Therefore a router failure may mean that the device stops working properly or may put connected devices at risk. There is a wide variety of vulnerabilities that have appeared in recent years, that are present now and that will appear in the future.
how they affect
After explaining exactly what router vulnerabilities consist of, we are going to talk about how they can affect us. They will represent a major problem when browsing the Internet and, also, they will pose an added security risk that could enable a hacker.
Security issues
First and foremost, router vulnerabilities can negatively affect the security. This can be a problem for the other computers that we have connected through the local network. For example, computers, mobile phones, televisions… They can all be affected if there is a fault.
A vulnerability that affects the Wi-Fi key encryption, for example, could allow intruders to enter the network. This is going to affect the information we transfer over the Internet, in the same way that when we connect to a public wireless network, there can be intruders who steal data.
They can take advantage of this circumstance to exploit that known vulnerability and be able to take control of the router. They could configure it at will, enable the entry of other devices, modify the DNS and lead us to malicious pages when we enter a page, etc.
This last, the DNS hijacking, is undoubtedly one of the most serious security problems in a router. It basically means that the attacker is going to control what sites we visit. That is, let’s take the example that we are going to access our online bank account. We put the URL in the browser, but the router does not redirect us to the legitimate address, but to a page that pretends to be that to steal the data.
poor performance
Another very important problem is that it will cause performance issues. For example, that the speed is not adequate, that signal cuts appear, poor coverage, etc. These types of vulnerabilities can affect the operation of the firmware or some component of the router.
A clear problem is that this type of error does not allow the firmware of the router to correctly manage the requests. This means that, when connecting any device to the network, it may take longer to respond and this affects the speed of the connection, generates higher latency and, ultimately, has problems with tasks such as playing online, downloading files or simply open a web.
Something very common is that an attacker exploits vulnerabilities to turn the router into a bot. In this case, it may not directly affect our security, but it does affect performance. Our device can be used to send requests on the Internet and join a botnet to perform DDoS attacks and make a server stop working, for example.
After all, vulnerabilities will affect the proper functioning of equipment regardless of whether it is a router, a computer or any other device. It is something similar to what would happen with some software that we are using and we cannot obtain optimal performance.
What to do to solve them
After having explained how vulnerabilities can affect routers, we are going to take a series of steps to solve them. The goal is to always have our device ready, protected, thus achieving optimal performance when browsing the net and avoiding any problem.
upgrade the router
The first thing you need to do is make sure you have the properly updated router firmware. This will allow you to correct any vulnerabilities that may appear and ensure that the operation is optimal. The process is simple, although it may vary depending on which model you have. There are basically two options: update it manually or have it installed automatically. If it’s automatic, you don’t have to do anything.
If you have to update the router manually, you will usually have to go to the official website of the brand, find the exact model and see what is the latest version. There you will have to download the corresponding file to later add it and have the updated firmware.
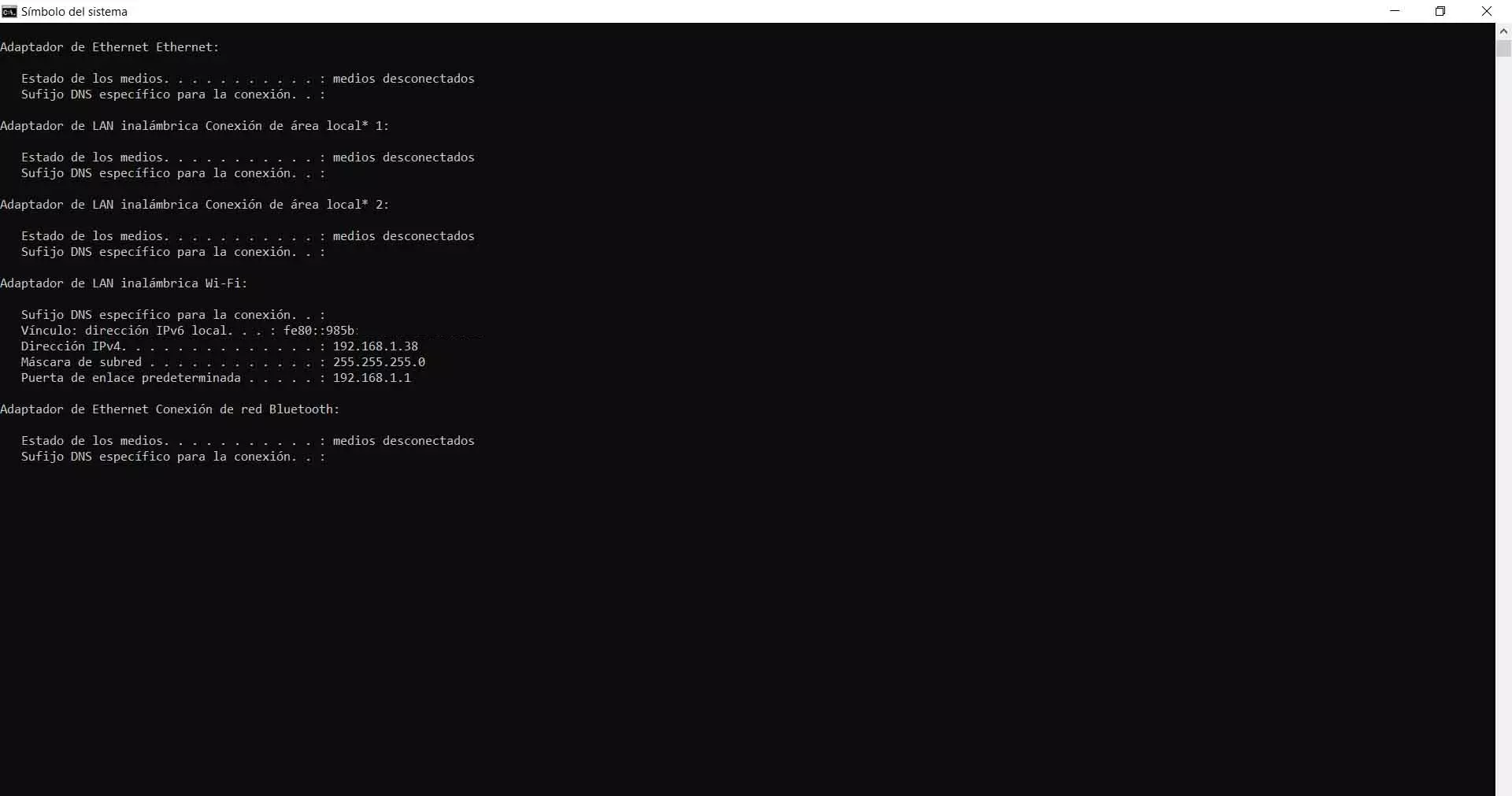
To update it manually you will have to enter the router, which is usually through the Gateway 192.168.1.1. If you don’t know what the default gateway is, you can find out from the Windows Terminal and by running the ipconfig command. There it will show you what it is.
Once inside, it will depend on the model. Normally, you have to go to the Administration section and click on Update or similar. When you are there, click on Browse and upload the file that you have previously downloaded from the router’s website. It is important that you always download that file from trusted sources.
protect device
Although protecting the router does not always mean correcting vulnerabilities, it can help ensure that an attacker does not end up exploiting them and does not compromise security. Therefore, you should always use a good access key to enter the settings and also to access the Wi-Fi network.
That password must be unique and totally random. You should never leave the one that comes default when you buy a router or the operator installs it for you. It is important that you meet the requirements of a good password, such as length, letters (both upper and lower case), numbers, and other special symbols.
Always use good encryption
The encryption that you use for Wi-Fi is going to be essential. You have seen that a well-known vulnerability was known as KRACK, which was used to access WPA-2 networks. The ideal is that you use current encryption and avoid those that are obsolete, such as WEP or WPA, since there are tools that allow you to exploit them.
Currently the most secure encryption is WPA-3. However, WPA-2 is still a good option as long as you have your devices up to date to fix the KRACK bug. Not all computers support the latest WPA-3 option, so sometimes you will have to.
In short, as you have seen, router vulnerabilities are a very important problem. It is essential that you correct them as soon as possible so as not to compromise security and be able to surf the web with optimal performance. The ideal is to detect them in time, before a hypothetical intruder can exploit them and cause problems.