When we install new software or update an existing one on our PC, a priori we consider it to be a safe program, but this is not always the case. This is something that can be extended to applications of the importance and popularity of Google Chromeas is the case that concerns us now.
If we focus on everything related to privacy and security in the software we use on our computer, when talking about the web browsers this takes on even greater importance. They are those programs that we install and configure to move around the Internet and work with all kinds of personal data. Without a doubt, Google Chrome is the undisputed leader in the sector, so everything that happens with this software is very important.
We tell you all this because a series of attacks that compromise the security of certain websites are now being detected. The attackers are in charge of injecting a series of scripts that show false errors of google chrome auto update. It must be taken into account that they send malware to unsuspecting visitors who fall for the trap. It is important to know that this campaign has been running since last November 2022.
However, experts have been able to notice a much greater proliferation as of February 2023. This is something that has now been extended to other languages, including English. SpanishHence, it is something increasingly delicate. At the same time, it must be taken into account that it is a hoax that uses an update of the popular Google Chrome, which could affect hundreds of millions of users.
How this Google Chrome hoax infects the PC
In fact, by now a multitude of websites that have already been hacked through this malware distribution campaign that we are talking about. Among these we can find news pages or online stores, among many other approaches. It must be said that the attack begins by compromising these websites to inject malicious JavaScript code.
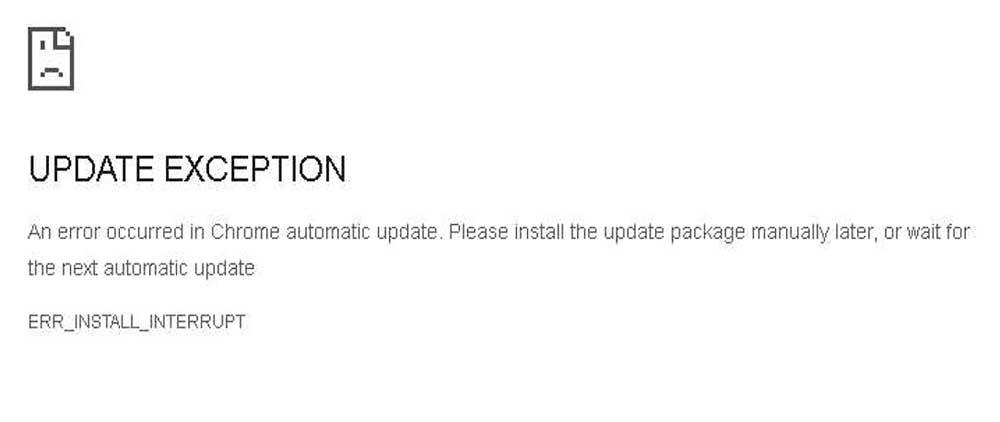
This is precisely the one that is in charge of executing scripts when a user visits them. The aforementioned malicious scripts are distributed hiding the origin server which hosts the files. With this, what is actually achieved is that the block lists are ineffective against this specific attack. When we move through one of these hacked websites, the malicious scripts show us a fake error screen from Google Chrome. It indicates that an automatic update necessary to continue browsing the web could not be installed.
It prompts us to download and install the update package. So the scripts then automatically download a ZIP file called release.zip that masquerades as the Chrome update the user is required to install. The compressed file has a miner money which will use the resources of the CPU of the PC to mine cryptocurrency without us noticing. Upon startup, the malware copies itself to the Program Files/Google/Chrome path as a file called updater.exe.
With all this, what we want to tell you is that if you find a message from update Chrome like the one we show you, get out of that page as soon as possible. Nor would it hurt to check the specified path for the file that we have mentioned to eliminate it. At the same time, it wouldn’t hurt to run a scan of our antivirus to make sure that the malicious code isn’t affecting our PC.