Passwords are our first line of defense for our accounts against cyber attacks on our accounts. These passwords that we use to log in can be more or less secure. Security is determined by the number and type of characters used in its generation. Secure passwords are more difficult to create, and more so if we intend to learn them by heart. For that reason, on some occasions we choose to reuse them without thinking about their possible consequences. In this article we are going to see the dangers of reusing passwords and how they put your accounts at risk.
Why are old passwords reused?
A fairly high percentage of users reuse their passwords in one of their accounts. However, it must be recognized that reusing it reduces our security, but despite this, it is a fairly widespread practice. Apparently we could find a number of reasons why this happens:
- Some assume that they are invincible to cybercrime, nothing has ever happened to them and with so many users out there, how are they going to play.
- Others don’t know that passwords shouldn’t be recycled.
- Another party is not willing to have many passwords and use a password manager.
As we will see later, the dangers of reusing passwords are many. Therefore, we must prepare ourselves to avoid this widespread custom. (www.brandxhuaraches.com)
The dangers of reusing passwords
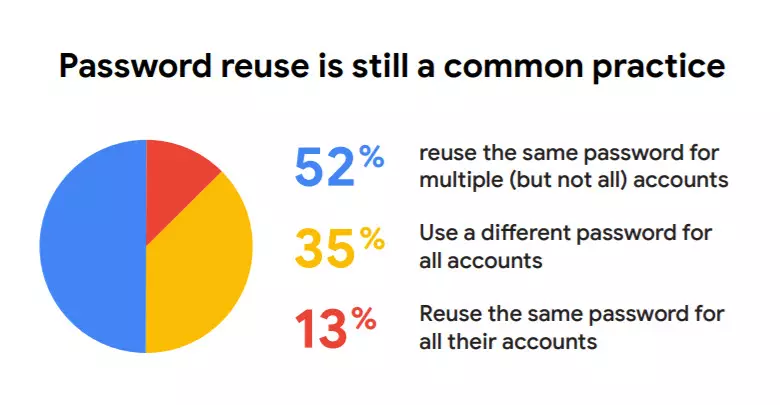
Despite the great awareness that is being made in this matter, many users continue to recycle their passwords. In a survey carried out by Google and Harris, it was revealed that 52% of users still use the same password for several of their accounts. In that aspect, it is not an encouraging fact because, as we will see below, this practice can compromise our security.
The dangers of reusing passwords are as follows:
- Can compromise multiple accounts. On occasion we may have a strong password for one account and be tempted to use it on all of them. At first it seems that it is not so dangerous, but it is. An example may be the Facebook data breach in which our account could have been exposed. Thanks to that information they would already know our e-mail and would have access. In addition, other possible accounts in which we use that email could be exposed if they use it to recover the password.
- we would be putting our work accounts at risk. In this aspect, in addition to our security, we would also be putting that of the company at risk. Also, it could lead to a loss of prestige in our work environment.
- Could use our accounts for phishing or other attacks. They could send emails impersonating our identity. Additionally, cybercriminals could ask in an email to click on an email attachment, download malicious files, or provide sensitive and personal information. If they think it’s us, out of trust, they can access the petitions and new victims appear.
You may be interested in these tips for creating a strong password.
How to mitigate this dangerous mania
The first thing we have to start with is replace default passwords. It is not good to leave the ones that come by default as “admin” or “1234”. Although default passwords are very easy to remember, they are also very easy for cybercriminals to hack. If it is a company, employees should be trained. A series of training courses can be offered to them so that they can deal with phishing, ransomware and other types of attacks. In this sense, workers must be advised to:
- They do not share their passwords with co-workers.
- Never reveal your password to anyone by email or phone call.
- If they are in doubt as to whether their password has been compromised, they should change it.
- Don’t use your computer on public Wi-Fi unless they use a VPN.
It would also be a great idea enable two-factor authentication in the services that allow it. Thus, in the event that someone stole our password, they would need a second step to be able to log in. That second action that we need to perform is to insert a verification code that we receive from 2FA applications such as Google Authenticator or via SMS. For example, we could start by activating Google’s two-step verification since many of us have an account.
Finally, we must not forget that it is highly recommended use a password manager. In addition to serving us to store our passwords, many of them also generate secure passwords for us. Some that we could use are LastPass, Keepass or Passwarden.