If you take care to install a physical door with a good lock to close the access to strangers in your home, why don’t you do the same to secure your digital life… The main person in charge of this management is the router, perhaps the least known device in our computing infrastructure despite its enormous importance and to which it is too widespread not to pay too much attention. Until trouble comes…
In disclaiming consumers it must be said that in a typical use case the same Internet service provider is the one that installs and manages the router. The operator does not usually offer information on its characteristics, much less functions that should be known by customers. In other cases it even blocks those functions. In others, send the router by mail activating it remotely, so you can’t even talk to a technician, having to search for the information on your own.
And to close the circle, say that the routers of the operators are usually cheap OEM models that often do not have the necessary capacity. With these premises, it is almost logical that an ordinary consumer forget about a device with little visibility. Until we have access to the Internet, we lose performance, we cannot connect to Wi-Fi or, worse, a good “bug” sneaks into us as malware for not having properly secured the device.
Router management, basic and advanced
The local network is an essential component of any IT infrastructure and the router is its main device, serving the Internet, connecting devices and also serving as a “lock” to strangers trying to access our digital home. In addition, the increase in connected devices and the functions they have to support, including access to the Web and the multitude of Internet services (online multiplayer gaming, multimedia streaming, downloads…), has been a constant in recent times.
Either in the operator’s router or if you have bought an improved one (highly recommended) should invest a few minutes in a management that can save us many headaches in the future, improving the security and performance of your home network. We go with them.
Change the default login
The easiest access to the router is through a web interface using your access IP address (192.168.0.1, 192.168.1.1 or similar). Almost all routers of the same make or model have a certain username/password programmed in for easy access to the router. This type of access is public knowledge, it is usually as simple as the well-known “admin/admin” and must be provided by the operator/manufacturer.
If you don’t know it, a search on the Web is enough to know them and there are even specialized tools such as RouterPasswords that provide the data of any known make and model. It is therefore necessary change at least the access password as soon as possible to prevent unauthorized access to the router and thus control our entire network. The well-known moral applies here: “change the admin password before someone changes it for you”.
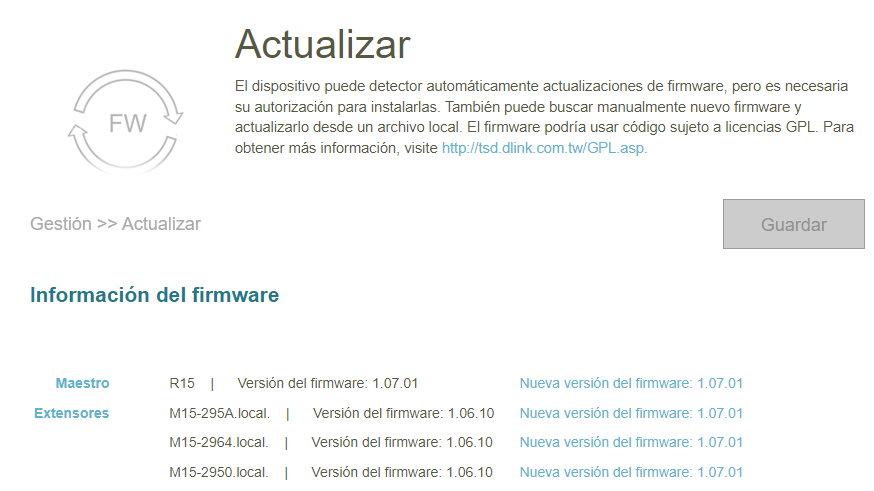
Update the firmware
Like any other electronic device, the router has a set of operating instructions and tools stored on a memory chip inside the device. Firmware updates on a wireless router are usually quite stable and therefore infrequent, but it is convenient to update them when the provider releases new versions. In addition, there are specific exploits and vulnerabilities that attack router firmware with the dire consequences that we have seen in many attacks.
The most advanced models have an automatic update function that can be scheduled at specific times so that the user does not lose activity. It’s a good way to keep you up to date.
Change Wi-Fi password
Like the router access password, it is It is essential to change the password that comes by default for access to the Wi-Fi wireless network. Although the situation has improved, there are still many operators that use less secure protocols and passwords that can be easily learned. Or that they are placed on a sticker on the same router, perhaps within the reach of third parties that you want them to not know about.
All current routers (or Wi-Fi access points) support strong encryption such as WPA3 and it is the protocol that we should use whenever it is available. As for the password, you know, it’s useless to use a strong protocol if we put the name of our dog, known by all our neighbors. It should be the longer the better, combining uppercase, lowercase, symbols and numbers or generate random keys with password managers.
Change the SSID or hide it
the SSID (Service Set IDentifier) it is a name included in all the packets of a wireless network. With a maximum of 32 alphanumeric characters, it refers to the name of our wireless network or of others that are within reach of a device or computer. The name included by default, generally gives away the model and manufacturer, something that is not convenient to reveal. In addition to changing its name, the configuration of the routers allows the option of hide this SSID to prevent it from being shown as a wireless network. There are special programs that can track them even when they are hidden, but it is a recommended option.
Disable remote access to the router
99 percent of home users do not need this function that allows access to the router from any point with Internet access. Since the router not only functions as the brain of home network management, but also as a security server, remote access can be another open door for third parties to gain full access to the home network. Make sure this feature is disabled.
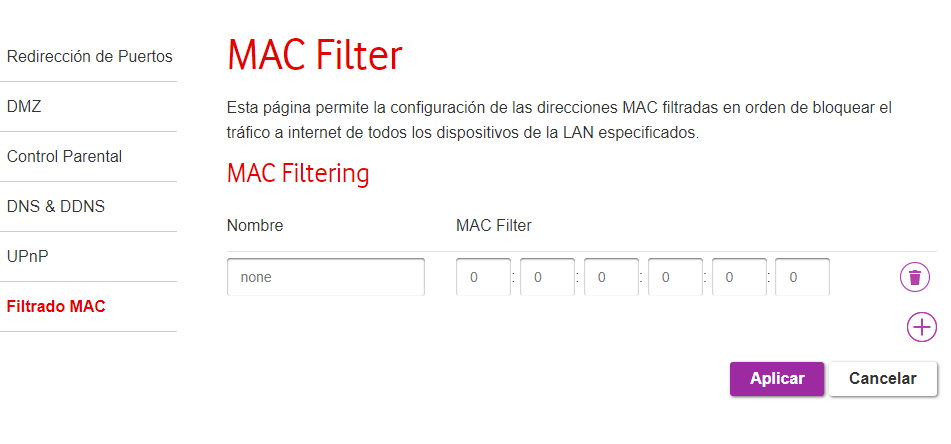
Manage MAC addresses
Each device that can connect to a network is assigned its own unique identifier in the form of a number called a MAC address. It is hardcoded in the production of each device and cannot be changed. This allows us to control exactly which devices can (or cannot) access our network.
Most of these wireless routers offer this MAC address filtering feature. You can block specific devices or for added security create a list of only those devices that can connect. The MAC address of each computer is easily known with the “ipconfig” command in Windows, Mac or Linux. On Android or iOS devices you can see it in the advanced Wi-Fi settings.
Take advantage of the less saturated bands
If you are lucky enough to have a wireless router that supports Wi-Fi 6E, you can take advantage of the expansion of the band at 6 GHz which has brought the latest wireless standard. The same with the 5 GHz band, both less saturated, with less interference, more stable and potentially faster than the 2.4 GHz band. Most new routers allow the simultaneous use of both bands or the creation of different wireless networks for each of them. You will need devices that support it to get its maximum performance. Of course, remember that the 2.4 GHz band has a greater range than the others.
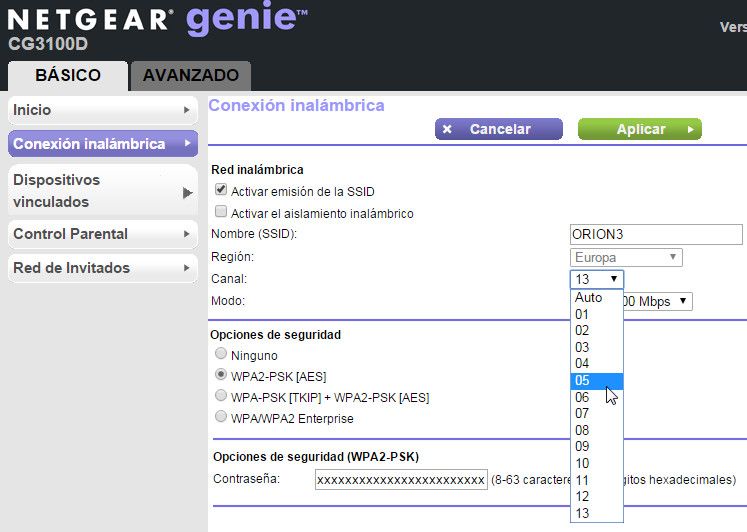
Change access channels
A wireless router transmits data on one of several available “channels” (13). If, as is usual in a neighborhood community, there are a lot of routers in the surrounding area using the same channels, it is likely that interfere and be one of the causes of loss of performance. The most advanced routers try to avoid this by automatically selecting the best channel, but the ideal is to do it manually and check the operation of each one of them. There are external applications that can help you. Watch this tutorial if you need it.
Prioritize traffic with Quality of Service
QoS (Quality of Service) is the average throughput of a telephone or computer network from network users. Measure parameters such as error rates, bandwidth, performance or transmission delays. When bandwidth is maxed out by multiple applications and devices, services like online gaming, streaming, or video conferencing can experience massively degraded performance.
This is where this “quality of service” comes in with which we can prioritize the services we need at the expense of less important ones. Some routers also offer support for Wi-Fi Multimedia (WMM) connections, a specialized type of QoS that automatically prioritizes voice, audio, and video data in an attempt to improve multimedia performance.
Manage port forwarding
He Port Forwarding is the function of port forwarding and allows remote computers (for example, public machines on the Internet) to connect to a particular computer within a private LAN. Ports are used by a router to filter traffic into different types (http commonly uses port 80 or incoming email via SMTP uses port 25).
There are 65,536 ports in total and for security reasons most of them are blocked by default. If the software or services use non-standard port ranges the router may not be able to send data to a particular device. If you have this problem (for example in network connections on video game consoles or for access to Torrent networks) you will have to manage this port forwarding.
Use Guest Access
It is a fact that someone who visits your house will ask you for the Wi-Fi password to connect their own device. If you can’t say no but still want to be in control of your network, guest mode is ideal because it sets up a sort of subnet with its own SSID and password, with no access to your main network. Connected users have Internet access and nothing else, and you can restrict the number of people who can connect at any one time.
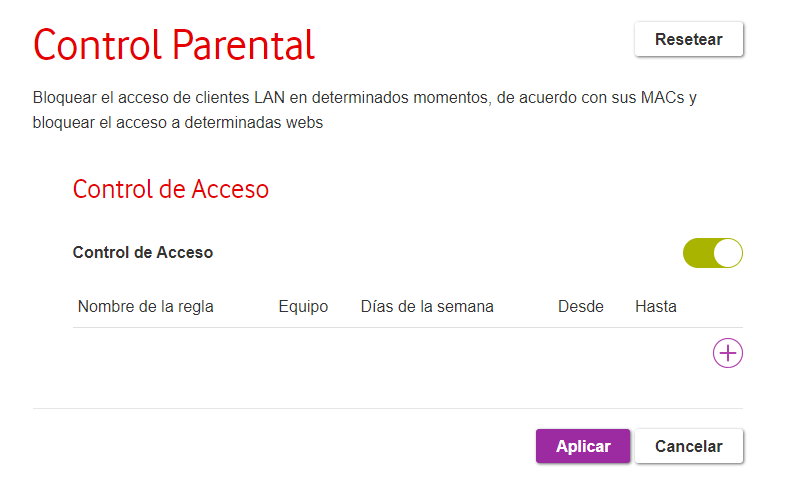
Use parental controls
In a similar vein to that of guest mode, many modern routers also offer parental control features, especially aimed at controlling the use of the youngest members of the household. The exact characteristics may vary in each router, but aspects such as Internet access hours can be limited in all of them. The ideal is to work with the MAC address of the device to be controlled, although there are other ways.
File sharing on the network
Many modern routers include an additional USB port. Most users do not use it but it can be used, for example by connecting an external storage unit to share files. Once connected and configured you can access your content from any device connected to the network. It can also be used to connect a printer. This function you will see as DLNA
Beware of mobile apps
All of the above features are configured through the router’s control panel, normally accessible from the web browser of a computer connected to the network. However, some of the consumer routers can be controlled via smartphone apps. You can try them but you have to have be careful with them for safety aspects. In fact, one of the general security recommendations is to disable remote access to the router as we saw above.