The fingerprint reader has become one of the central pillars that support the security of your smartphone, although some models have been betting on more advanced solutions for some time, such as the Apple iPhone which, as our regular readers already know, uses a 3D facial recognition system that cannot be fooled using photographs or videos.
There is no doubt that both security systems have its advantages and disadvantages when used on a smartphone, and that in the end there is no perfect solution, but the truth is that overcoming a fingerprint reader is much easier than it seems, and it is not necessary to use advanced or especially expensive technology.
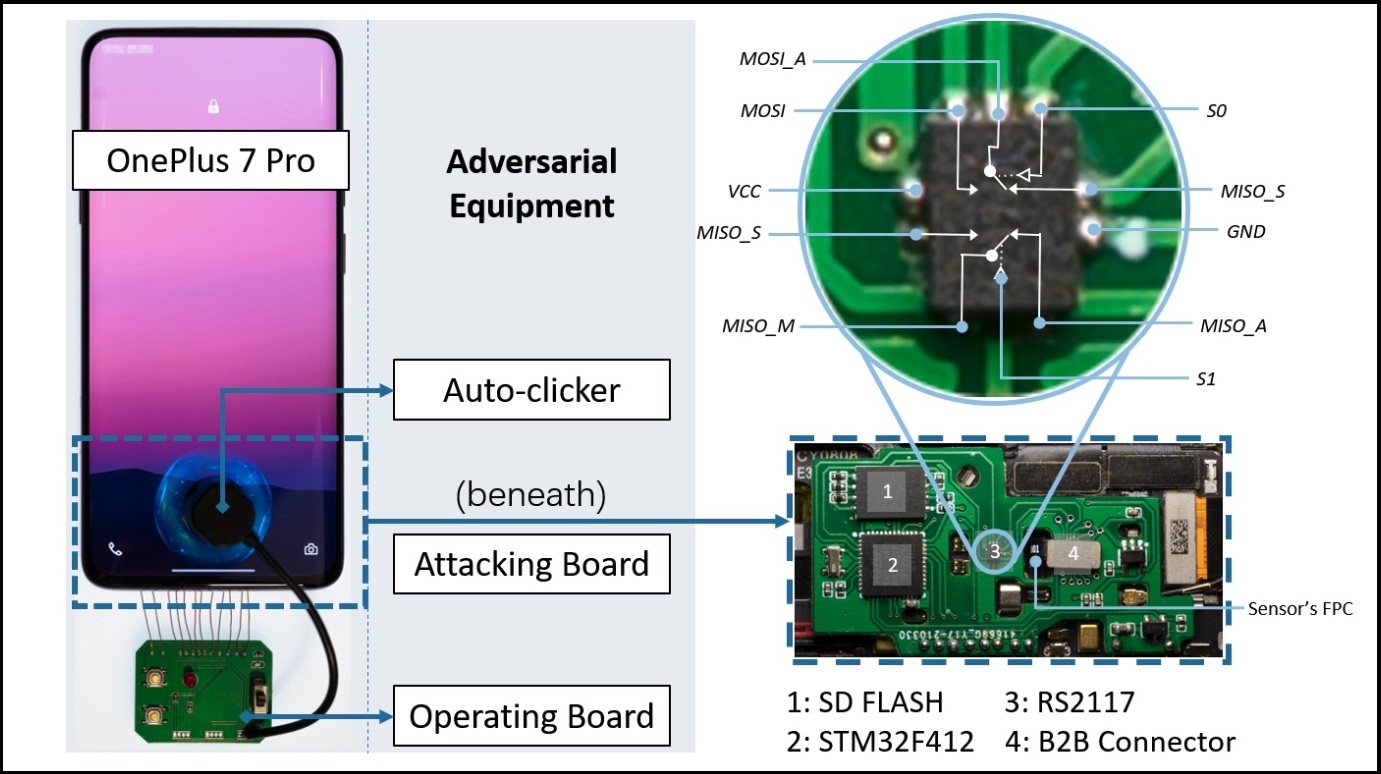
A group of experts has shown that it is possible to overcome the fingerprint reader of different terminals based on Android and iOS, among which are the Galaxy S10+, iPhone SE, OnePlus 7 Pro and Xiaomi Mi 11 Ultrausing a brute-force fingerprinting attack known as “Brute Print”.
In order to carry out this type of attack, it has resorted to a plate that costs only 15 dollarsand which integrates an STMicroelectronics STM32F412 microcontroller, a dual-channel bidirectional analog switch known as RS2117, an SD flash card with 8 GB of storage capacity containing a huge database of fingerprintsand a board-to-board connector that connects the phone’s motherboard to the fingerprint sensor’s flexible printed card.
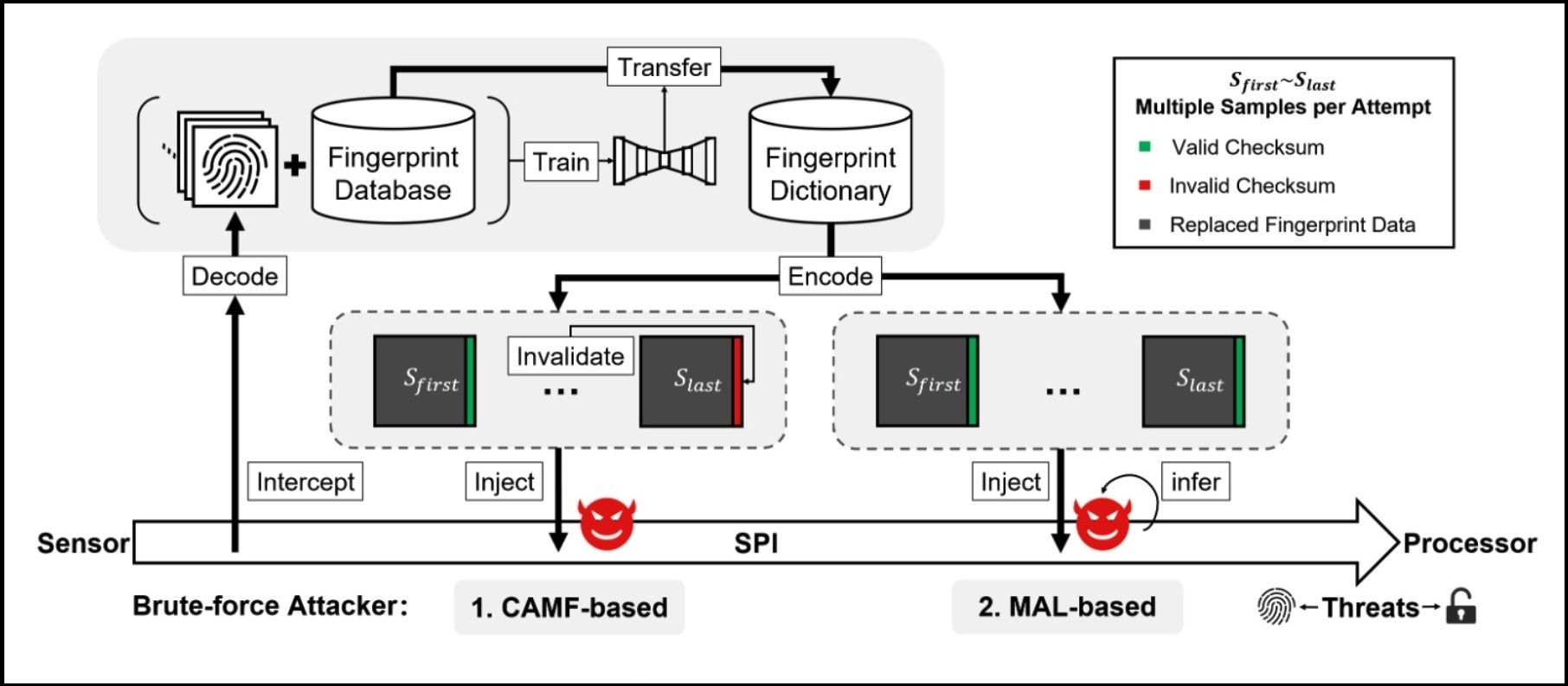
This type of attack takes advantage of vulnerabilities that allow unlimited fingerprint identification attempts, and from there it begins to use that database of fingerprints that the plate contains to send them to the smartphone until it is unlocked. I know what you are thinking, how can my fingerprint leak? You may be surprised by the answer, but the truth is that they don’t really need your fingerprint for this attack to work.
The crux of the matter is that the fingerprint authentication system has a reference margin or threshold that is relatively wide, which means that does not require an exact match at the fingerprint level, but it is enough that the image of this is considered as an acceptable approximation. In other words, if a fingerprint similar to ours is found in that database, the attack will be successful and the security of our smartphone will be compromised.
On the other hand, it should also be noted that with “BruteForce” a manipulation is performed so that the false accept rate is higher, which greatly facilitates the margin of success when using those images similar to our real fingerprint. Obviously, to be able to carry out this type of attack, it is not only necessary to have that plate, but also you have to connect it to the smartphone and turn its fingerprint database into a kind of “dictionary” usable, but this is not particularly complicated for people with minimal knowledge.