Last week, Windows was affected by a new security flaw: PrintNightmare. This bug, registered as CVE-2021-34527, allows an attacker to run remote code on any PC with SYSTEM permissions, a flaw for which several exploits are circulating over the Internet and for which, furthermore, there is currently no solution. Until next week Microsoft will not release its official patch to cover the vulnerability on their computers. However, if we don’t want to take unnecessary risks until then, there are several ways to mitigate this problem.
First of all we must indicate that this vulnerability It primarily affects Windows Server computers and other domain-joined versions of Windows. However, if changes have been made to the default settings of Windows 10 it can also compromise the system.
Official solutions for PrintNightmare
There are two official ways, recommended by Microsoft, to protect ourselves from this vulnerability.
Disable Print Spooler
This is the simplest method to protect ourselves from this failure, although we must be clear that, as long as we have it disabled, we will not be able to print anything from said equipment.
To do this, what we must do is open a PowerShell window, with administrator permissions, and execute the following commands in it in order:
- Run Get-Service -Name Spooler.
- Run Stop-Service -Name Spooler -Force
- Stop-Service -Name Spooler -Force
- Set-Service -Name Spooler -StartupType Disabled
The third command stops the service, and the fourth deactivates it. When Microsoft releases the final patch, what we must do is re-enable the Print Spooler to be able to print normally on the PC.
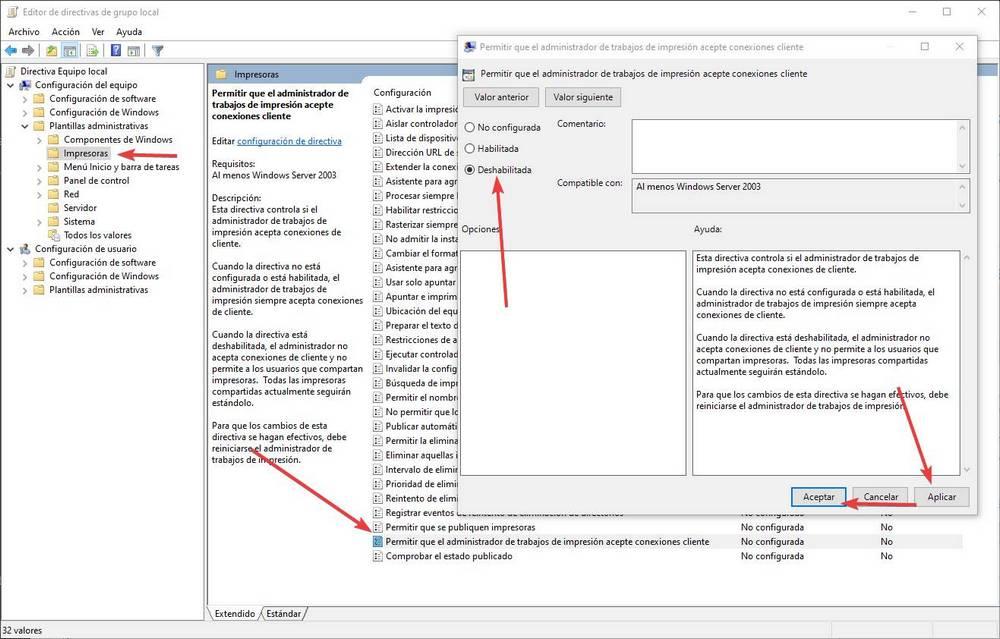
Disable remote printing
Another way to protect ourselves from this security problem is by disabling the remote printing functions. To do this, what we must do is open the group policies (executing the gpedit.msc command) and go to the Computer Configuration> Administrative Templates> Printers section. Here we will double click on the section «Allow Print Job Manager to Accept Client Connections»And we mark this directive as« Deactivated ».
We apply the changes, accept and that’s it. Now you can no longer remotely exploit this security issue.
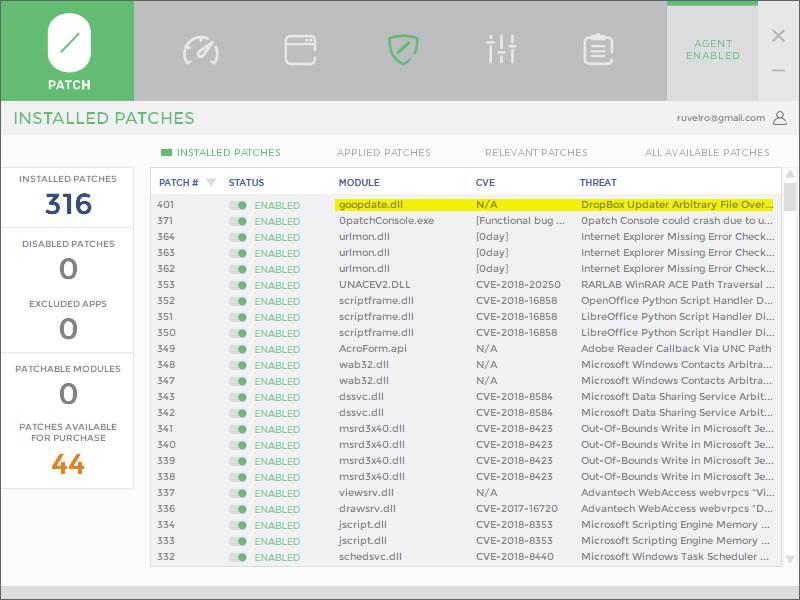
New patch 0Patch against PrintNightmare
0Patch is a tool that provides users with micro-patches with which to solve all kinds of bugs and vulnerabilities. Unlike the updates that Microsoft releases for its operating system, which basically detects and replaces vulnerable libraries, which does 0Patch is to apply hot-patching updates. What these types of patches do is locate the vulnerability in the RAM memory and patch it directly in it. In this way users are protected and the integrity of Windows is not altered.
This company has just released a series of free hot patches to protect users from these problems. These patches are available for all editions of Windows Server, from 2012 to the latest 2019, and will allow all users to protect themselves from them with a couple of clicks, without altering any system file. The patches will be free until Microsoft releases theirs.
These patches can also be used in Windows 10, although it can cause problems as they were not designed for it.