The main Internet browsers such as Mozilla and Google Chromesome giants of CDN like Cloudflare, and even the IETF organization, have been developing this extension of TLS for several years to have an encrypted point-to-point connection from the first “hello.” It must be taken into account that the content of web browsing, authentication on different websites, when we insert our cards on shopping websites, and much more, is fully encrypted point-to-point thanks to the TLS protocol. However, ECH will allow us to protect the identity of the websites we visit, making it impossible to know which website we want to access, something that does happen if we do not use ECH and have the popular SNI.
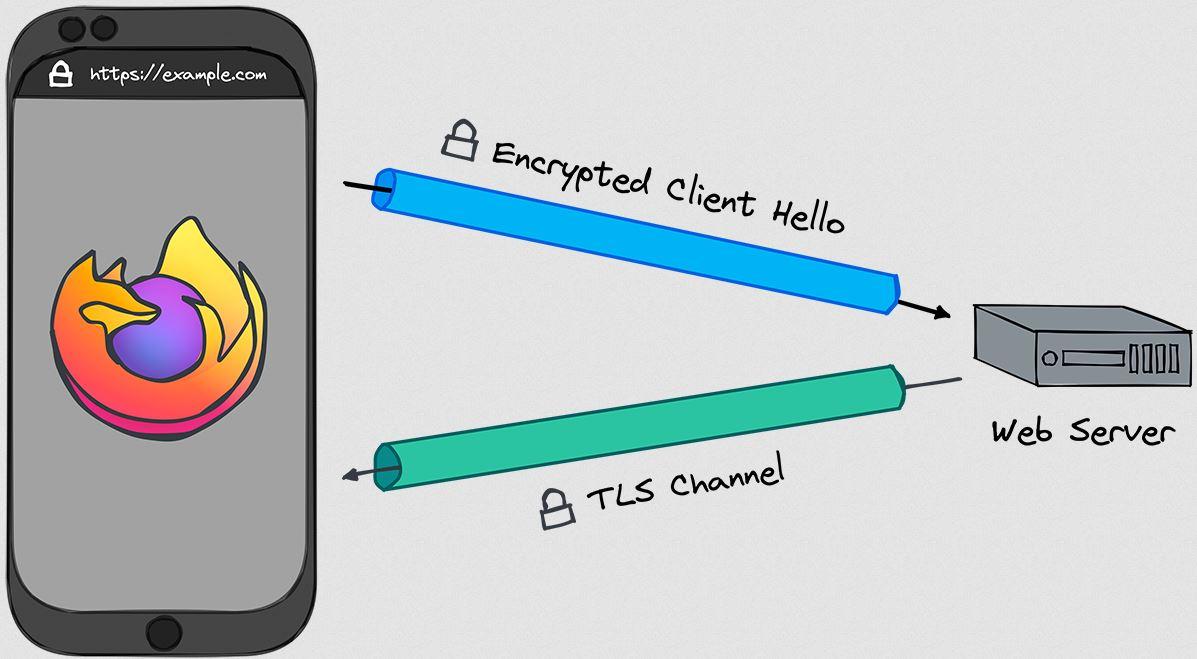
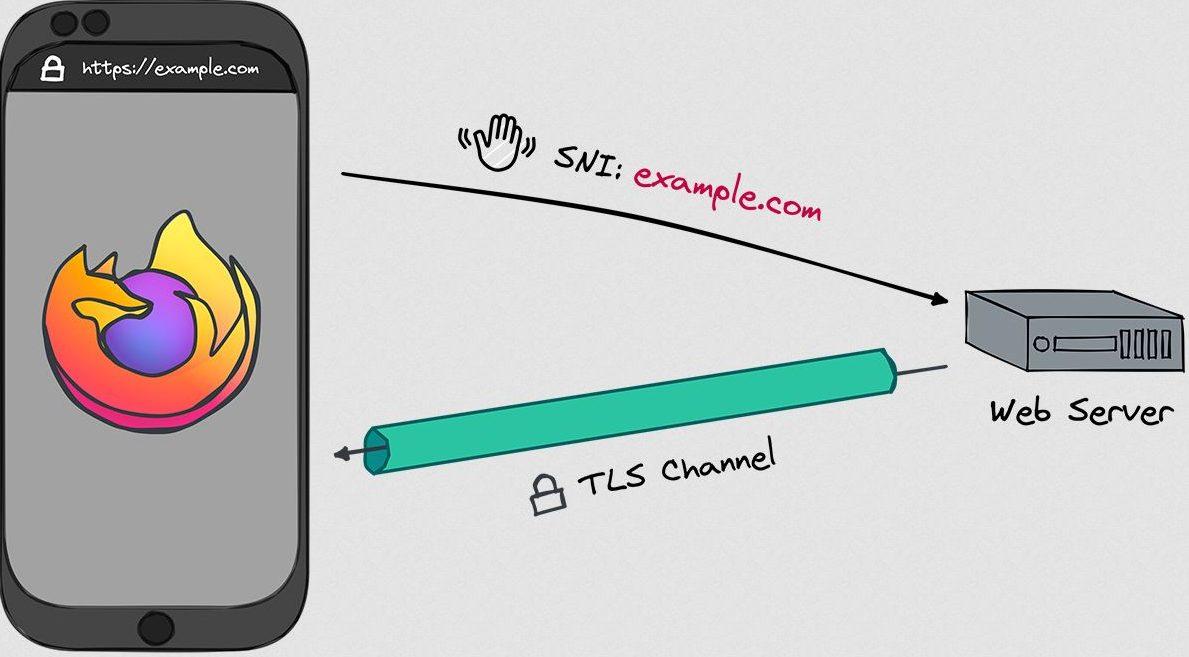
When a web browser connects to a website, the site is transmitted in the initial message and it is not encrypted, the communication scheme would be as follows:
The ECH extension is capable of using a public key obtained through the DNS system to encrypt this first message between the web browser and the website, protecting the name of the destination site to prevent blocking and improving user privacy. In the following diagram you can see that this message is fully encrypted:
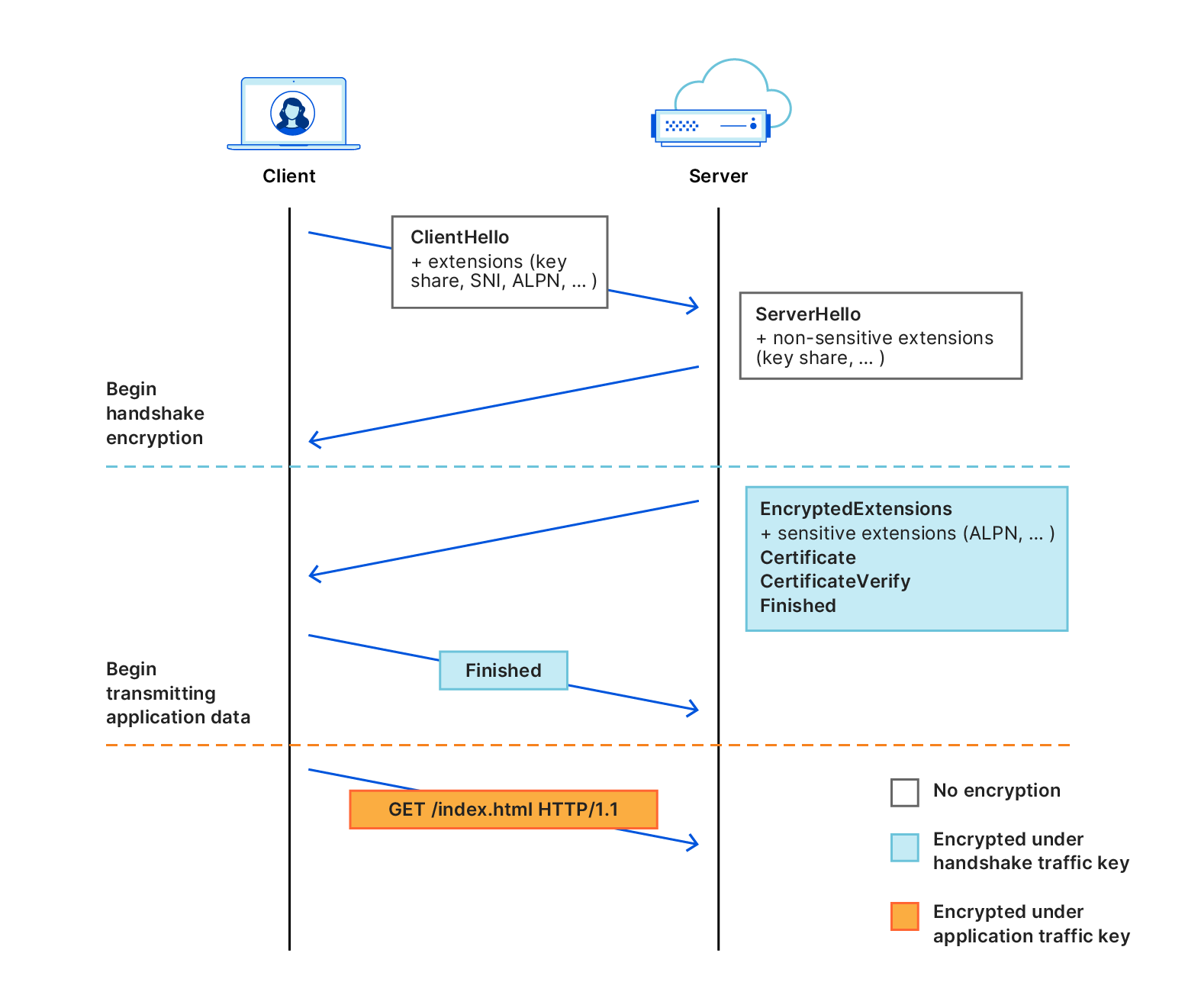
If you want to know in more detail how this TLS extension works, we recommend you see this complete message diagram between the web client and the server:
By activating this ECH extension in web browsers and also in web servers and CDN, we will have a greater privacy globally, preventing third parties from “spying” on our connections. It is very important that not only web browsers support this protocol, but also web servers and CDNs. Right now there are very few websites with support for this TLS extension, in fact, the giant Cloudflare activated it a while ago and had to deactivate it because there were many navigation problems through the different websites that are on its CDN, and it is still It is not completely “tuned” to be deployed en masse. In fact, Cloudflare had the possibility of using ECH individually on the websites you wanted, and due to these problems they have encountered, they have disabled this possibility and we cannot even enable it manually.
With ECH, will operators no longer be able to block websites for me?
Years ago the operators They blocked websites through DNS servers, meaning that if a client used their DNS servers they could not enter certain websites. With the popularization of Google and Cloudflare’s DNS servers, more and more users evaded these restrictions, unless the two Internet giants also blocked the domain, something that is not usually common if only copyrighted files are shared. Because of this, operators had to invest large amounts of money in systems to Examine all TLS connections your clients madebeing completely encrypted, they can only see the SNI field, which is the domain the user wants to enter, so they block it directly, returning a connection error.
Now with the ECH extension this is impossiblesince the entire connection up to the first “hello” is fully encrypted point-to-point, and operators will not be able to decrypt this connection without “breaking” the TLS connection, putting a digital certificate in the middle, which would cause that operator to be spying on all connections to their clients, since they would have “raised” the HTTPS connection.
It is also very important use DNS that guarantees security and privacyIn this case, we have to use both DNS over HTTPS (DoH) that we already have integrated into the main browsers such as Chrome or Firefox, and even DNS over TLS that we can configure directly on our router so that clients on the local network can make requests and receive DNS resolutions completely privately. When using DoH or DoT, DNS messages cannot be intercepted or modified on the fly.
Of course, all of these protocols can be combine with VPNs (virtual private network) to add another layer of privacy and security, especially since VPNs allow us to mask the user’s public IP address, and encrypt all traffic completely. In these cases it also makes sense to use ECH, because we will be protecting the identities of the websites we visit while we are connected to the VPN provider.
And what about parental controls?
At a domestic and also professional level, we have different types of technologies to filter the websites that can or cannot be visited through different devices. Right now, browsers like Chrome or Firefox use DNS over HTTPS to encrypt DNS requests, so if we have a DNS system at home like PiHole or AdGuard Home to filter these requests, we will not be able to block malicious or advertising requests. The same happens in the case of activating ECH, companies may not be able to block certain domains if we use it.
In these cases, both Mozilla and Google allow you to configure the activation or deactivation of this TLS extension in browsers, to allow or disallow the use of this feature. In the event that we want to implement opt-out options at the network level, we can do so without problems.
How to activate it in the Mozilla Firefox browser
The first thing we must check is that we have version of Mozilla Firefox 118 or later, and we will have to enable DNS over HTTPS for it to work, otherwise it will not be available, even if it is activated. Right now Firefox only allows it to be used if DoH is enabled.
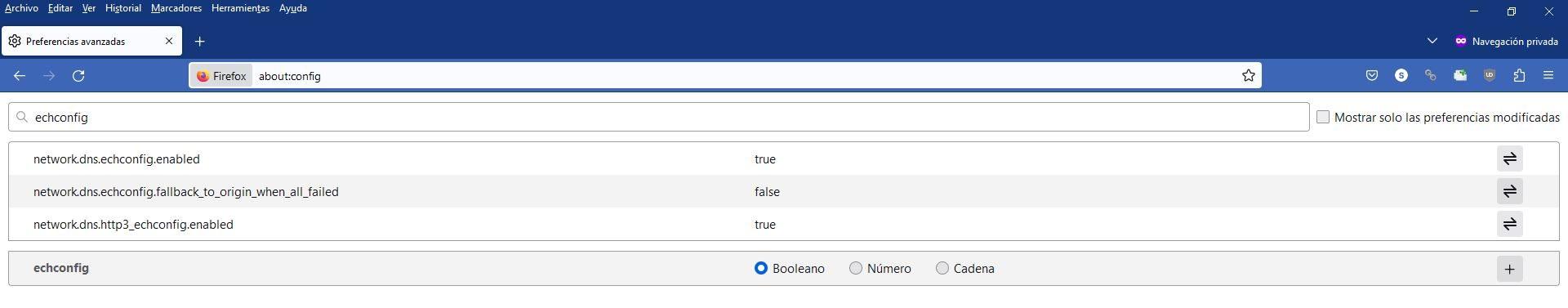
If we enter the advanced Firefox configuration menu, putting in the address bar «about:config» and we look for the string «echconfig» we can see that it is all set to «true», which means it is enabled. In addition, we have the fallback disabled for maximum security.
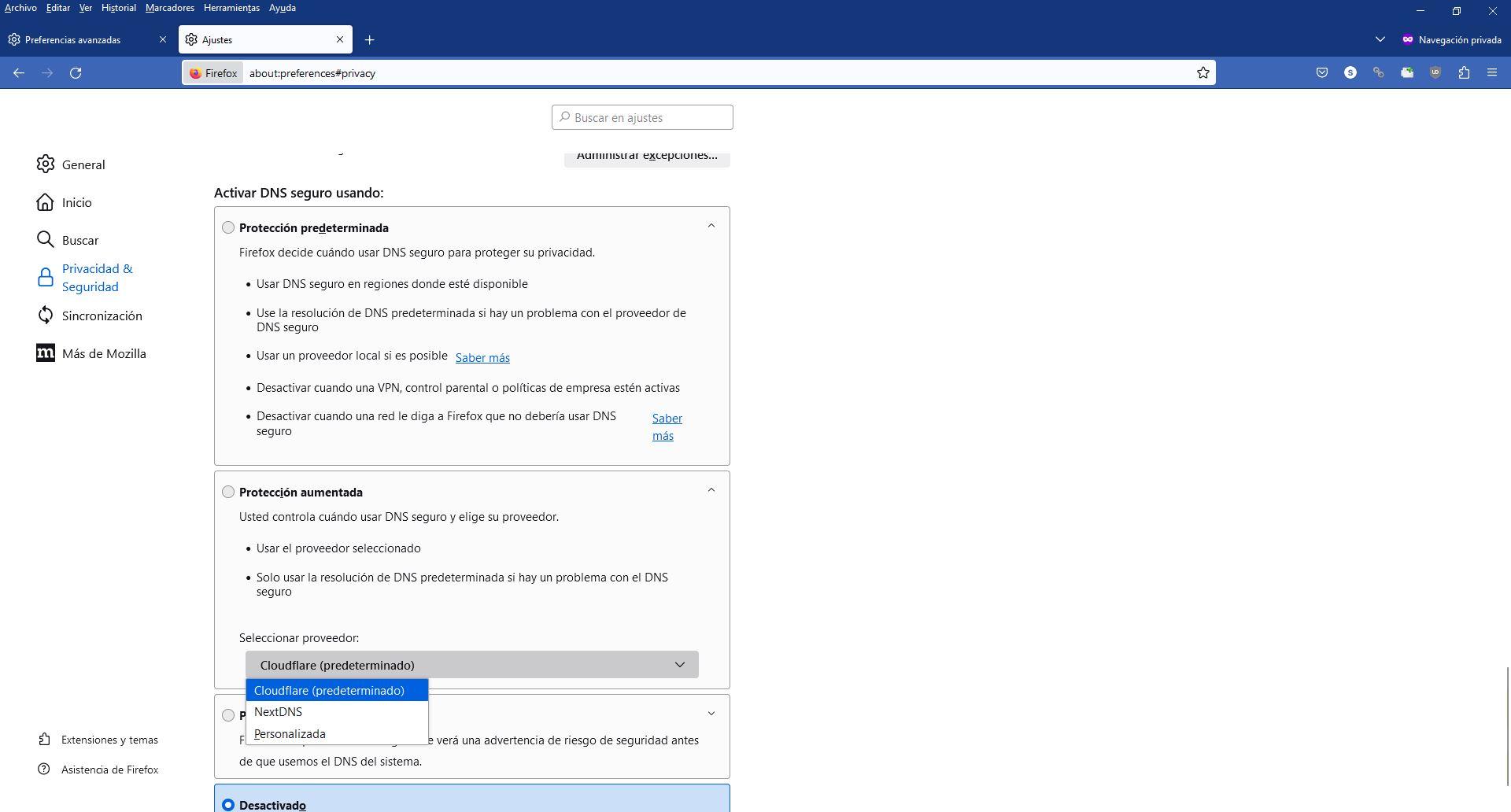
To enable the DNS over HTTPS If you do not already have it enabled, you must go to the «Tools / Settings» and in the « menuPrivacy & Security» you can see it at the bottom. In this menu you must activate the default, increased or maximum protection, to be able to use DoH and for ECH to be available.
Once we have activated DNS over HTTPS, when we enter a website that supports this functionality we will use it. However, today ECH is still somewhat “green”, so you could have connectivity problems.
Activate it in the Chrome browser
If you use the Google Chrome browser and want to use this TLS extension to protect your privacy, you can use it starting with version 117 of the browser. The normal thing is that you always have the browser updated to the latest version, so you should not have problems, but check the version from the three vertical dots menu, «Google Chrome Help / Information» and you will get something like this:
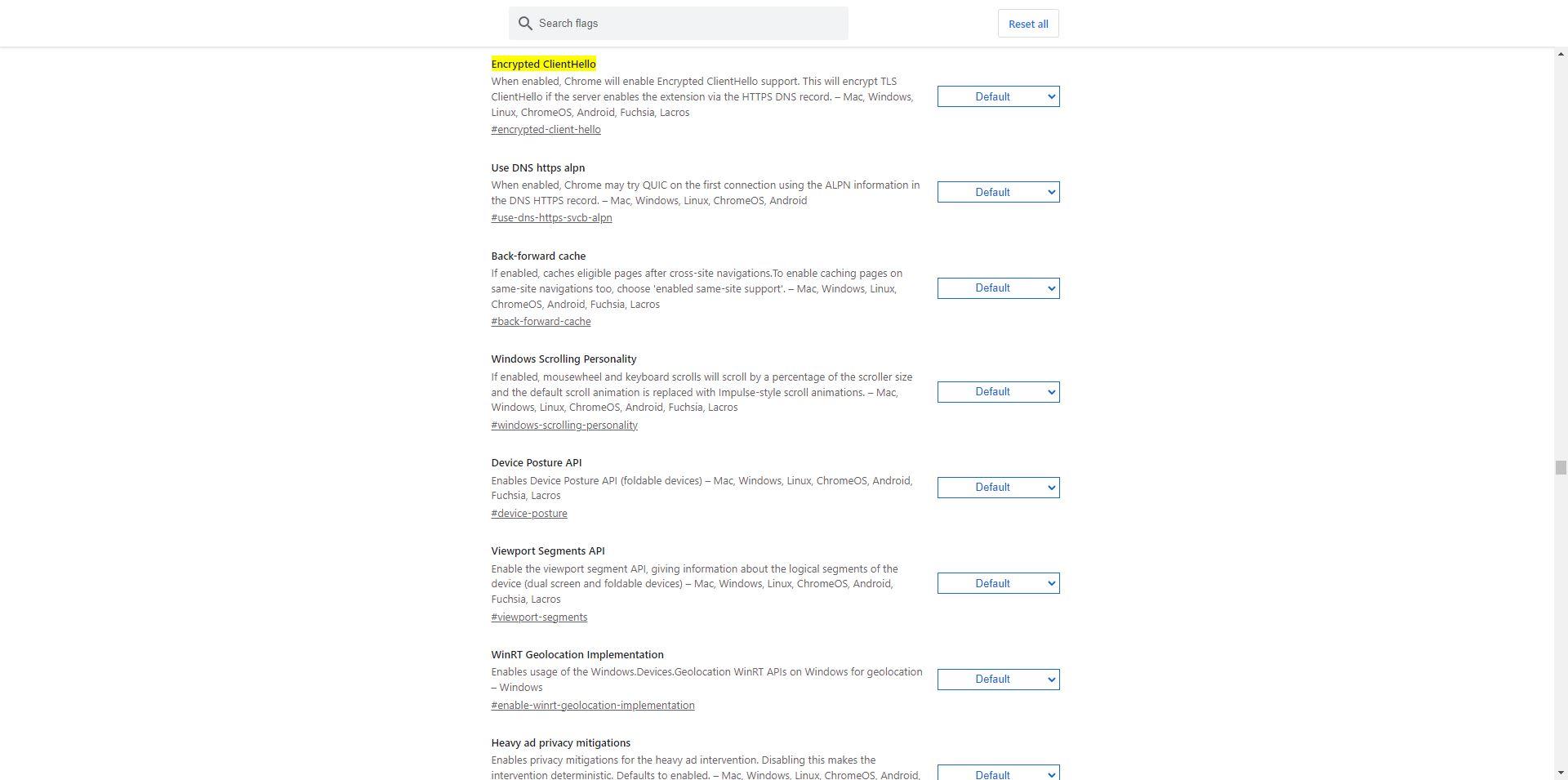
Once we have made sure of the version, in the address bar we put the following to take us directly to the configuration: “chrome://flags/#encrypted-client-hello” and we will see the following menu:
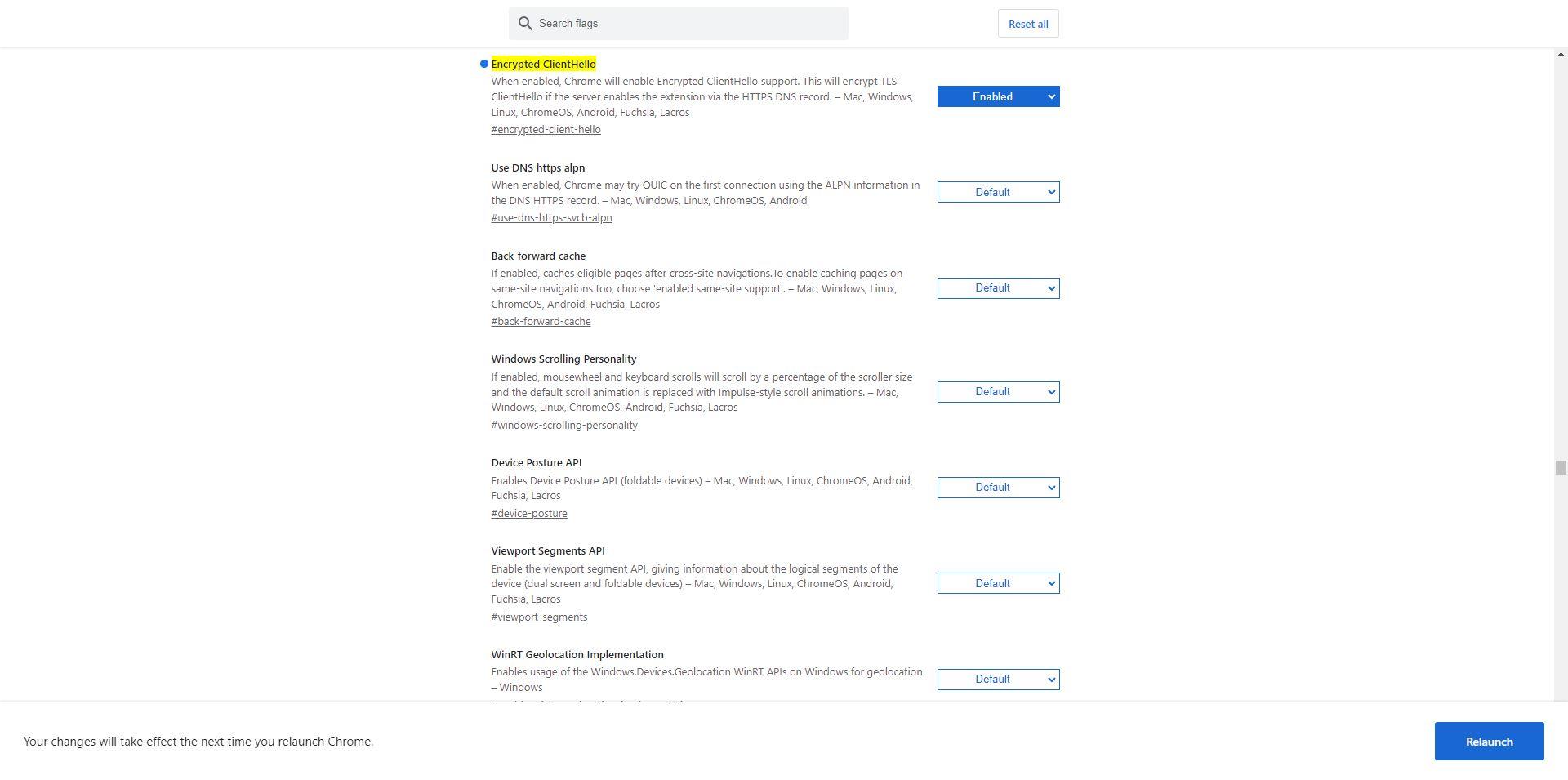
In the first option we will have to go from «Default» to «Enable«, and click on the « buttonRelaunch» to apply the changes correctly. The configuration would be as follows:
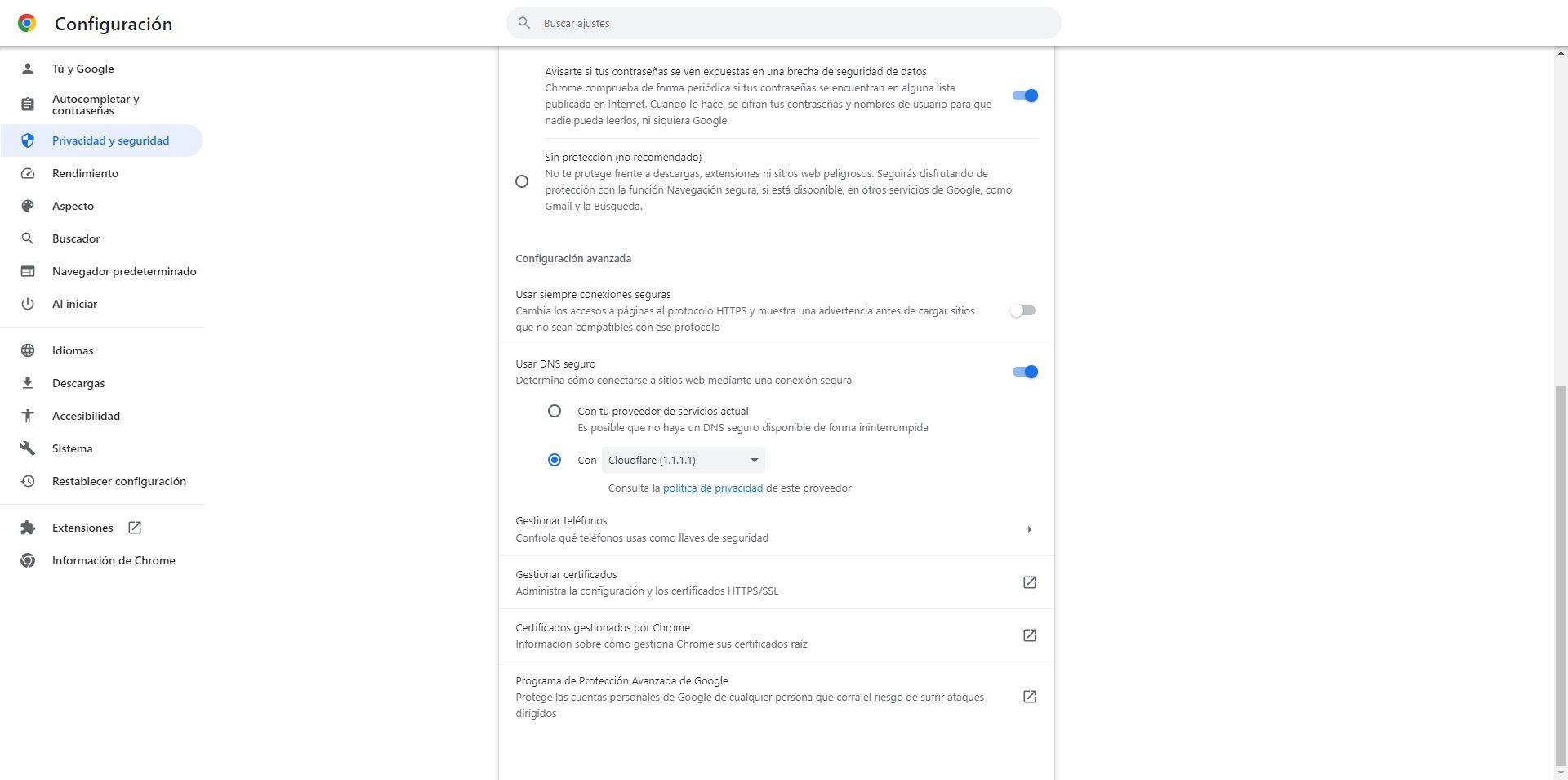
In this case it is also mandatory that we have DNS over HTTPS enabled and working. We go to the section «Settings / Privacy and security» or directly enter the following URL from the browser: «chrome://settings/security«. Once inside, you must enable secure DNS and select Cloudflare or any other provider built into the browser:
Once we have done this, we will have both DoH and ECH working for web browsing, although logically it will only work on web servers that support it.
Check if you have ECH activated
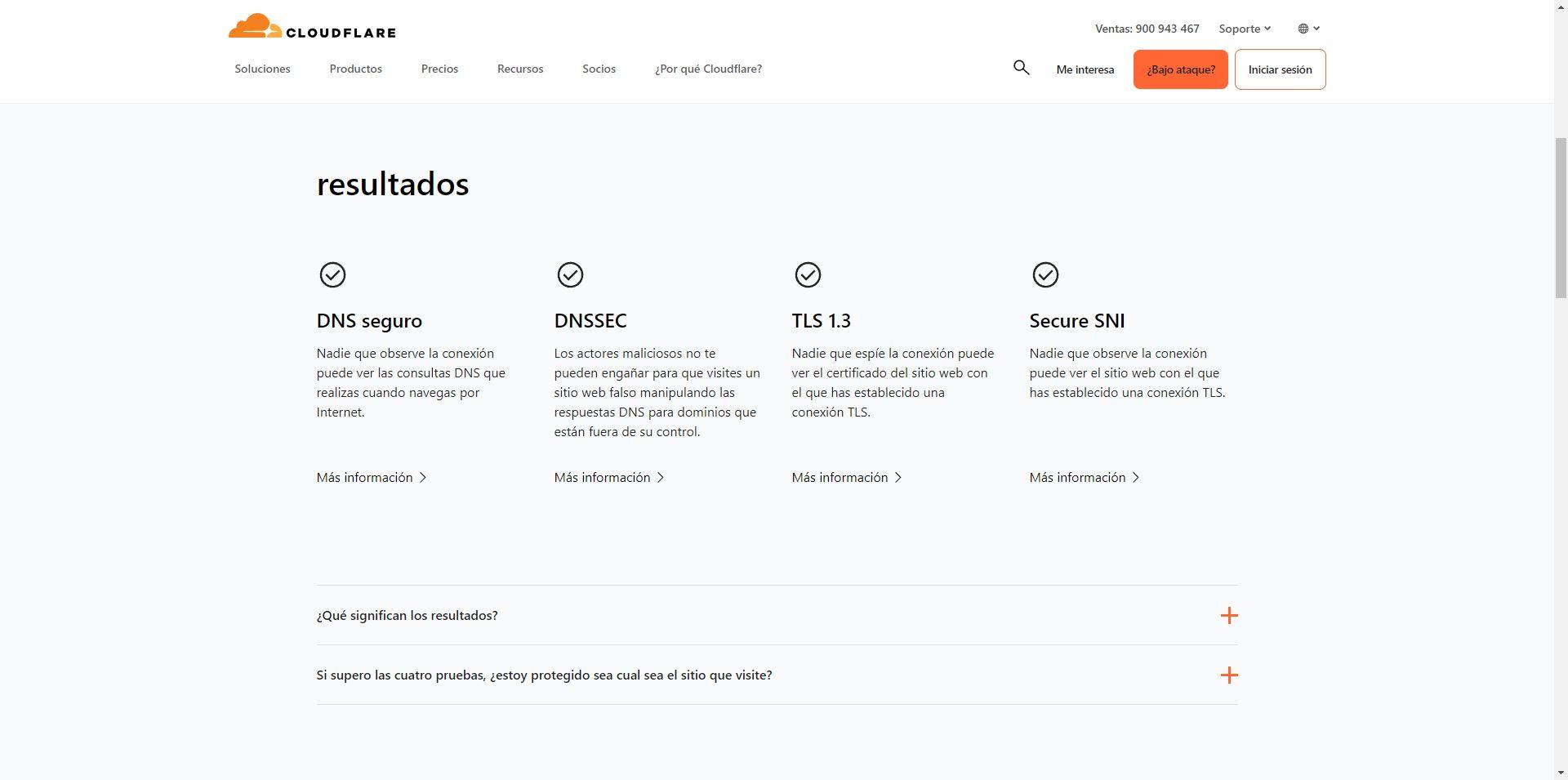
Once we have activated ECH in web browsers, it is essential to check that it is indeed enabled to avoid privacy problems. Currently there are different online tools to check it, our favorite is the one offered by Cloudflare for free. You can directly access this link and do the test, it takes a couple of seconds to check if we have it enabled and working:
Something like this should appear, indicating that we have secure DNS, DNSSEC, TLS 1.3 and also “Secure SNI” which is ECH:
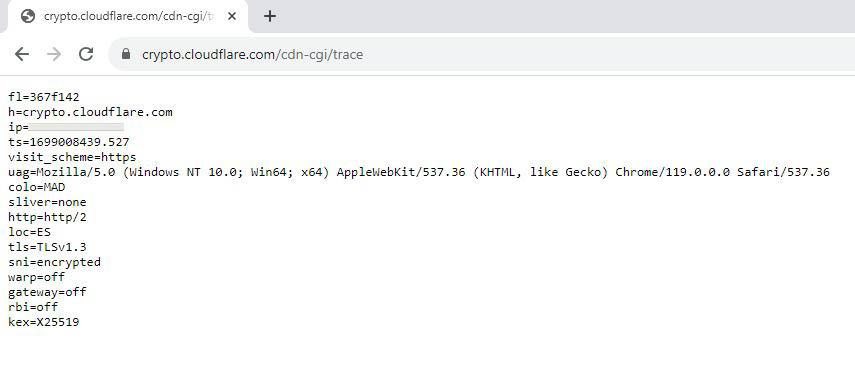
Cloudflare also allows us to access an online tool in text mode, this is perfect for checking it without having to go to a specific web page, and even for automating scripts.
We should get something like this:
In the “SNI” section it says “Encrypted” so we are using this TLS 1.3 extension without problems.
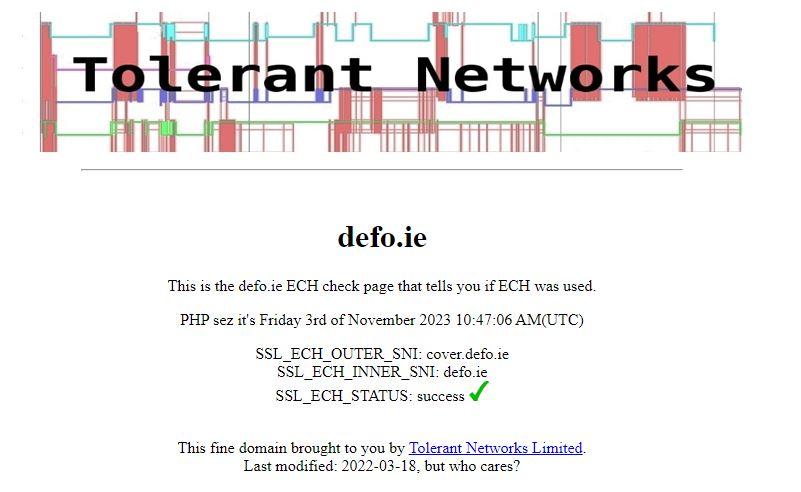
Finally, another website that we can use is the following:
In this case, we should get something like this:
The last option of “SSL_ECH_STATUS” should appear as “Sucess”.
As you can see, it is very easy to enable this important functionality to protect our privacy, and it is very easy to check that it works correctly. A very important aspect is that there could be a case in which a website does not load correctly due to having this function enabled. In fact, Cloudflare has decided to disable it on all websites by default because they detected many navigation problems.
Conclusions
In recent years, much progress has been made in security and privacy while browsing the Internet, for example, we currently have the TLS 1.3 protocol that not only provides us with great security, but also very good speed in the connections that are established. This TLS 1.3 protocol Compared to TLS 1.2 it is much faster, perfect for smoother web browsing. Navigation speed has also been improved thanks to the QUIC protocol, a protocol that is currently supported by thousands of websites, and will allow us to have great security and is really fast. Of course, DNS over HTTPS and DNS over TLS They also guarantee that DNS requests and responses are completely encrypted, something essential because otherwise our connections would not be fully encrypted.
The last “ingredient” incorporated into all the connections has been E.C.H., a TLS extension that will allow us not to send in plain text the SNI of the domain we want to visit. This was the last way that operators or cybercriminals had to know which websites we are visiting, now it will be even more difficult for them to do so. However, there is still a long way to go before we see how all web servers support it, since unexpected problems may appear when using it since it is a relatively new technology.