- Create strong passwords that are not in dictionaries and have a certain complexity.
- Force users to change their passwords to comply with the new access password policy.
- Configure password expiration, to force users to change their passwords from time to time.
Next, we are going to see how to configure a good password policy on our server or PC with Debian or Ubuntu.
Set up a strong password policy
The first thing we must take into account to configure a robust password policy is to be administrators, we must have root privileges to be able to make all the changes, since they affect all the users of the operating system. Once we have administrator permissions, then we can begin to perform the different steps to correctly configure the password policy.
Install the libpam_cracklib tool
The first thing we are going to do is install the libpam_cracklib library, this library is in charge of verifying that the password that you are going to enter is not part of a dictionary, that is, that it is not a simple word. It will also check that the password is not the same as another that you have used previously, that is, it will not let us reuse the passwords that we have already used previously. Nor will it allow us to reuse passwords that have only changed one character, let’s imagine that the new password is “Pepe123.”, Since the new password cannot be “Pepe123-” because we have only changed one character. Other characteristics of this library is that it checks if the new password is too short, if it is not very complex, and even allows us to know if it does not have a single character entered several times in a row, in order to make the password more complex.
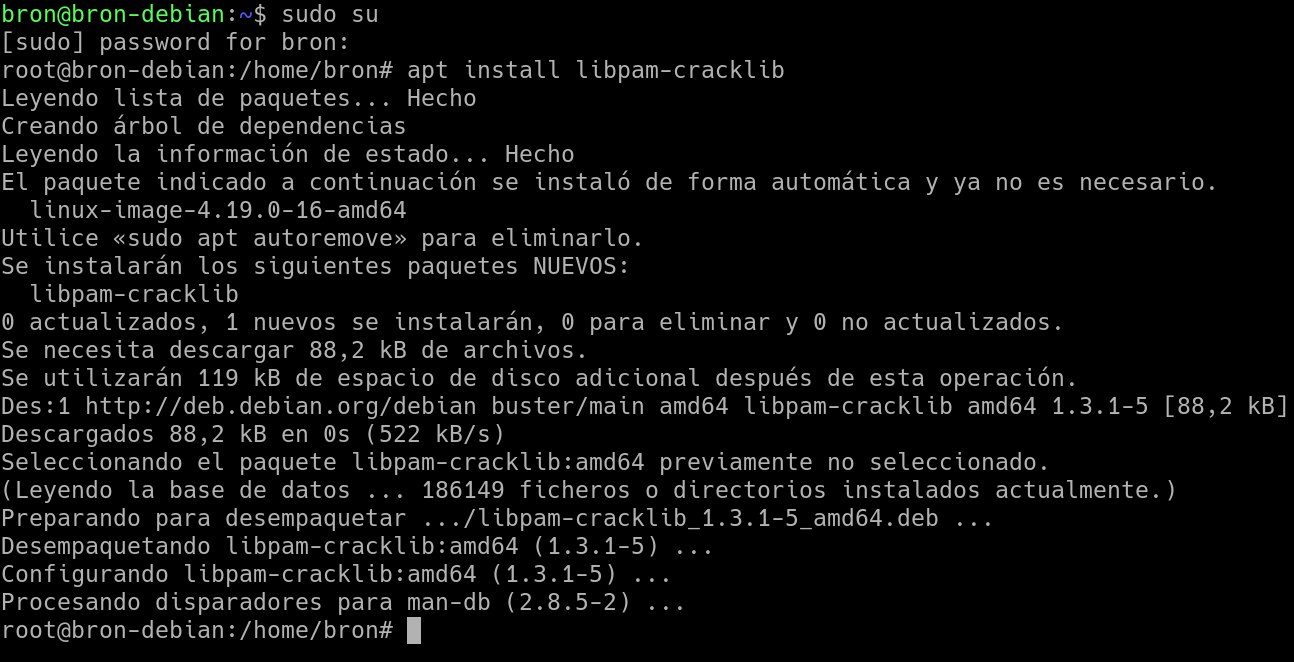
We must bear in mind that setting a strong password is very important, as it is the first line of defense in the security of our operating system. To install this library, we simply have to execute the following command:
sudo apt install libpam-cracklib
If you use “sudo” in your operating system, you will have to put this command before the installation command, otherwise, if you are in root mode you will not need to use it. Before continuing, we must indicate that the installation of this library is very important, because thanks to it we will be able to configure the password policy as we want.
Edit the configuration file
Once we have the library installed, now is when we are going to edit the file that is located in /etc/pam.d/common-password. But before editing it directly, we recommend you make a backup copy of this configuration file, in case we put any wrong configuration, to be able to return to the factory settings easily and quickly.
To make a backup copy of this file, just execute the following command and put the path that we want:
sudo cp /etc/pam.d/common-password /root/
Once done, we open the file with superuser permissions to be able to edit it, we can use vi, vim, nano or another text file editor by console, we will use nano. You could also use a graphical text editor, but always with root permissions because otherwise it will not let you edit it.
sudo nano /etc/pam.d/common-password
Now we will see the complete configuration file of the operating system:
Once we are inside the editor, we must locate a line similar to the following:
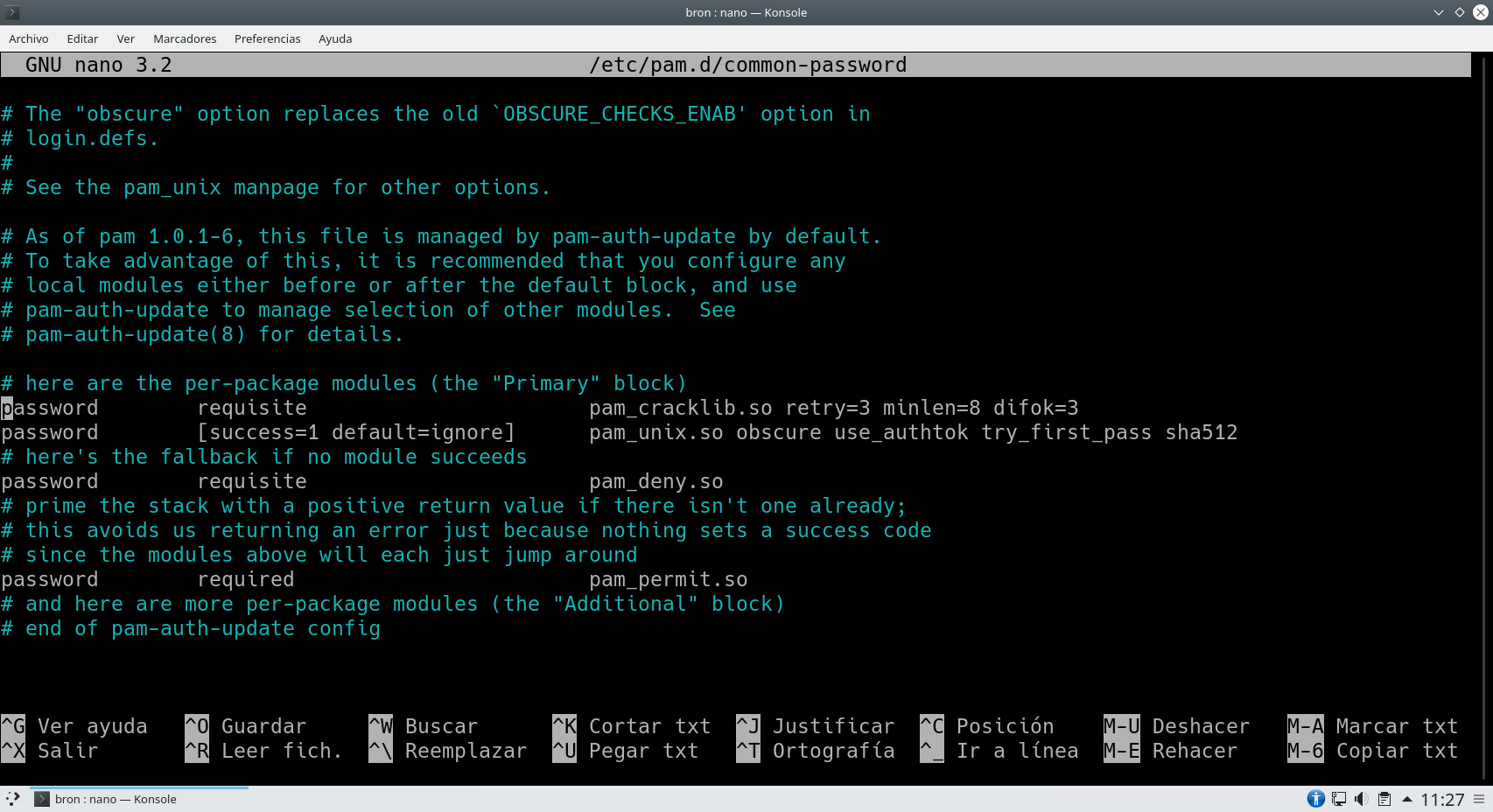
password requisite pam_cracklib.so retry=3 minlen=8 difok=3
In the following image you can see where it appears:
This is where we must edit it, and we will have the following options to configure it as we want.
- retry: number of attempts before the system returns an authentication error and expels us.
- minlen: is the minimum length of the password, by default it is 8 characters.
- difok: number of different characters that the new key must have compared to the old one.
- ucredit: uppercase characters that must have a minimum or maximum.
- lcredit: lowercase characters that must be at least or maximum.
- dcredit: the number of digits it must have as a minimum or maximum.
- ocredit: the number of other characters (symbols) that the key must have as a minimum or maximum.
The ucredit, lcredit, dcredit and ocredit options can have negative or positive numbers, to define if we want it to have a minimum or maximum range, for example:
- lcredit = -2: means that it must have at least 2 lowercase characters.
- lcredit = + 2: means that it must have a maximum of 2 lowercase characters.
And it is the same with the rest of the lcredit, dcredit and ocredit options.
Configure the key policy to apply
Once we know all the configuration options that we have at our disposal, we are going to choose the key policy to configure. An example of a key policy could be the following:
password requisite pam_cracklib.so retry=3 minlen=12 difok=3 ucredit=-3 lcredit=-3 dcredit=-3 ocredit=-3
With the previous policy we will have:
- Minimum password length 12 characters.
- If we change the password, there must be at least three differences.
- 3 uppercase characters, 3 lowercase characters, 3 digits and 3 symbols minimum
We have not put any character as a maximum, but we could also incorporate it, to limit the number of characters of the same type that is allowed, however, with this key policy we believe that the key is complex enough to avoid problems.
Check the new key policy
Once we have it configured, we are going to change the password of our own user so that it fits perfectly with the new password policy that we have configured. To change the password we must execute the following order:
sudo passwd
We will have an assistant where we will have to indicate the new password, so that it fits perfectly with the previous policy. Depending on the password that we enter, we could see a different error, for example, it could tell us that the key is too simple, it is a dictionary word, it is too short, etc. Once the new password that we have entered complies with the policy, it will allow us to change it without any problem.
Force other users to change their password
Debian gives us the possibility to force the password change for the next user login, in this way, they will not be able to avoid the new password policy that they must comply with. In order to force users to enter a new access password, the administrator user must execute the following command:
passwd -e USUARIO
The “-e” argument forces an expiration of the user’s password, and at the next login you will need to enter a new password that conforms to the new password requirements of the operating system.
Configure password expiration for users
If we want to configure the expiration of passwords for users, we can also use the passwd command to carry out this configuration for each and every one of the users of the system, or individually. To define a password expiration and force users to change it before the term expires, we must execute the following command:
passwd -w 5 -x 30 USUARIO
The “-x” argument means that users must change their password at most every 30 days. The argument “-w” means that it warns us 5 days before the password expires, to change it, in this way we remind the user that he must change the access password.
It would also be highly recommended to configure the inactivity of the account, if the user does not change the password after the expiration of the key, that it is put as inactive and it is the system administrator who has to activate it again. Let’s imagine that we want to mark an account as inactive if a day has passed since the expiration of the key, in this case the configuration would be:
passwd -w 5 -x 30 -i 1 USUARIO
The passwd command allows us to put different arguments in the same order, we recommend that you read the man pages of this tool where you will find all the available configuration options.
As you have seen, configuring a good password policy on our server with Debian or Ubuntu is really simple, we will simply have to install the library and make some adjustments, in addition, it would be highly recommended to force current users (if they exist) to create a new access password.