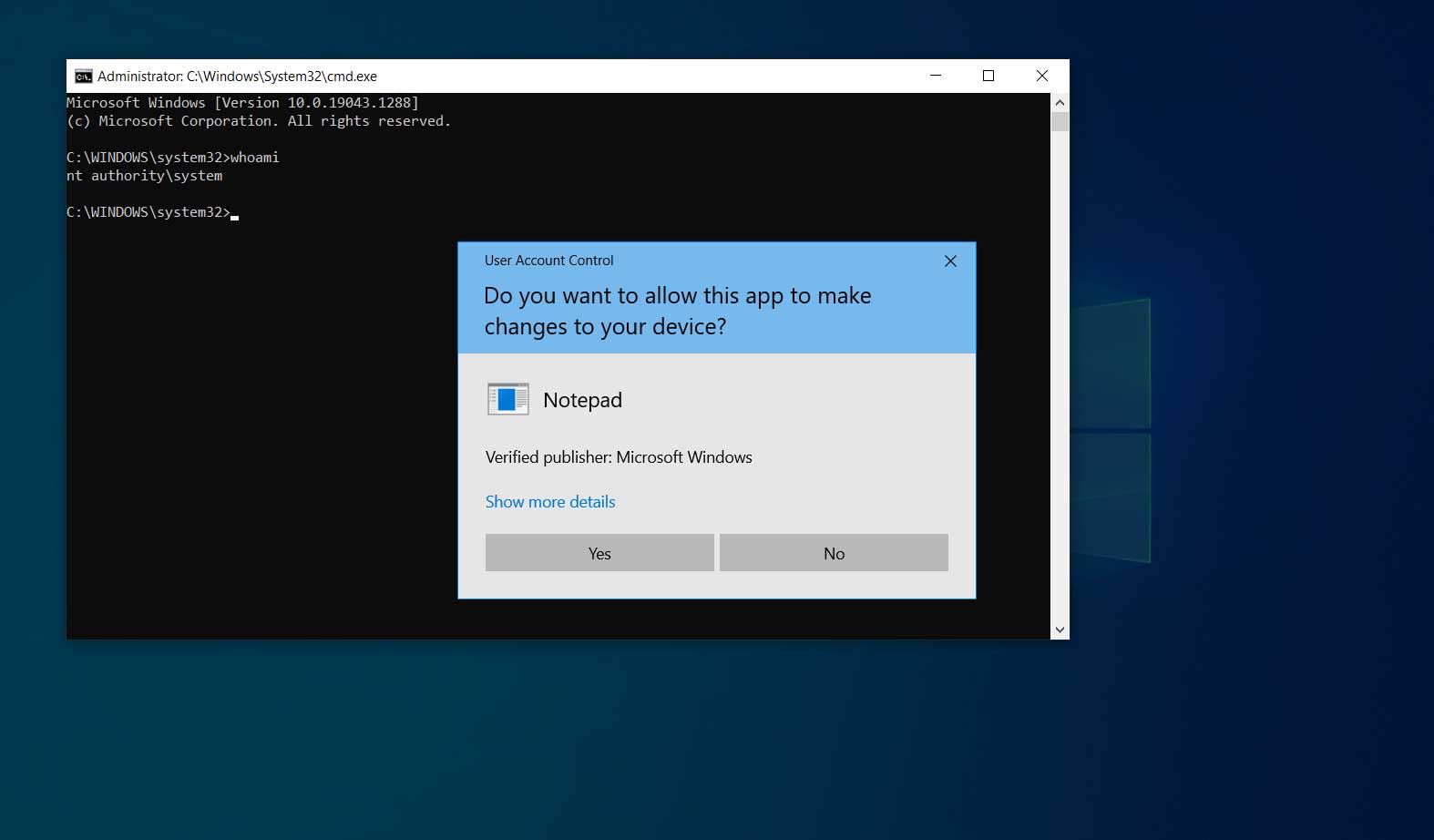
A zero-day bug, not completely fixed by Microsoft for several months, was recently given an unofficial patch and made freely available to users of the company’s operating system. The vulnerability tracked as CVE-2021-34484 (7.8 at CVSS v3 scale) allows users to gain administrative privileges (LPE or local privilege escalation) on Windows 10, Windows 11 and Windows Server.
According to the 0patch team, responsible for providing the unofficial fix for discontinued versions of Windows and fixes for some of the vulnerabilities not officially resolved, the flaw is still a zero-day.
Since the discovery in August of last year, Microsoft has not been able to resolve the flaw, despite having already marked the bug as doubly fixed. In addition to not having fixed the problem, they ended up making 0patch’s previous unofficial patch unusable.
Although exploits have been publicized in the past, it is believed that they have not yet been actively exploited in the wild.
“The company’s attempt was worse than the first”
CVE-2021-34484 was discovered by security researcher Abdelhamid Naceri and revealed to Microsoft, who at the time released a patch on the August Patch Tuesday, fixing part of the vulnerability.
— Abdelhamid Naceri (@KLINIX5) October 22, 2021
With the patch incomplete, Naceri released a proof of concept (PoC) capable of bypassing the official patch on all versions of Windows.
Image: BleepingComputer
Later, the 0patch team released an unofficial security update to all versions of the operating system and free for registered Windows users.
Microsoft’s response followed with a second update, released on the January 2022 Patch Tuesday, giving the deviation a new tracking ID (CVE-2022-21919) and marking it as ‘fixed’.
However, Naceri has again found a way around Microsoft’s newly released patch, which in theory — for her — fixed the flaw. According to him, the company’s attempt was worse than the first.
By putting the patch to test the researcher’s exploit, 0patch found that the fix for the “profext.dll” DLL still protected users from the new method of exploitation, allowing these systems to remain secure. However, this security lasted until Microsoft released the second patch, which replaced the “profext.dll” file.
In a new attempt to fix the vulnerability, 0patch has released a patch that did not conflict with the March 2022 Patch Tuesday updates.
The Windows versions that can take advantage of the fix are as listed below:
- Windows 10 v21H1 (32 & 64 bit) Updated with March 2022 Updates
- Windows 10 v20H2 (32 & 64 bit) Updated with March 2022 Updates
- Windows 10 v1909 (32 & 64 bit) Updated with March 2022 Updates
- Windows Server 2019 64 bit Updated with March 2022 Updates
It is worth noting that Windows 10 1803, Windows 10 1809 and Windows 10 2004 are still protected by the original 0patch patch as these versions have reached the end of support and have not received the Microsoft update that replaced the DLL.
How to install 0patch micropatch
Until Microsoft releases a full fix for the particular LPE issue and all of its deviations, the micropatch will remain available to users of the versions listed above.
For those who intend to install the 0patch fix, just have the latest update (March 2022) and create a free account at 0patch Central. From there, install and register on this 0patch Agent page.
The process does not require additional manual actions or necessary restarts for the update to take effect.
In a comment to BleepingComputer regarding plans to revisit the flaw in particular and a future fix via an update, a Microsoft spokesperson responded that they are aware of the report and that they must take necessary steps to protect customers.



