Thanks to a report by VirusTotal, a website with which we can analyze suspicious files and URLs to detect types of malware, we can learn about the evolution of ransomware in 2021. This report is designed to help both professionals and the general public to better understand the nature of ransomware attacks.
Next, through a series of graphs and brief explanations, we will see the most affected countries, the most used ransomware families and more.
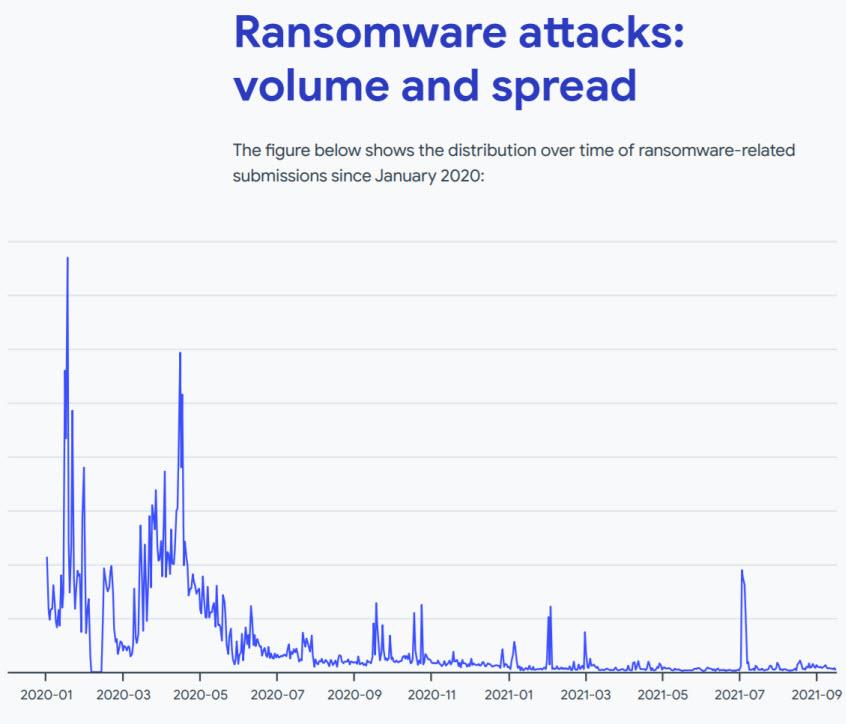
Ransomware attacks in 2021
This first graph will show us the volume of the attacks. It presents us with both 2020 and part of 2021. Thus, in the first two quarters of 2020 there were some notable spikes that can be attributed to the GandCrab ransomware family. It should also be noted regarding ransomware in 2021, that there was a major peak in the first quarter of 2021, and also another in July 2021 related to the Babuk ransomware family.
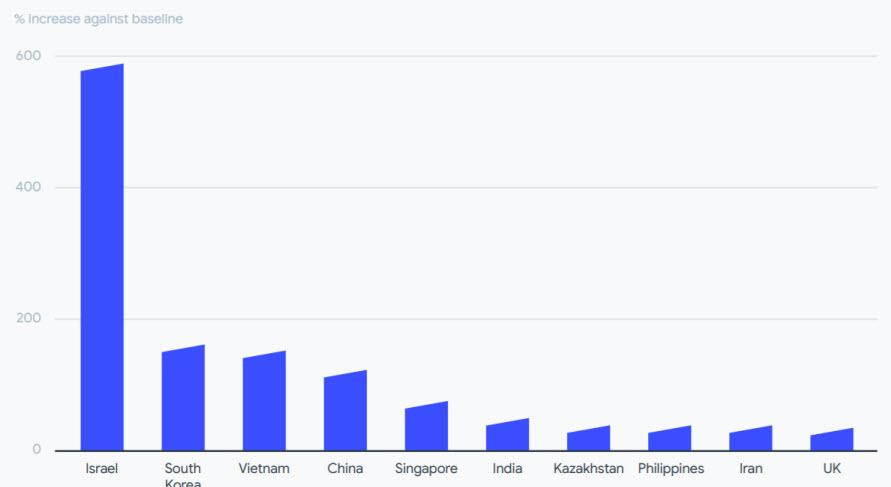
On the other hand, the 10 most affected countries according to the number of shipments to VirusTotal were Israel, South Korea, Vietnam, China, Singapore, India, Kazakhstan, the Philippines, Iran and the United Kingdom.
In this regard, Israel should be highlighted, in which case it has increased by almost 600% in the number of submissions compared to its baseline.
Different families of ransomware
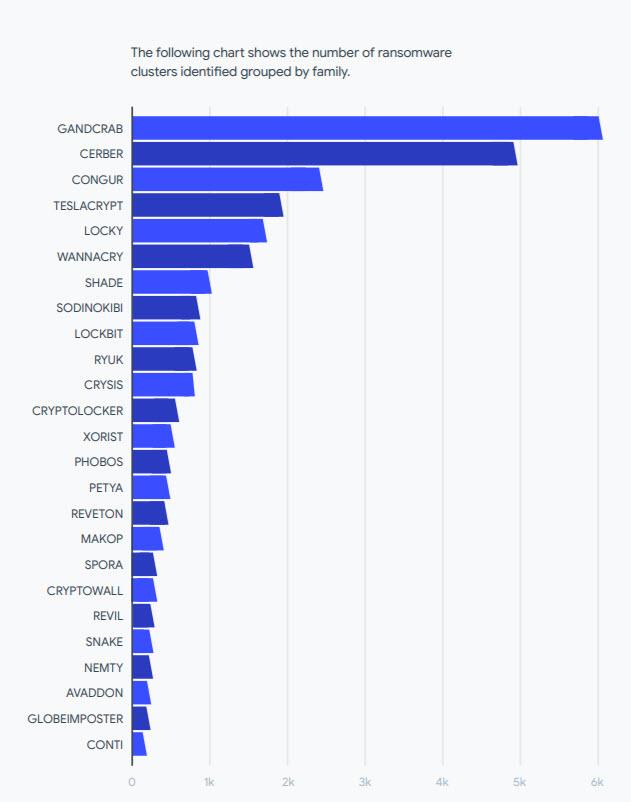
The following graph on ransomware in 2021 and 2020 shows us the number of identified ransomware groups grouped by family.
Now let’s see which are the most active ransomware families.
As can be seen, the most active are Gandcrab with 78.5%, Babuk with 7.61% and Cerber with 3.11%. It is also surprising that Wannacry is among the top 10 ransomware families in 2021. It is estimated that this would be a holdover from a previous detection that still applies to some current ransomware families.
Sophistication, distribution and conclusions
Refering to ransomware sophistication in 2021 some conclusions can be drawn. One of them is that the 95% of ransomware detected were Windows-based executable files or DLL libraries. It should also be noted that another 2% were Android-based.
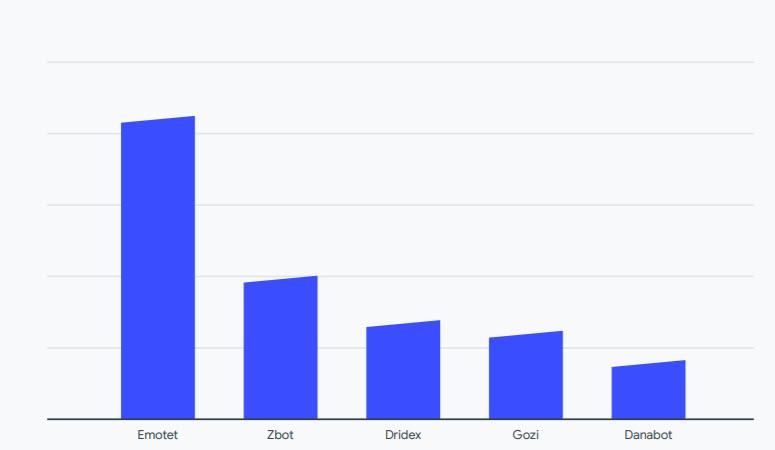
Furthermore, around 5% of the analyzed samples were associated with Windows elevation of privilege exploits and SMB information disclosures and remote execution. These were the most used artifacts for the distribution of malware, among which Emotet stands out.
One of the conclusions of the VirusTotal report is that attackers do not seem to need exploits other than for privilege escalation and the spread of malware within internal networks. Also that Windows represents 95% of the targets of ransomware when compared to 2% that Android has.
Finally, if you want to know the ransomware report in 2021 and 2020 you can access it from here.