A backdoor for the Linux platform has been recently discovered by researchers at the Qihoo 360 Network Security Research Lab (360 Netlab). The malware uses rootkits, creating reverse shells and acting as a proxy for web traffic to steal information mainly from Linux ARM, X64 CPU architecture devices.
Dubbed B1txor20 by researchers, the botnet uses expoits targeting the Apache Log4J registry library vulnerability to infect new hosts.
The malware was discovered on February 9, when the first sample became trapped in one of 360 Netlab’s honeypot systems. At that time, the researchers captured up to four samples that contained, in addition to traditional backdoor functions, opening Socks5 proxy, and remote downloading and installing the rootkit.
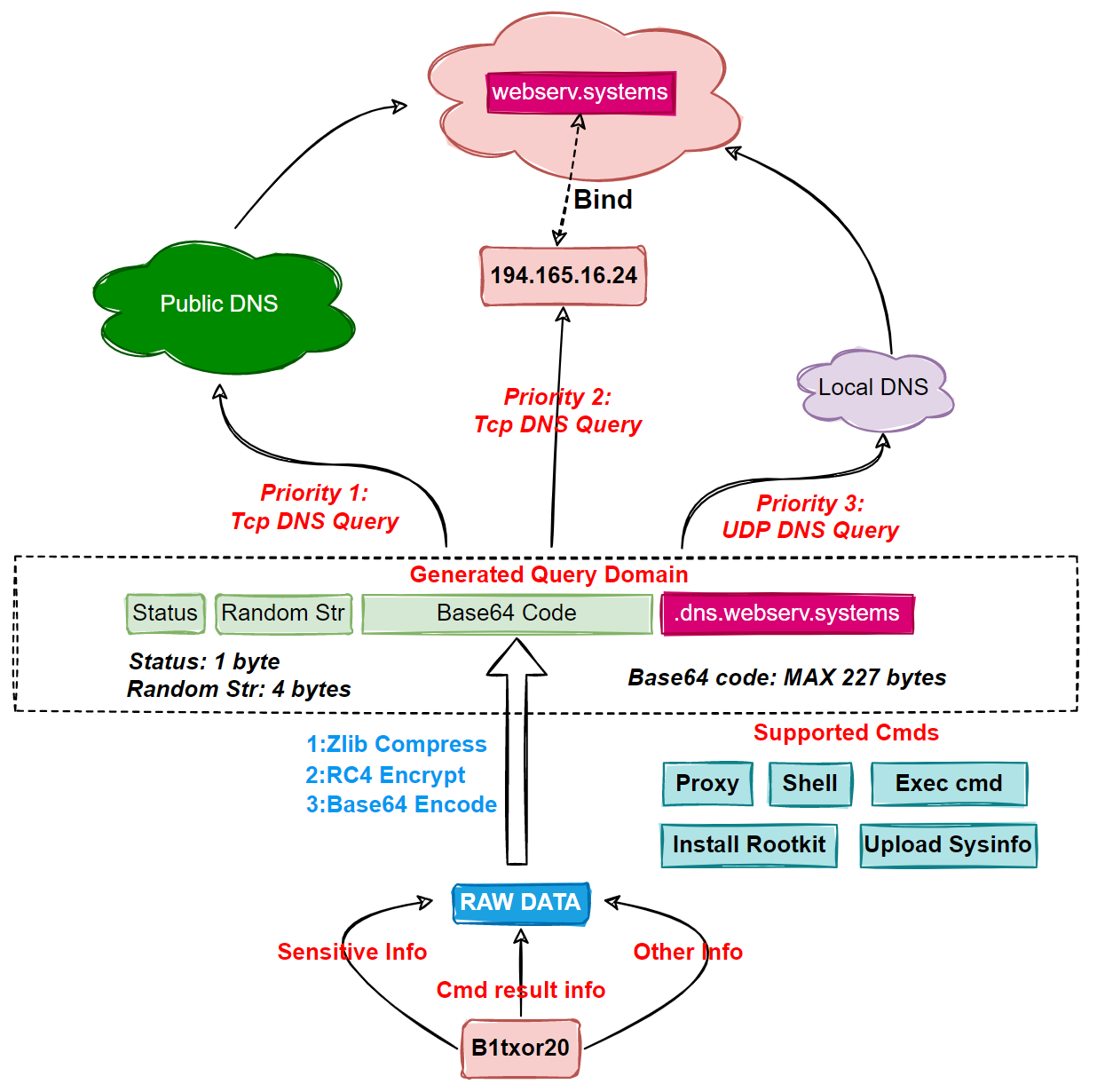
DNS tunneling to hide C2 communication traffic
One of the features of the malware that draws attention is the use of DNS tunneling to establish communication with the C2 server (command and control). Although old, the technique is reliable and used to exploit the DNS protocol for malware and data tunnels via DNS queries.
Image: 360 Netlab
“The Bot sends the stolen sensitive information, the results of the command execution and any other information that needs to be delivered, after hiding it using specific coding techniques, to C2 as a DNS request”, explain the researchers. “After receiving the request, C2 sends the payload to the Bot as a response to the DNS request. In this way, Bot and C2 are able to communicate with the help of the DNS protocol”.
Researchers at 360 Netlab have observed that a broad set of features are added to the malware, although not all of them are enabled. They believe there are still issues and the threat creators are still improving development to use them in the future.
Log4j Continuous Expos
Like other malware families, B1txor20 also takes advantage of a flaw in the Log4J library. “Since the Log4J vulnerability was exposed, we’ve seen more and more malware jumping on the wagon, Elknot, Gafgyt, Mirai are all very familiar,” the 360 Netlab researchers add.
In December, they detected threat actors exploiting the registry library flaw to infect Linux devices with malware dedicated to the Mirai and Muhstik platform.
Furthermore, researchers reveal that botnets have been seen “recruiting” IoT devices and servers to deploy cryptocurrency miners and carry out large-scale DDoS attacks.
Earlier this month, cybersecurity firm Barracuda confirmed the information of the Netlan 360 report, warning that they also detected several payloads targeting Log4j vulnerabilities, with variants of Mirai botnets leveraged for DDoS and miners for the most part.
Via BleepingComputer



