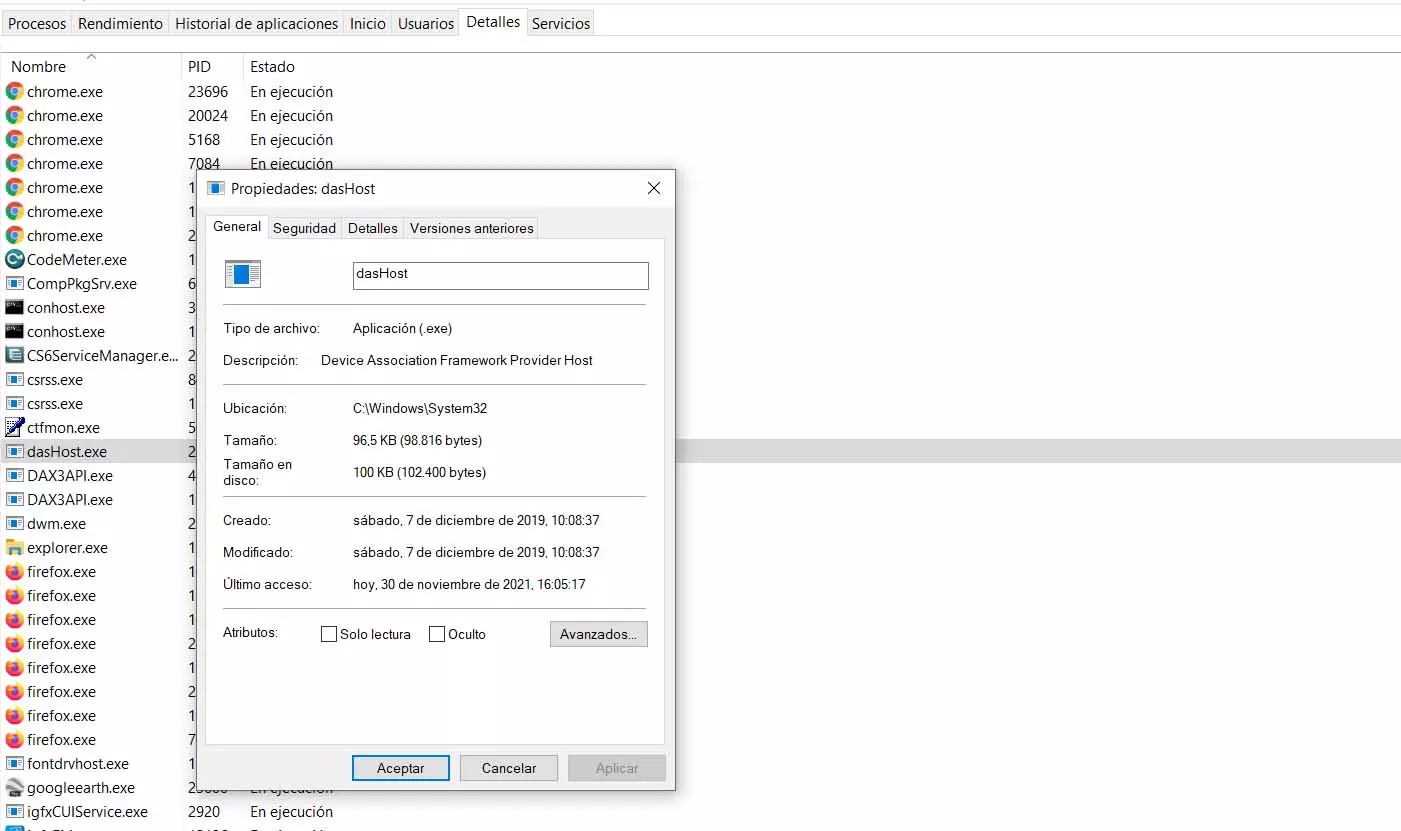
It will appear to us that it is running. If we click with the second mouse button and click Properties, we can see information about that file. This, as we will see, will help us to know if there is something strange behind it and it could be a threat.
So is dasHost.exe safe or dangerous?
The question that many users ask is whether it is really dangerous or not. As we have seen, it is a file that comes with the Windows system. It is, in fact, necessary to be able to use some devices. But of course, this could change and become a danger.
On some occasions we have seen malware that pretends to be a legitimate Windows process. This can pose a significant security risk as they could be collecting information or serving as an entry point for hackers. The dasHost.exe file could be used for this as well. But we will be able to follow some steps to verify whether or not it is reliable.
View location
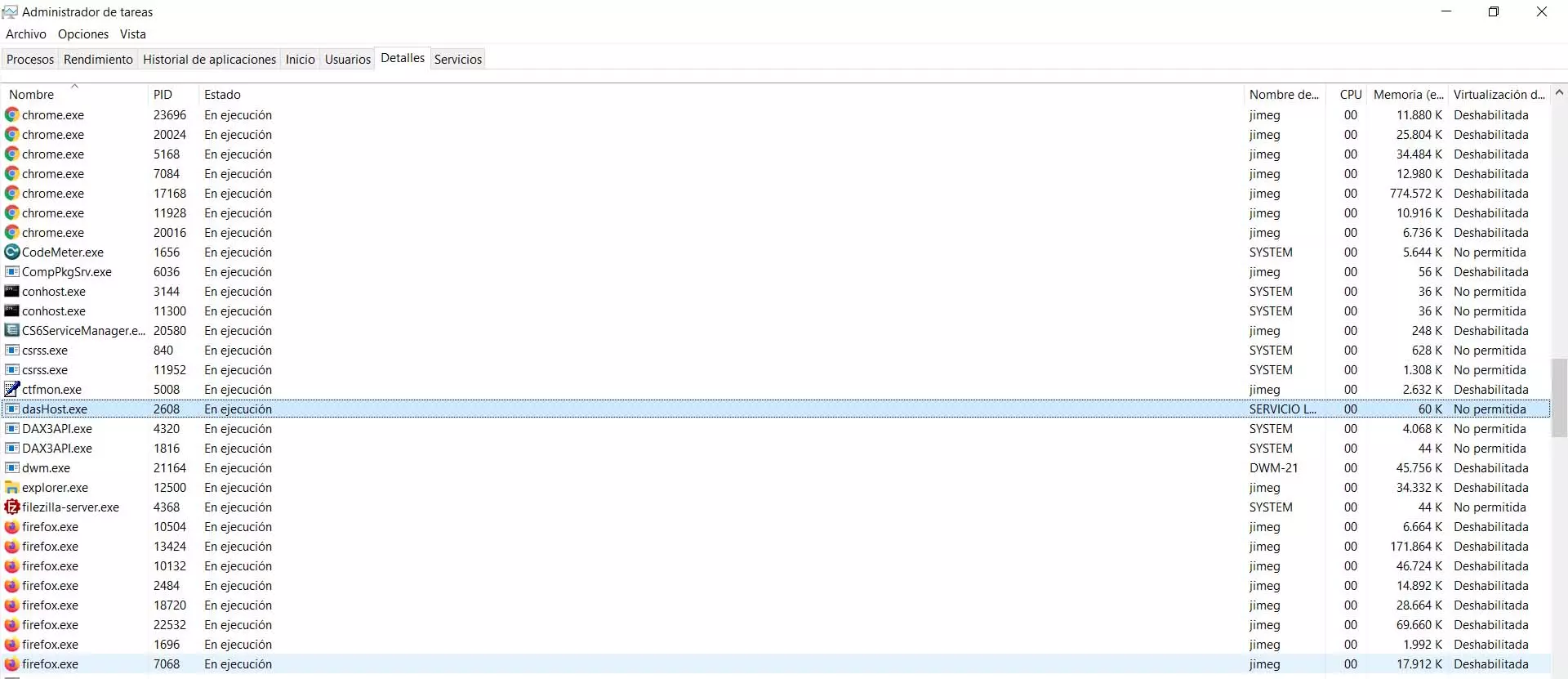
The first thing to do is check what is the dasHost.exe file location. To do this, simply go to the Task Manager, click with the second mouse button and click on Open file location. This will get us where you really are.
To verify that it is safe, the location would have to be System32. If we see that it is located in any other folder, whatever it is, it could mean that it is a false process, that it is not really the Windows one, and that it would be putting our security at risk.
Check the file size
Another option we have to detect if the dasHost.exe file may be false is to look at its weight. It should not take up more than 100KB. If we see that it is older, there is something strange. This could be one more sign that it has been modified or an intruder uses a process with the same name to infect Windows.
To see the size you just have to go once more to the Task Manager, click on Properties and there it shows us the size of the file. We will see that it occupies 100 KB, which would be the correct thing to do. The normal thing is that, in case it has been modified or it is a false process, that size is much higher.
In addition, we can additionally see in that same section the date and time the file was created, as well as the last access to it.
Scan with an antivirus
We can also parse the file with a antivirus. We can do this with any document that causes us concern and we want to know if it is really reliable or not. You just have to go to the location of the file and analyze it with the antivirus that we have installed.
We can use Windows Defender itself, as well as any other guarantee option that we have installed, such as Avast, Bitdefender, etc. If dasHost.exe is detected as a threat, the alert will automatically be triggered and we will be able to delete the file so that it does not cause any problems to the system.
We always recommend having security programs on our computers and this situation is one more example of why it can come in handy. Every time we have doubts about whether a file or document could be dangerous, we can simply run the antivirus and check it.
Give permissions
On the other hand, we could find ourselves in the situation where dasHost.exe requests us permissions to access a device, the network or even the firewall or antivirus asks us to unblock it so that it can work correctly.
After what we have seen, we can say that it is not a virus or threat. As long as we verify that it is the original file, the one that comes with Windows, we should not worry about having to grant permissions to dasHost.exe or even having Internet access.
However, it is normal that this situation does not arise. Windows should not ask us for permissions for dasHost.exe except for specific situations, such as having to act when connecting a device or similar. Only in those cases will we have to give those permissions. It could also happen that a security program asks us.
Ultimately, if you come across the dasHost.exe process and wonder if it could be a virus or is it something safe, the answer is that you shouldn’t be afraid. This is a built-in Windows feature that you can use to connect some devices such as Bluetooth mice, keyboards, or headsets. Now, we have also seen that you can verify that it really is the legitimate file and there is no risk, however minimal, that it is due to a modified process by an attacker.