Today I am going to expose a little about Secure Bootthe security feature that accompanies UEFI and that was and continues to be heavily criticized from non-Microsoft circles, and that is that, although on paper it is supposed to be a standard, the way in which it was promoted by the giant of Redmond was seen by many as a way to try to push alternative operating systems out of the market, starting with Linux and FreeBSD, which are Windows’ main rivals on the compatibility spectrum.
When it comes to Secure Boot, we find ourselves with two worlds that coexist with the feature in very different ways. On the one hand we have Windows users, who have never had to worry about compatibility because Microsoft de facto has all hardware manufacturers at their service.
On the other hand, there are alternative operating systems, starting with Linux. Here the position around Secure Boot has been diluted and diversified, to the extent that the feature currently has up defenders. Simplifying, it can be said that there are currently three camps: those who reject Secure Boot outright, those who are not opposed to the concept but to the way it is managed, and those who have fully embraced it.
The use of Secure Boot in Linux has not been free of controversy and harsh anger, since in Ubuntu it was discovered that its implementation was not secure due to the fact that it skipped the boot feature, while within the development of the Linux kernel itself , the inclusion of the Lockdown module was up in the air for seven years because those responsible did not agree on whether or not to bind Secure Boot. In case anyone is wondering, Linus Torvalds was against it, while Matthew Garrett, creator of Lockdown, was for it.
In recent times it has been possible to see how systemd, which is basically the framework that establishes the way most of the main Linux distributions work, is advancing in the adoption of security mechanisms implemented at the motherboard level, among them the TPM required by Windows 11. Will we see Linux requiring TPM to work in the future? For now, the community has plenty of strength to prevent that from happening.
As we see, the sauce around Secure Boot is outside of Windows, and it is that there is not much to tell when the Microsoft system acts here as a good soccer referee. If he does his job well, he doesn’t give anything to talk about (or write).
What is Secure Boot
Secure Boot is a security standard developed by members of the PC industry. for the purpose of ensuring that software running on a computer is trustworthy to the manufacturer.
When the computer is turned on, the motherboard firmware checks the signature of every piece of software running on the computer, including UEFI firmware drivers, EFI applications, and the operating system. If the signature check is successful, the computer will finish the boot process and the firmware will give control to the operating system.
It is important to note that Secure Boot does not encrypt data storage and is independent of TPMalthough it is capable of working together with the module required by Windows 11. Basically, all Secure Boot does is make sure that the software has the required signature to be authorized to run on the computer.
Windows 8 and the UEFI push
Microsoft sowed discord with Windows 8, the failed converged operating system. Its best-remembered feature is Modern UI, known as Metro in its development phases, which is a tile-like interface for the Start menu that almost no one liked. That rejection, which limited the diffusion of the system, caused Steve Sinofsky to end up out of Microsoft.
Another controversial aspect of Windows 8 was the app store, which was accused of being an attempt to monopolize the distribution of software through a channel totally controlled by Microsoft. That caused many to raise their voices, including Valve and Epic Games. Who would have thought that, years later, the two video game companies would become bitter rivals after the second launched its own store in 2018.
But what really matters in this entry was that Microsoft required OEMs to use UEFI and activate Secure Boot if they wanted to get certified for Windows 8. That movement by Microsoft caught almost everyone responsible for Linux distributions off guard, who not only did not have support for a Secure Boot that can be disabled in the vast majority of cases, but were also unable to boot on UEFI due to that GRUB, the most widely used bootloader on that system, did not support that firmware interface.
Microsoft’s UEFI and Secure Boot requirement was the big push for both technologies and cost the Redmond giant a lawsuit that failed, as x86 machines where Secure Boot cannot be disabled are not common.
The passage of time and the availability of a third-party Secure Boot key for Linux has greatly changed the landscape around the open source operating system. for years there are distributions like Ubuntu and Fedora that offer good support for Secure Bootbut the security feature still has to be disabled in case of using an NVIDIA graphics card with its official driver.
However, despite the improvement in Linux support, there are quite a few users of this system who currently continue to think that UEFI and Secure Boot are two technologies that are hijacked by Microsoft and that only respond to its interests. Consequently, the first thing they do to use the operating system of their choice without barriers is to disable Secure Boot.
Even though the ways you’ve come UEFI are questionable, not everything contributed by the firmware interface has been bad, since, among other things, It has served to standardize the GPT partition table against the old MBR, it has allowed to improve the integration between the operating system and the motherboards (or their firmware). and in Linux it has opened the door to fwupda daemon that allows updating the firmware used by the hardware, from computers to peripherals, but despite the fact that the support it offers is improving, few manufacturers offer support through it.
Nuances between UEFI and Secure Boot
The campaign against Secure Boot also turned against UEFI. This has made many people believe that both are the same, but the reality is that the first acts as a feature of the second and can also be disabled, while the second must be supported by the operating system in a forced way if not. some kind of legacy support is available.
Summarizing a lot, UEFI (Unified Extensible Firmware Interface) is a set of specifications written by the UEFI Forum that defines the firmware architecture of the platform used to boot and its interface to interact with the operating system.. It was created with the aim of replacing the old BIOSes, while maintaining compatibility at least temporarily. The original EFI (Extensible Firmware Interface) specification, which is basically the old name, was developed by Intel.
I have already defined what Secure Boot is in previous sections, so I will limit myself to saying that it is a mechanism that is responsible for verifying the authenticity and legitimacy of the software that is going to be executed on the computer, using a verification mechanism to do so. through digital signatures.
How Secure Boot works
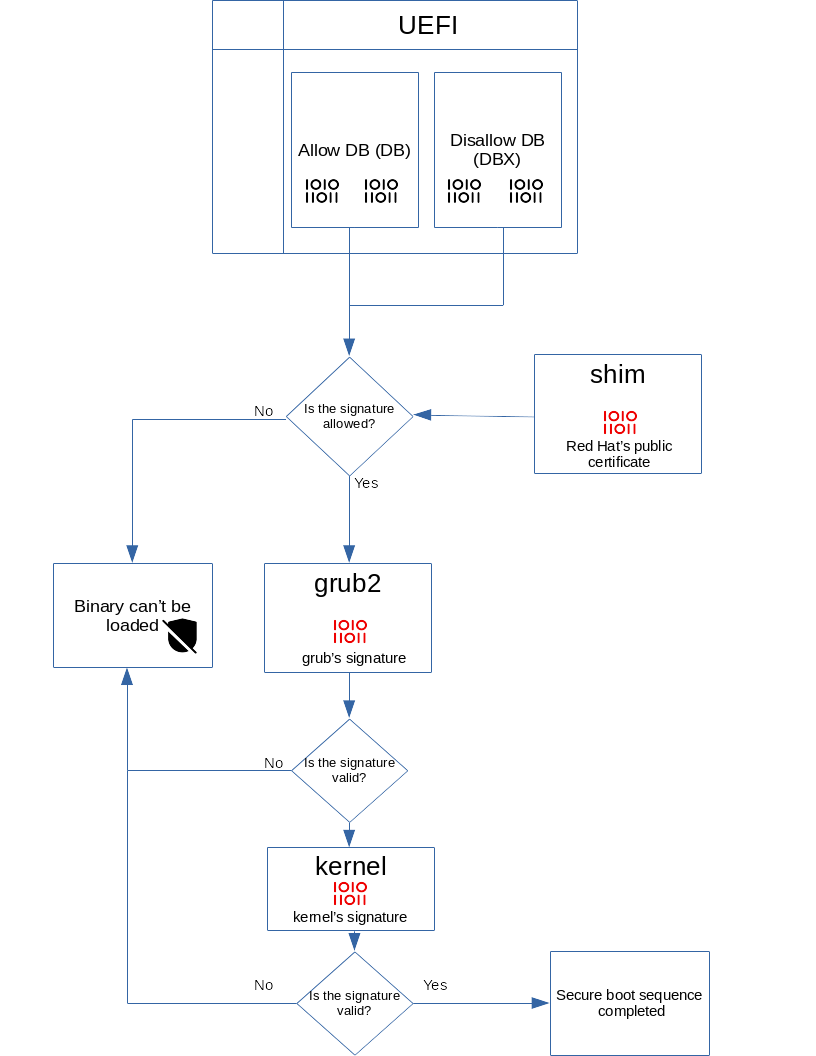
How Secure Boot works is easier to explain with a diagram than with words. One of the most important parts of the security feature is the Allow DB (DB) and Disallow DB (DBX) databases.which can be translated as database to allow and database to disallow.
DB stores the values hash and keys for trusted loaders and EFI applications that the machine’s firmware allows to load. For its part, DBX stores the keys and hash revoked, compromised and untrusted. In case you want to load a code signed with one of the keys present in DBX or that the hash matches a DBX entry, the platform will take care of causing the boot process to stop.
The following diagram shows the process that Red Hat Enterprise Linux goes through to comply with the various steps and requirements of Secure Boot. This scheme should be similar in any other distribution, especially those that use systemd.
First, it checks if the public certificate is present in Allow DBsomething that in case of being answered in the affirmative allows to go to the next bootloader check: GRUB 2. If the bootloader signature is valid, it will happen to do the same with the kernel (Linux), which in the event of another affirmative result, results in the fulfillment of the Secure Boot sequence and in the boot of the system. The logic with Windows is essentially the same, but this diagram from Red Hat shows an example using individual components rather than a generic overview.
Obviously, none of this testing process is done in case the user has disabled Secure Boot from their motherboard settings, and that is the best option if one wants to test Linux distributions or other operating systems over UEFI without more limitations than the need to support such a firmware interface.
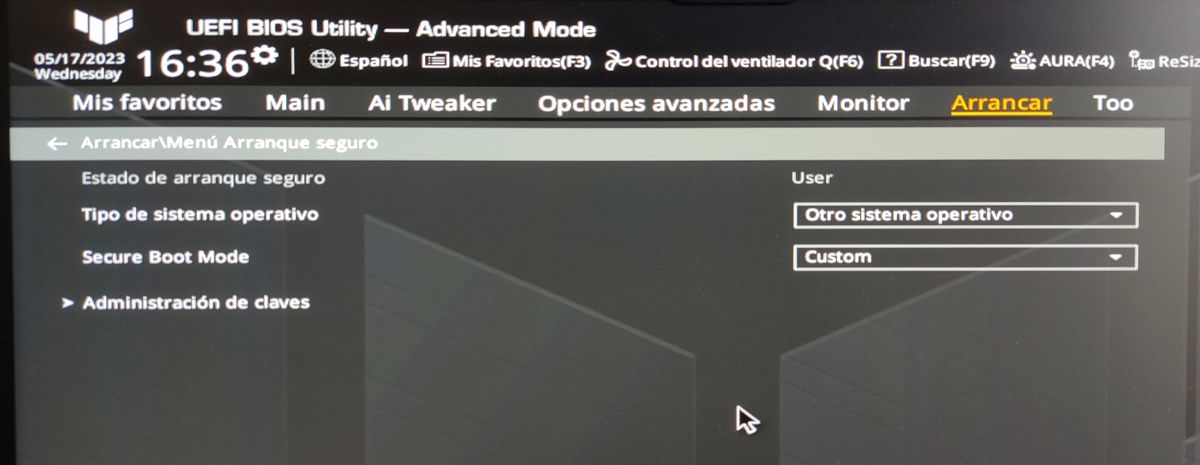
How to view Secure Boot settings on your motherboard
The Secure Boot configuration can generally be found in the Security/Safety or Boot/Boots. Depending on the motherboard, the user can find more generic configurations or others more oriented to Windows, which is, after all, the operating system for which more than 90% of the computers in the world are manufactured.
Desktops allow the disabling of Secure Boot relatively easily and without putting more obstacles for users, but when it comes to laptops, or at least that’s what happened to me with my current Acer laptop, disabling the feature Security requires setting a password to access the BIOS.
Conclusion
As we can see, Secure Boot is a feature that on paper provides positive things for users, but when it comes down to it, it has shown to have some holes that at least partially justify the arguments of its detractors.
Like it or not, Secure Boot is here to stay, and this is being seen in things like its expansion in the IoT, a sector that is totally dominated by Linux in general and Ubuntu in particular. However, that its use is voluntary and that it can be deactivated is still very important because not all distributions support the feature correctly, something to which we must add more underground profile systems such as those derived from Illumos.
Cover image: Pexels and Pixabay