If you don’t want to have security problems with your NAS server, you should never expose the management port to the Internet. Although we think that by using a good password for our administrator user, with two-step verification, changing the default port of the NAS and even enabling HTTPS, the truth is that if you open the port on the router to the NAS, you are in serious danger of your computer being hacked. Cybercriminals take advantage of remote access to this type of device to exploit a vulnerability and gain total control, today at RedesZone we are going to tell you what you can do to access it from the Internet safely.
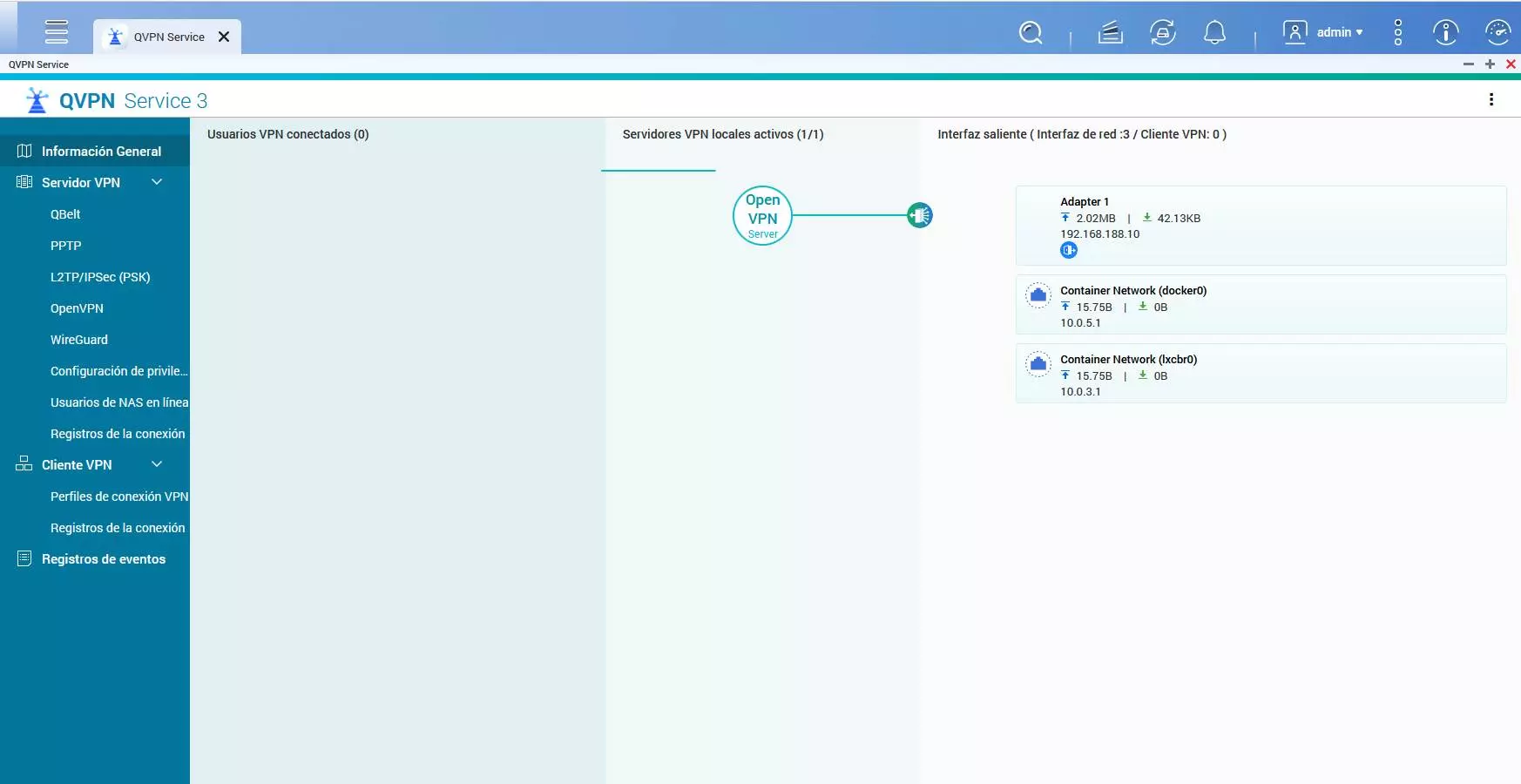
Access through the VPN server of the NAS
This solution is the most recommended of all due to its ease of configuration and the security it provides. If we configure the VPN server of the NAS server itself, and open the corresponding port on our router to connect from the Internet, we will be able to connect remotely to the computer with maximum security, and all this as if we were connected through the local home network.
To be able to connect in this way, we will have to configure the OpenVPN server or the VPN server with WireGuard, or configure both simultaneously for different types of uses, since generally all systems are compatible with several protocols that we can use simultaneously without problems. Thanks to the possibility of configuring a VPN tunnel, we are going to access our computer securely, since for the connection it is necessary to have the corresponding certificates and private keys that are only under our domain.
In this way, in the router we only have to open vpn server port, and we will not directly expose the NAS management web page, protecting it from possible attacks by cyber criminals. If a cybercriminal performs a port scan and finds the open VPN port, there is not much they can do as they do not have the private keys to connect to it.
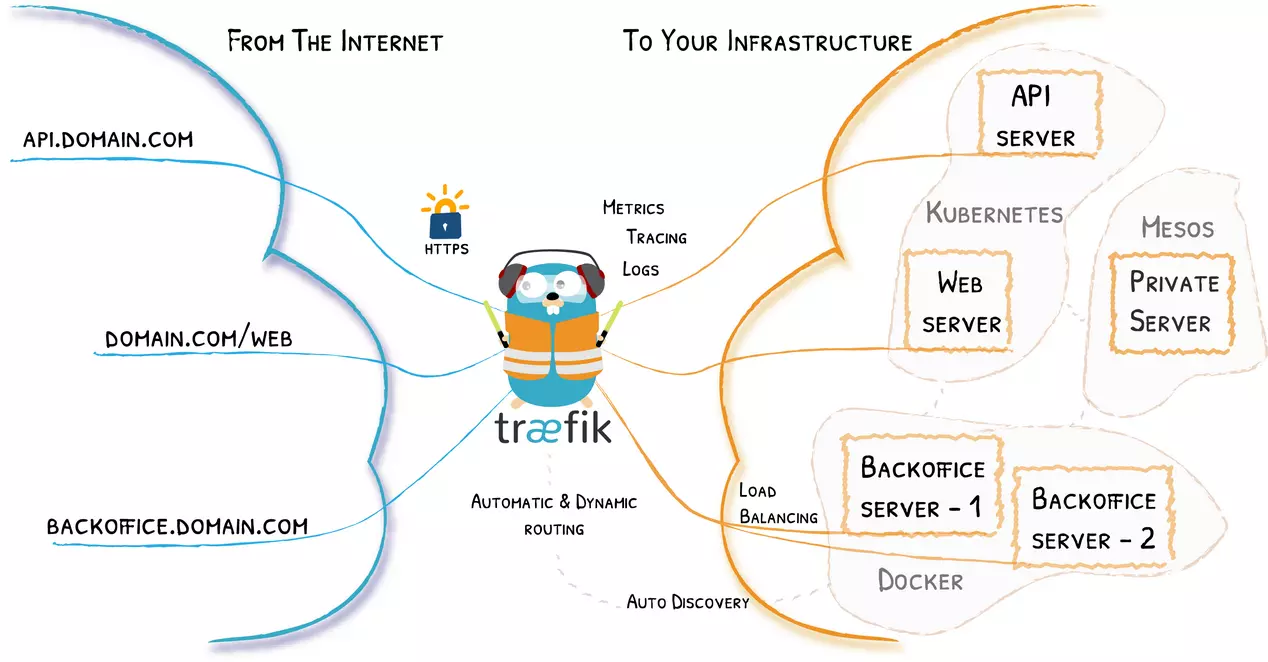
Set up a reverse proxy with additional authentication
In recent years, NAS manufacturers are integrating a reverse proxy into their operating systems natively, however, you could also install the popular Traefik reverse proxy as a Docker container. Manufacturers such as QNAP, ASUSTOR or Synology allow you to install Docker containers to further expand the functionalities of the equipment.
In this case, if we install a reverse proxy, we will only be able to access the server administration website by entering a specific subdomain or URL, which clearly makes it difficult for a cybercriminal to connect. In this case, we will only have to open port 443 of the reverse proxy web server, to later go to the server administration website.
Reverse proxies allow us to add additional security measures to mitigate and even prevent possible attacks and intrusions to the different services. Here are some of the most common and recommended security measures that we should apply:
- Limit access to different resources by country, based on the source IP address.
- Block IP addresses based on attempts to access the computer.
- Add a first authentication to be able to access the shared resources, this authentication can be basic with username and password, or use Oauth to authenticate with Google directly.
- Add a secure header policy to use.
- Limit the number of requests per second, to mitigate many attacks that could be carried out.
As you can see, configuring a reverse proxy with sufficient security is also one more method to connect securely to our NAS. What you should never do is expose the administration port to the Internet, because anyone could access and exploit a security flaw in the web server.