Hikvision cameras affected by a critical failure
This security flaw affects the firmware of Hikvision IP cameras, both the latest and older ones. They have detected that it affects the most recent version that was released on June 21, but also other models with versions of even the year 2016.
This vulnerability not only affects IP cameras, but is also present in some NVR models. However, in this case it is not such a widespread problem.
How can you exploit the vulnerability CVE-2021-36260 What affects IP cameras and some Hikvision NVR models? A hypothetical attacker could gain full control of the device simply with a root shell without administrator access. According to the researchers behind this discovery, they might even have more permissions than the device owners themselves, as they are restricted to a limited protected shell.
But this does not affect only the IP cameras themselves, it is able to access and attack internal networks. In addition, these cameras are often connected in sensitive places, so many critical infrastructures could be at risk. This critical vulnerability allows unauthenticated remote code to be executed for full control.
An attacker would only need access to the HTTPS server port, which is generally 80/443. No username would be required, and no password would be required. In addition, the owner of the camera would not have to do anything and the whole process will be undetectable. This paves the way for anyone who exploits this vulnerability.
Many affected models and patches available
The security researchers who discovered this serious security flaw have provided the complete list of affected Hikvision models. Many cameras and firmware versions that can be exploited by an attacker and have full access. It is always important to use good security cameras.
They were able to run a proof of concept to exploit the vulnerability and, for example, were able to obtain the password for the administrator account and have access to the content.
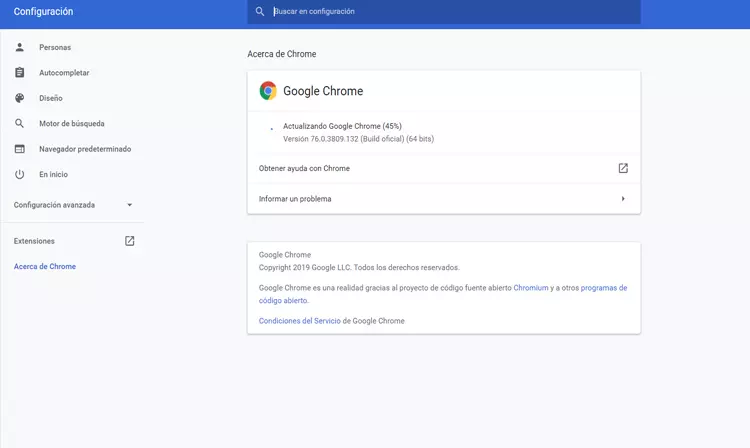
The good news is that there are patches available and, at least partially, the devices are protected. The IPC_G3 version (V5.5.800 build 210628) fixes this problem and users must install it to be protected.
Once again the importance of always having the latest versions available on any type of device or system is demonstrated. Especially when it comes to computers connected to the network, it is more important to correct any failures as soon as possible and prevent them from being exposed so that any attacker can exploit those vulnerabilities and have access that could compromise the security and privacy of the user, in addition to the operation itself. .