In the case of SAMBA, in Linux, the way to connect from Nautilus or terminal would be:
smb: //87.222.xxx.xxx
This address is an example, since there we would have to put the corresponding one.
Although it is generally sufficient to open the port 445, it could also happen that it is necessary to open port 139. This will allow you to access files remotely and configure things like access with username and password.
Therefore, we can say that SMB, CIFS or SAMBA is a very simple and easy-to-use network protocol, which is used to share files between computers. However, as we will see, it is not a good idea to have it activated and it can be a significant security problem.
Why SMB / CIFS is dangerous
We have seen that SMB / CIFS is a very simple protocol, but it must be mentioned that it is also dangerous. Of course, there is no denying that it is very useful to share files on a local network with other computers without having to carry out complex configurations and all very quickly.
But why is it unsafe? It should be noted that the traffic of SMB / CIFS / SAMBA is not encrypted. Anyone who could intercept our communications, such as a hacker through a Man in the Middle attack, could intercept all the files we send. Even our own operator would have that capability. On the other hand, if we do not use a password to control access to the server, anyone could access it. Similarly, if we use a password will travel the network unencrypted, in plain text, and could also be stolen by a hypothetical attacker.
We must indicate that the latest versions of SMB 3.0 onwards do support encryption of communications in authentication, and also when transferring data through the local network, however, in most cases the SMB 2.0 version, so we will not have encryption of any kind.
But we must not forget about vulnerabilities what’s in these protocols. In fact, one of the most important to hit Windows in recent years, EternalBlue, the NSA vulnerability used by WannaCry, is based on an SMB flaw. Keep in mind that this ransomware caused havoc through this protocol used only on the LAN, so we can imagine the danger if it could have been used by default through the WAN.
It is not the only protocol that puts us in danger
Therefore, we can say that SMB / CIFS is not a secure protocol for WAN, but not for LAN either. However, he is not the only one who can put us in danger. One of them is the known FTP. In this case it also sends the user names and passwords in plain text, as well as the files in unencrypted network traffic packets.
Another protocol that is also a danger is Telnet. In fact, in addition to sending users and keys in plain text, it also allows you to execute code. This can jeopardize our safety. We must bear in mind that these protocols that we have mentioned, FTP and Telnet, do have others that are secure and encrypted. We are talking about SFTP / FTPS and SSH. There our data would be protected. This is not the case with the SMB / CIFS / SAMBA protocol, which does not have this encryption.
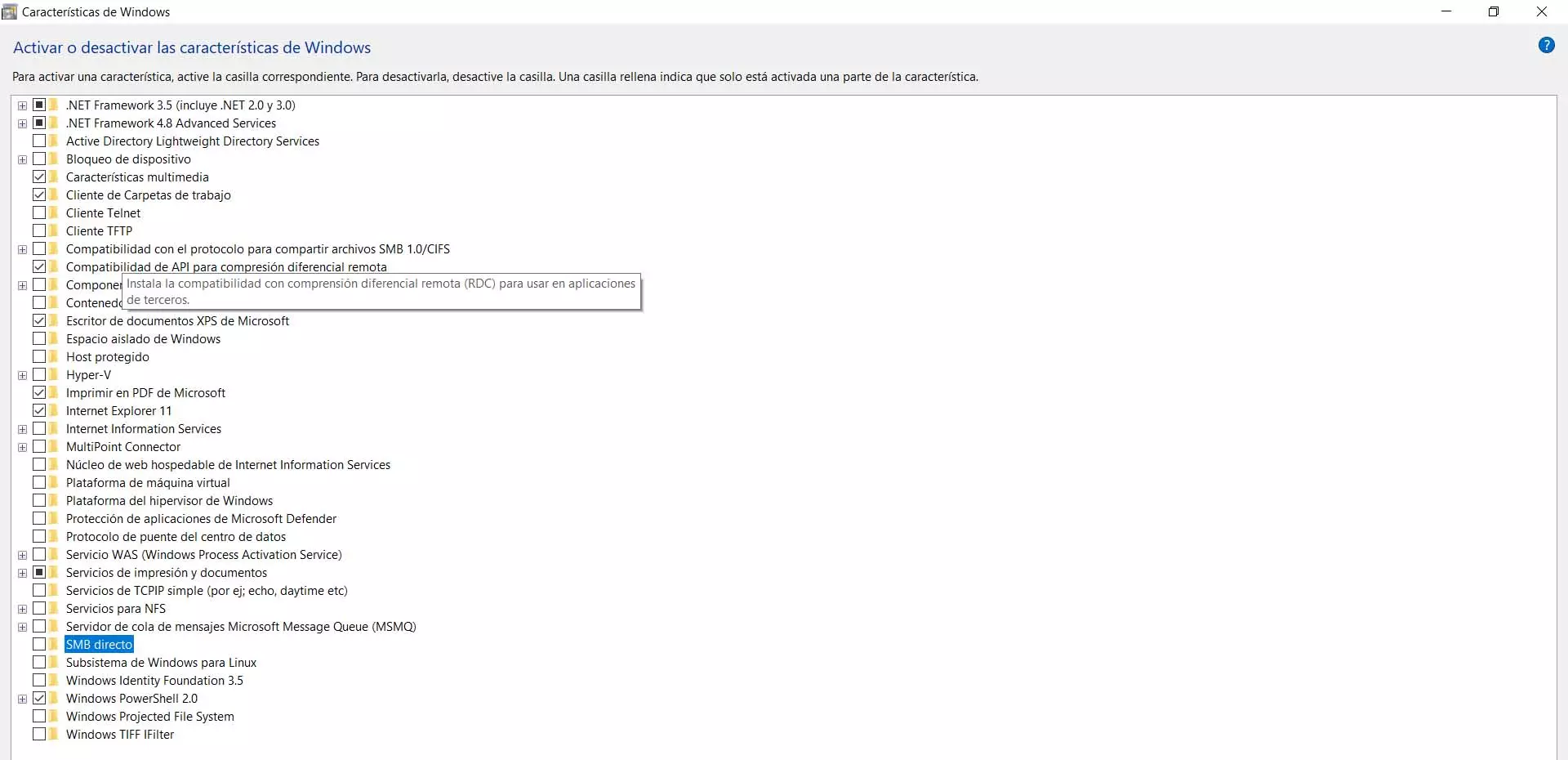
How to disable SMB in Windows
After explaining why it is not good to have SMB / CIFS enabled in Windows, we need to explain what to do to disable it. However, it should be mentioned that the normal thing is that we already have it configured like this, although the operating system allows us to activate it if we need it for something.
To disable it or verify that it is not really activated, we must go to Start, enter Control Panel, go to Programs, Programs and Features and there we select Enable or disable Windows features. There would appear SMB 1.0 / CIFS.
But, as we have indicated, the normal thing is that if you have updated Windows that feature does not appear as enabled. However, you can verify that it is not really activated, in the same way that you can verify it with Telnet or FTP Client.
If for any reason you need to enable it, you just have to check the box. Of course, you must know the risks and understand that you are really going to use it for something. Otherwise, it is best not to have these insecure protocols enabled in Windows, as they could be used by a potential attacker to steal information.
Conclusions to enable or not SMB / CIFS
In short, we can say that the SMB / CIFS protocol, as well as its implementation in Linux SIMBA, we should not have them active on our computer. They are not safe when sending plain text files. This also includes passwords and usernames, which could be accessible to any intruder.
Therefore, if for any reason you have activated these protocols or have considered doing so, the ideal is to check in Windows that they are not configured. This also includes others such as Telnet and FTP, as we have seen. In all of these cases, the information we send and receive travels unencrypted and can be exposed on the web. Sometimes the best security is to check the system periodically and verify that we do not have these types of insecure protocols.