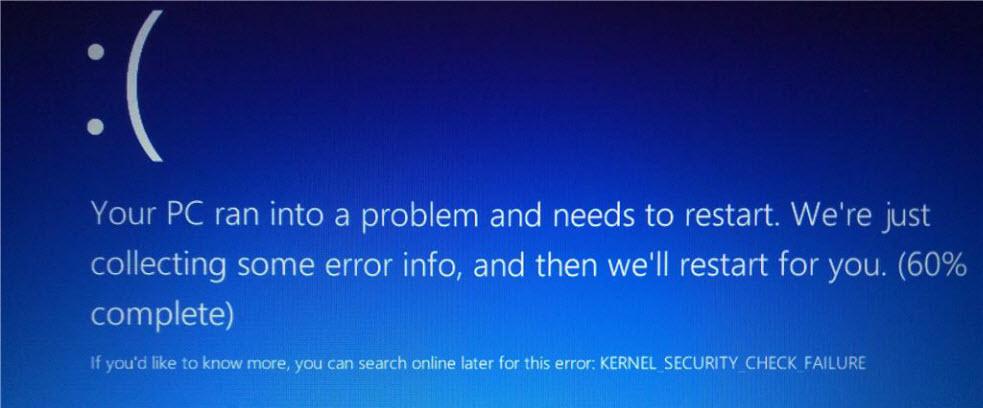
Bugs, it should be noted, that at the end of the year end up causing costs to companies. We are living in a transition to the digital world and software is increasingly important. Thanks to this computer bug, we experience crashes, slowdowns or security failures that can cause the leakage of our confidential information. A typical failure of this type is the windows blue screen of death which comes from the acronym in English BSoD (Blue Screen of Death).
When these types of bugs occur, they are at least a waste of time since you have to restart and sometimes start the job again.
What is a computer bug and a brief history
A computer bug We can define it as a failure or error in a computer or software system that ends up causing an unwanted result. If we want to find or eliminate these bugs we have to use a type of software called debuggers or in English debuggers.
The term bug It is used at least since 1872 in which Thomas Alva Edison used it in his notes, in addition, it appears in a letter from him of 1878 in which he talks about mechanical or electrical defects, and also in 1889 he used it when he made a reference to the interference and malfunction of a phonograph.
At first he was associated with the physicist and mathematician Grace Murray Hopper and others who worked at Harvard University on the Mark II. Thus, they reported that a computer had suffered a failure in the electromagnetic relay. Then later when that relay was investigated a moth was found (bug) frit that made that relay stay open. So Hopper taped that bug onto the blog in which he added this incident.
How it originates
In most cases, a bug is created by a failure or error on the part of those who develop the code of a software or system. Some common programming errors that we can find are division by zero, infinite loop, arithmetic problems such as overflows (overflow) or underflows (underflow), exceed the size of the defined array, or use an uninitialized variable.
Typographical errors in which the number “0” is confused with the vowel “O” are also the order of the day. To finish with this section, other bugs that we can find are:
- Buffer overflow (buffer overflow).
- Memory access not allowed (access violation)
- Syntax errors, such as not ending a statement with a semicolon (;) in a programming language that requires it.
- Incorrect use of API.
Who can be affected by a computer bug?
A computer bug can affect various computers of a very diverse nature, such as:
- A computer or laptop.
- To the smartphone or tablet.
- A home router or network equipment.
- To IoT, home automation or video surveillance devices.
In that sense, we could find a failure in the firmware of a device. We can also find a bug in a computer operating system such as Windows, Linux and MacOS. Nor should we forget that mobile operating systems such as Android or IOS are not free from these flaws.
Classification of the bug according to its severity
The severity of a computer bug will be determined based on the impact that the failure has on the operation of the system or equipment. This negative impact can be translated in various ways such as data loss and decreased revenue.
The rules for classifying a software bug should be determined based on the task they perform. For example, a bug in a game, an Internet browser, or a real-time security monitoring system has a different impact.
However, although the severity levels are not standardized, these are commonly used:
- Critical: This is an error that, when it occurs, makes the program unable to run. These are errors that can crash the system.
- Tall– Occurs when that error seriously affects the functionality of the application and makes it difficult to use.
- Half: We can work, but from time to time we have messages from the application that are incorrect or small bugs that slow us down.
- Under: they are low-impact errors, and they affect us little or nothing. We can see aesthetic errors in the user interface or typographical errors. Some examples could be menus that you have forgotten to translate or that, between the names, strange characters appear.
Depending on the severity of a computer bug then they are usually corrected. Thus, a critical vulnerability is usually fixed in the next update. “High” or “critical” security flaws usually do not take long to fix, mid-level security flaws depend on how annoying they are, and lows may never be fixed.
Also, a frequent occurrence is releasing software with known low-priority bugs. The reasons for making these decisions not to fix a low-priority computer bug are usually twofold:
- It is not possible to fix it before the release date and the bug will be fixed in a future update.
- The changes to be made are financially too high.
Rewards for finding bugs
Programming errors are the order of the day. As we discussed earlier, it can range from low severity to critical. Large companies, to avoid loss of prestige and sometimes a lawsuit, invest money in rewards for those who discover a computer bug in their software. Obviously, the critical and high errors will be the ones that report the most benefits to their discoverers. In fact, this is currently done both individually and through some companies.
Among the large organizations that offer rewards for discovering a bug we have Microsoft, Google or Facebook.
Protect ourselves from a computer bug
The first thing we have to do is have our operating system with the latest available updates installed. Also keep in mind that it is better not to use old operating systems such as Windows XP or 7, because they no longer receive updates.
When we use an outdated or outdated operating system, we are putting our equipment at risk. Cybercriminals know how to exploit this computer bug to obtain our confidential information, to integrate us into a botnet or any other way that may interest you to obtain revenues.
In addition, the rest of installed software must have the latest updates onsuch as Microsoft Office and computer component drivers. Finally, we must not forget to install the firmware of the router, the hardware, the network equipment and other devices connected to the Internet, in addition to providing them with a suitable configuration.





![6 Best uTorrent Alternatives [2020]](https://techunwrapped.com/wp-content/uploads/2020/09/uTurrent-best-alternatives.jpg)