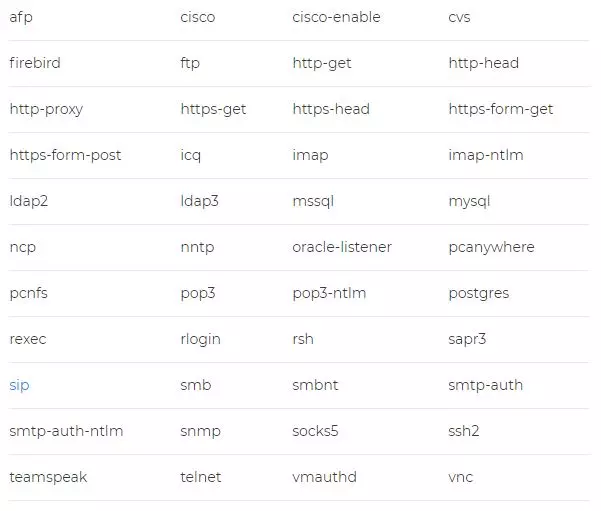
Hydra is totally gratuitous and in addition to Open Source. It has more than 30 compatible protocols (operating systems, web pages, databases, etc.) where we can test and see if a password is exploitable or is really strong and we will be safe.

Hydra – Supported protocols
A peculiarity of Hydra is that it has been designed in a modular way. This means that any programmer could create their own modules that add new functions and features. Use brute force by combining a series of options recorded in rainbow tables or databases. If someone uses a key that is short, predictable, or repeating, they could break it.
How to download and use Hydra
Hydra is a free and open source application that we can download from GitHub. There we will see that the most current version is 9.2. It is available for Windows (through Cygwin), macOS, and also on Linux (and other UNIX systems). They also included compatibility with mobile operating systems, such as Android or iOS.
If you are familiar with Kali Linux, the popular distribution for ethical hacking, you should know that one of the tools it has incorporated is Hydra. We would not have to carry out any installation, since it comes with the serial system.
When we download Hydra on the computer, we will have to execute the command “hydra” for the main options it has. If we are using Linux we can also run “./xhydra” to see the graphical interface.
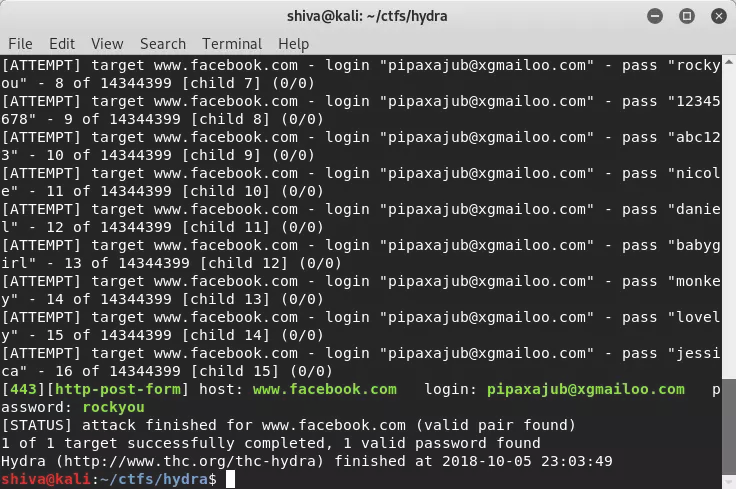
- In order to carry out an attack with Hydra we have to follow the following steps:
- Choose the target (IP address, domain, etc.) that we want to attack
- Select the protocol through which we will launch the attack
- Enter additional protocol parameters (if you have them)
- Choose the port (optional) through which to launch the attack
It offers a large number of options, so we can look at the GitHub documentation to see all the options. The main one is going to be exploiting a password, something that will help us understand if our password is secure or we should use another to avoid problems.
Keep in mind that this tool has been designed with the aim of test passwords and watch your safety. It is aimed at ethical hacking, but logically it can be used by third parties for bad purposes and seek to steal other people’s access codes. That is why we must always take precautions and be protected.
Steps to protect passwords and avoid attacks
So what can we do to protect our passwords and prevent cyber attacks? We are going to give a series of tips so that our access codes are safe and are not exploited by applications such as Hydra and other similar ones.
Generate reliable passwords
The main thing of all is to create passwords that are really strong. To avoid attacks with Hydra or any application of brute force, it is best to create keys that are not “common”. That is, we should never use our name, surname, basic words, dates, telephone numbers … All of this is what will be part of the dictionaries that use these tools.
Ideally, it should be totally random and long. We must use letters (both uppercase and lowercase), numbers and other special symbols. An example of a good password could be 3dU / -rl (eMb49 & “. As we can see, they are totally random characters, with no relation between them. That is exactly what will make brute force attacks fail.
Do not reuse keys
Another very important point is do not use the same password in various places. It would be a mistake, for example, to have the same password for Facebook as for the Gmail account. If they manage to find out about any of these services, a domino effect could occur and they end up accessing other accounts.
Therefore, you always have to create a unique key for each record on the Internet. We can help ourselves with password managers to be able to have all stored correctly and not have to memorize so many.
Enable two-step authentication
A very interesting complement to passwords is the two-step authentication. It is basically an extra layer of security. It is a second step that we will need to be able to log in, beyond having to enter the typical password.
This double authentication is usually a code that we receive by SMS or through an application. This serves to identify us. If someone managed to steal the password, they wouldn’t be able to log in without that second step. Therefore, it is one more way to be protected on the Internet.
Periodically change passwords
The importance of change Password occasionally. This will mean that we always have a reliable key and in case it is leaked by some error, we reduce the risk that it could end up in the wrong hands.
Whenever we change the password we must take into account the previous advice. It is important that it is secure, unique and that it meets all the requirements to be protected against attacks with applications such as Hydra and other similar ones that may exist.
In short, Hydra is a tool that we can use to test our passwords. However, it can also be used by a third party to carry out attacks and compromise our security. We need to always create reliable keys.