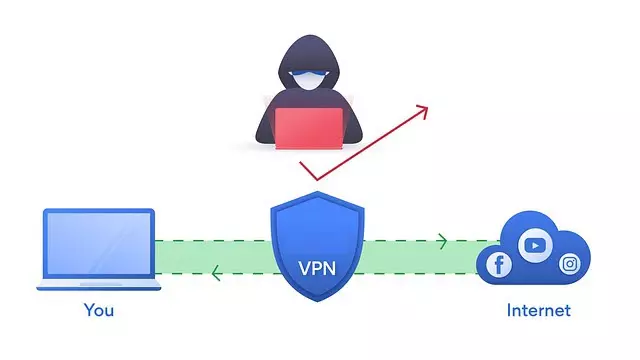
We live in an increasingly digital world where the accounts of our platforms and services are increasingly valuable to us. Our first line of defense is the password, which must be strong. Even so, it could be compromised, so it is convenient to activate multifactor authentication or 2FA in our accounts. The reason is that even if they were to get our password without a second step that we only have, they wouldn’t be able to log in. This second requirement can be obtained with a verification code obtained with an application, SMS and more. However, we can go one step further and use U2F or Fido security keys. In this article we are going to see how you can get the best security using hardware-based 2FA authentication.
Hardware-based 2FA authentication
Nowadays, some of our accounts are priority and very important for us, for example, those of Google, Microsoft or Dropbox. The reason they are vital is because they contain a lot of sensitive personal information. Whether it’s our company documents, our own photos and videos, accounting and bank documentation, we want to keep this information safe. In this regard, there is no better way to protect our online accounts than using hardware-based 2FA authentication.
This is where security keys come into play, because they are easy to use and put an end to phishing attacks. In addition, they are relatively cheap and much more secure than 2FA authentication with SMS, since they can suffer from SIM Swapping attacks. These security keys can be obtained in a wide variety of formats such as USB-A and USB-C, Lighting and NFC. Therefore, we are going to have many options available to be able to use them.
Kensington-Verimark
Smartphones aren’t the only devices that can benefit from the convenience and security of biometric fingerprint technology. Thanks to this model from the prestigious manufacturer Kensington, we obtain a security key that has Fido and U2F certification.
The KensingtonVeriMark It has a fingerprint reader with 360 degree detection. After having configured our fingerprint we can use it to log in to a computer or to our online accounts such as Facebook or Google. As for its operation, it is very simple, it works just like the fingerprint reader of a smartphone.
YubiKey Bio
YubiKey Bio is another good example of hardware-based 2FA authentication that is supported by operating systems and browsers like Windows, MacOS, Chrome OS, Linux, Chrome, and Edge. Regarding security measures, it supports FIDO2, WebAuthn, FIDO and U2F.
It should be noted that it meets the most stringent hardware security requirements with fingerprint plates stored in a secure element of the key. Their way of proceeding is by saving the fingerprint in a separate secure section.
We can find it in two different USB-A formats:
Or also in USB-C format:
Thetis Fido U2F
Thetis Fido U2F, as you can see in the image below, it is a security key that looks like a USB stick. In terms of security, it is compatible with U2F and Fido.
Regarding the design, it has a 360 ° rotating metal cover that protects the USB connector when not in use. Also, a positive thing is that it comes with a USB-C adapter to be able to use it in this type of port. In this regard, it is increasingly common for both computers and mobile devices to have a USB-C port. It will give us one more option to use it.
Yubico YubiKey 5 NFC
Another good security key with hardware-based 2FA authentication is the Yubico YubiKey 5 NFC. It can be said that where it stands out is because it allows it to be used with both USB-A and NFC ports, which will offer us the versatility of wireless.
This model is made to protect our online accounts against phishing and account theft. In addition, it has multi-protocol support including Fido (U2F, FIDO2), Yubico OTP, OATH-TOTP, Smart Card (PIV) and OpenPGP.
Yubico YubiKey 5Ci
Yubico YubiKey 5Ci It is another security key that stands out because it is designed both for those who want to use it with a USB-C port and for those who want to use it with Apple’s Lightning connector.
Regarding security, it supports many protocols, such as U2F, FIDO2, Yubico OTP, OATH-TOTP, Smart Card (PIV), OpenPGP. It’s going to provide us with a challenge response capability to ensure strong hardware-based authentication.
Thanks to these security keys and their hardware-based 2FA authentication, we will be able to keep our accounts more secure.