Before reading the article, you may not have come across the term “calculate MD5” yet. Maybe you don’t know what MD5 is, what it is for and much less how to use it. In any of the possible cases, don’t worry. After reading this article you will come away knowing what it is, how it is calculated, and even how and where to use them in a useful and effective way.
In today’s article we will first see what MD5 is. Subsequently We will see how to encode it and finally we will see in which cases and in which places it is useful to use it. opt for extra security when plain text does not offer us more in this sense.
Index
What is MD5
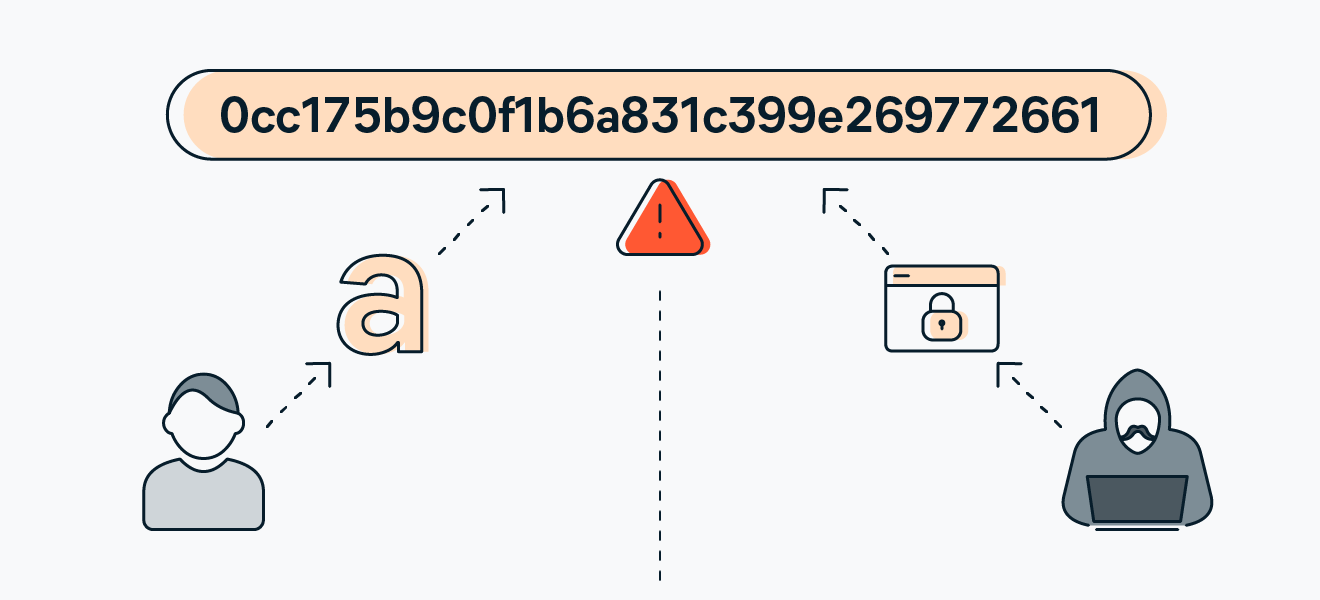
The first step to continue reading is to understand what MD5 is. The MD5 is an algorithm used to verify the integrity of files and messages. Broadly speaking, the MD5 generates a 32 character code called a hash, which is unique for each file or message. If something is changed in the file or message, the hash changes too.
We can summarize Its operation is that it is a method of encrypting files and messages. We will see it specifically on plain text messages, to give them security. In this way we can change a plain text word or password to a combination of letters and numbers. What we have mentioned above as a hash.
This encryption is used on secure web pages to convert the plain text of the login forms to a non-traceable format through sniffing. If you are not familiar with this term, we leave you this web page so that you can complete the definition of this term.
The weak point of this encryption method is that if a malicious user or hacker finds out, probably through the code of the web page on which they have detected spied user activity, they will be able to see that an MD5 function is being used. Therefore It will be enough to pass the extracted text through the login changing its property so as not to re-execute the MD5 on the field entry and you could enter with the captured credentials.
In any case, maybe this last part got a little technical. What MD5 can do and we will see in some later example is translate an existing, readable word into a combination of seemingly random characters to hide its true meaning.
What we must take into account is that This encryption method is not reversible. That is, we will not be able to later translate the result of an encryption to know what it meant. We will explain the reason in the next point.
How to calculate MD5
This can be calculated MD5 in different ways at the software level. However, for our little experiment so that you can know the process we will see it below. through a web tool.
MD5 Calculator Website
From this website, although searching on the internet you can find many more, We can easily calculate MD5 by writing plain text. We can use a password, for example. What we must keep in mind is that we can’t do it the other way around. That is, a code generated by MD5 will not be able to decipher what original content generated it.

To better explain why MD5 is not reversible, let’s give an example; When we use the MD5 generator, in the text data we are going to indicate 120 characters, of which we will get only about 32 characters when encoding it. Therefore, if we wanted to reverse this, How could the system accurately determine that 120 characters were used from only 32 characters? This is why the MD5 generator simply does not have this type of feature.
Knowing this, operation is unidirectional, and be very simple. All we have to do is write a text and click generate. However, the most interesting thing comes later, in the useful methods where to use it.
Where and how to use MD5
There are many ways to use MD5 to our advantage. Especially in the field of programming and services over the internet, as we mentioned before, to pass a password text from a login form in a protected format. This is a very simple and effective way to hide that password text while reaching the website service where the login is being done. Although we have more examples, this would be the most popular, and the one used by popular web pages that we will not mention in the article to preserve their security.
Calculate MD5 and use it in personal passwords
You may wonder how it is possible for us to use this encryption method that is not reversible. The answer is actually simple. We can use MD5 to protect our own passwords. We don’t need to translate something we already know, just turn it into the key that opens the door.
We will have an effective example where we will see where and how to use MD5. Let’s imagine that we want to set a password for a hard drive external where we have sensitive encrypted information. Our goal for using MD5 will be set a text passed through MD5 as an access password. In this way, even if we know that the password is a specific one, Not even if someone finds out that it is a certain word will they be able to access it.because it will be necessary to pass it through an MD5 first.
In this way we will have established as an access password a text encoded in MD5 and only this same encoded text will allow access to the supposed hard drive.
Can use this encryption method also for web page passwords. We can provide our keys with extra security or simply use them to make them safer against brute force attacks. The only problem with this will be that we will stop being able to remember themWell, it’s practically impossible. We would have to use some password manager software to store all credentials encrypted with MD5.
Now it’s your turn to tell us what you think of this encryption method, if you have ever used it, if you didn’t know about it, or if you can think of any other use for it.
We read you in the comments!