The new Windows 11 operating system, among the requirements to use it, is that the system integrates the TPM 2.0 module. There are several variants, there are physical ones and there are firmware type ones (fTPM). Well, researchers from the Technical University of Berlin have been able to hack the fTPM used in the AMD processors.
Microsoft’s obligation to use TPM is to ensure the integrity of the software. This module verifies the signature of the software and its integrity. This prevents or limits the execution of unsigned software or that may contain malicious code, ensuring the integrity of the system.
AMD processor security breached
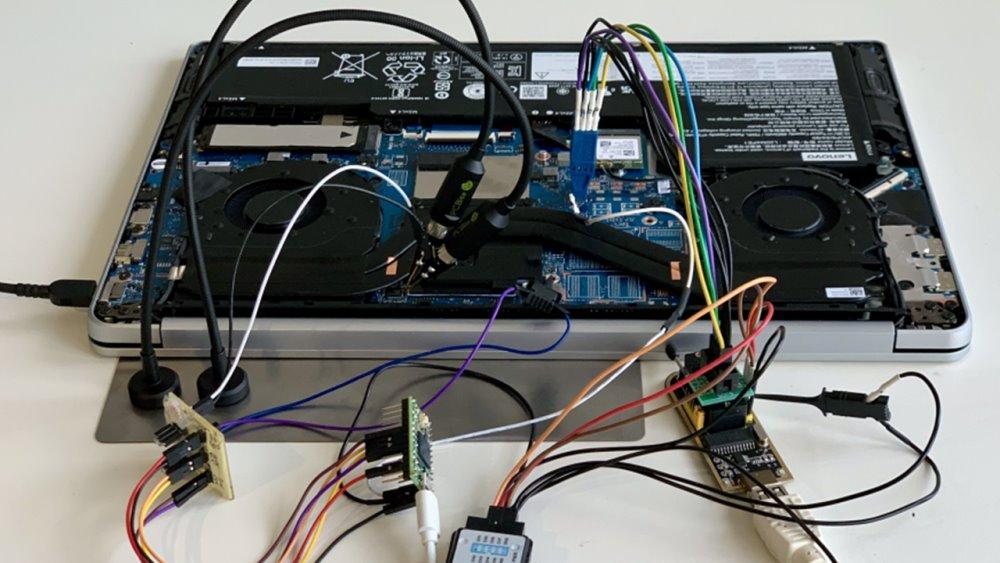
According to the researchers, in order to break security they have used components that can be purchased online at Amazon and AliExpress and that they cost about 200 dollars. They have shared on GitHub the components used and the code to carry out the attack.
They attack the processor security platform (PSP) of the chips AMD Zen 2 (Ryzen 3000) and Zen 3 (Ryzen 5000). There is no data in the report whether Zen 4 architecture processors are affected by this vulnerability.
On the positive side, this attack requires physical access to the computer for “several hours.” It requires significant time for the installation of all the elements. Also, it requires quite advanced knowledge of electronics. The most positive thing is that it cannot be exploited remotely through software.
Through this attack, researchers have had Full access to fTPM and encrypted data stored. What this access allows is full disk encryption using BitLocker. Something possible thanks to the fact that this vulnerability allows full access and control of the system.
As the researchers point out, to mitigate this security issue it’s not easy. The problem is that there is a fault voltage injection, something that it cannot be mitigated by software. AMD may fix this in future processor architectures and upcoming design tweaks.
The researchers point out that Intel has mechanisms that prevent this type of attack. As they indicate, Intel integrates a converged security and management engine (CSME) that prevents this type of attack.
Should I worry about this?
NO. Really, this vulnerability should give you pretty much the same, realistically. The reason is that cannot be exploited remotely through software, it requires have physical access to the computer. Also, installing the components requires time and different soldering.
Come on, exploiting this vulnerability is very complicated and slow, so it is irrelevant. It simply states that the TPM firmware is vulnerable. Although this element was really considered as an improvement of TPM 2.0. It is used to avoid an interface that is easy for malicious actors to attack.
What does AMD say about it?
At the moment, no official statement has been released about this type of attack and vulnerability. Of course, Tom’s Hardware has communicated with the company and a spokesperson has said the following:
“AMD is aware of the research report attacking our firmware Trusted Platform Module that appears to exploit related vulnerabilities discussed earlier at ACM CCS 2021. This includes attacks done through physical means, typically outside the scope of security mitigations. of the processor architecture. We are continually innovating new hardware-based protections in future products to limit the effectiveness of these techniques. Specifically for this document, we are working to understand potential new threats and will update our customers and end users as necessary.”