
A simple, but rather dangerous, security vulnerability has been discovered in macOS. It allows you to execute code remotely, with the help of a stupid, seemingly harmless shortcut file.
A new security flaw has been discovered within macOS. In a blog post dated September 21, 2021, the cybersecurity specialist SSD Disclosure details how a simple web shortcut file can be used to execute code remotely on a Mac.
The flaw is located at the heart of the system, since it is the Finder (the file explorer of macOS), itself, which is affected. It seems that all versions of macOS are affected, even the most recent version (macOS Big Sur 11.6). We were indeed able to reproduce it on a perfectly up-to-date computer.
Where does the security breach come from?
The flaw is not terribly complicated to exploit. A victim only needs to open a simple .inetloc file for a hacker to take control of their machine. .Inetloc files are normally shortcuts to a web server, or to a machine on the local network. But with a little bit of development knowledge, it is possible to place system commands within this small file. Commands that will be silently executed, without even the owner of the machine realizing it.
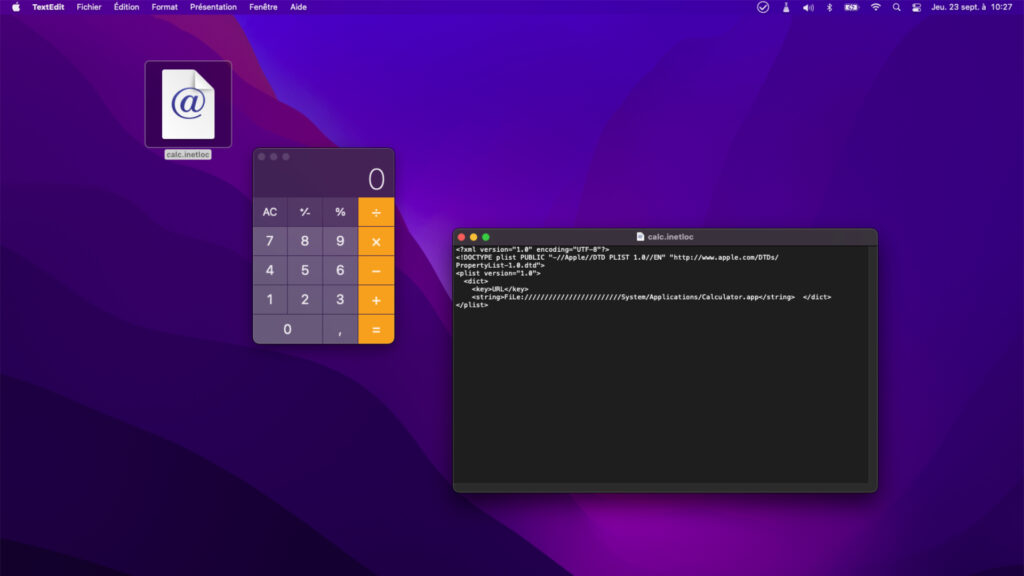
In the example provided by SSD Disclosure, it is possible to open the Calculator application by simply double-clicking on an .inetloc file. This script is perfectly benign, but proves that a command can be hidden in a seemingly harmless file. We were able, with two or three modifications, to launch a terminal emulator and execute commands. You just need to point to a local resource (present on the hard drive of the computer) with the prefix “File: //” to access the content of the computer.
Do not run an .inetloc file
Warned the first time by whoever discovered the flaw, Apple has deployed a security patch that unfortunately does not go far enough. The patch made available by Apple blocks remote code execution with the prefix “file: //”, but does not take into account typographical case. This means that variants like “FiLe: //” or “filE: //” always work.
According to SSD Disclosure, even opening such a file in an email attachment can infect your computer. Until this flaw is fixed (which we hope won’t take too long given the simplicity of the problem), the best thing to do is therefore to be very careful when downloading files of this type. More generally, do not open files from unknown sources, you will avoid trouble.



