Hacks in Google Cloud to mine cryptocurrencies
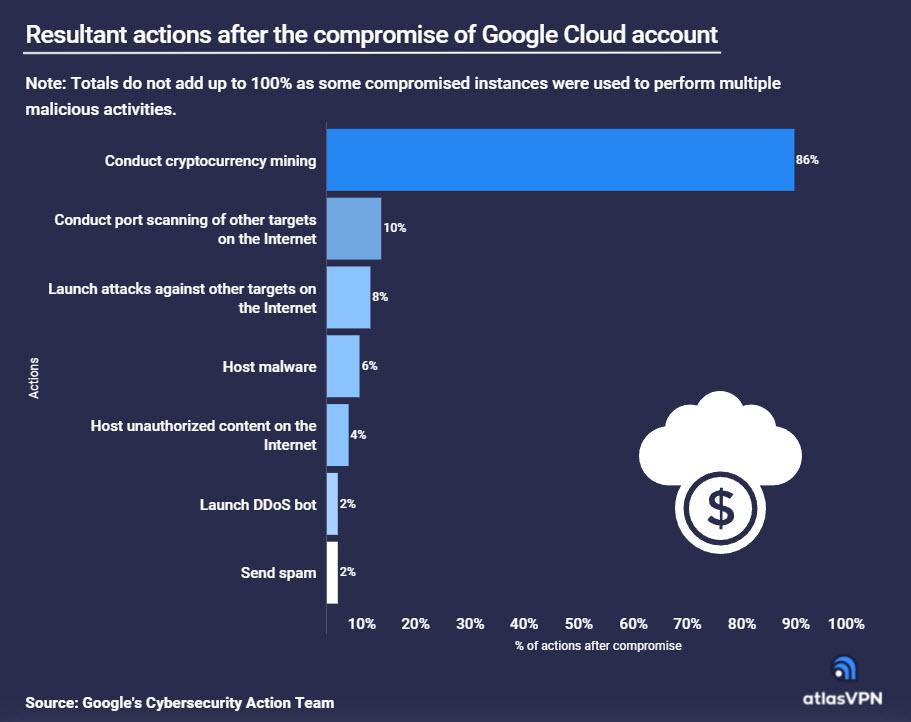
In many cases, a successful attack on the cloud is due to poor security measures and also a lack of control implementations. Without strong protection, cloud services can become easy targets for cybercriminals. In a report by the Atlas VPN team, it was revealed that the 86% of Google Cloud accounts hacked I know they use for him illegal cryptocurrency mining. Regarding most of the hacks in Google Cloud, they are due to a weak password or that they did not have one in the user’s account. These are the results after a Google account was compromised.
The data is taken from a Google Cloud Threat Intelligence report. Cybercriminals engaged in cryptocurrency mining in 86% of the situations as we discussed earlier. Cryptocurrency mining is a for-profit activity and consumes a large amount of GPU and CPU resources of those affected. By using victims’ computers, cybercriminals consistently reap huge profits.
Also, as can be seen above, Google Cloud hacks were also used to:
- Port scanning of other targets on the Internet occurred with 10%. Port scanning allows you to find out if network ports are open. (aristocratps.com) Thanks to this, cybercriminals can identify weak points in a network and exploit any vulnerabilities they find.
- Launch attacks against other Internet targets with 8%.
- Hosting malware in the cloud with 6%.
- Store unauthorized content on the Internet with 4%.
- 2% DDoS bot launch.
- Send spam with 2%.
You may be interested in knowing what Google Hacking is and how it can affect your privacy.
The most attacked vulnerabilities in the Google cloud
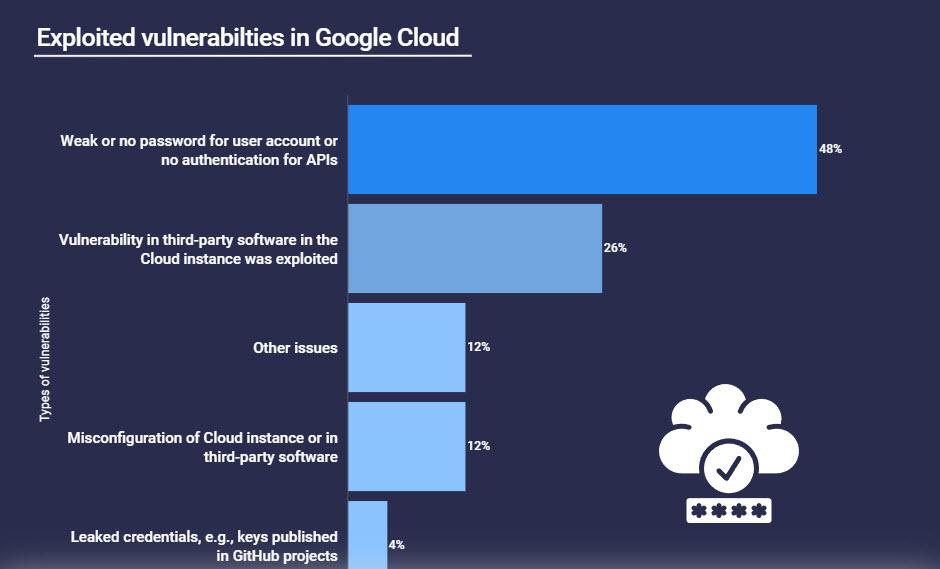
Hackers when carrying out an attack are always looking for the easiest way to compromise their target. Sometimes sophisticated methods are required, but sometimes just entering the correct password is sufficient. In that regard, the 48% of Google Cloud hacks were due to a weak or no password for a user account or also to the lack of authentication for the APIs. By simply setting a more secure password, these users could have prevented their account from being hacked.
On the other hand, cybercriminals exploiting a vulnerability in third-party software in the cloud instance was 26%. In this regard, if we find a zero-day vulnerability, that failure could be attributed to the software developers not releasing an update. However, if that patch was released, the responsibility lies with the security team who did not update that software in time.
Also the incorrect configuration of the cloud or third-party software allowed 12% of the attacks in Google Cloud. Keep in mind that incorrect settings can make it easier for hackers to hack into Google Cloud. On the other hand, other problems caused 12% of the attacks on Google Cloud and another 4% of the attacks were due to leaked credentials, such as keys published in GitHub projects.
In summary, to avoid hacks in Google Cloud, the first step we must take is to have a strong password. However, if we want to improve security even more, we can activate multi-factor authentication to protect our accounts with Google Authenticator.