
A circulating phishing claim that you should pay a $ 1 or $ 2 “reprogramming fee” for your package. The thugs hope to collect contact information and subscribe to shadow service.
The great classic of parcel phishing has a new twist. Obviously, his scenario takes up the basics that made the success of the recurring scam. You would be contacted or contacted by a delivery company (La Poste, Colissimo, UPS) because a package intended for you is supposedly blocked at the warehouse. The alleged reasons vary, but the message always offers the same solution. You just need to pay a small amount of money (1 or 2 euros) to unblock the situation.
Usually, criminals claim the existence of ” customs fees »: The sender of the parcel would not have paid enough tax and it would be up to you to pay for what is missing. But the new variant of phishing, received by email by a Numerama reader on August 21, 2021, this time claims to claim ” reprogramming fees “. More precisely, it asks you for the payment of just 1 euro. To make the message more credible, the thugs invent a tracking number (which in some cases corresponds to a real parcel number in transit) and they name the alleged depot where the parcel would be blocked.
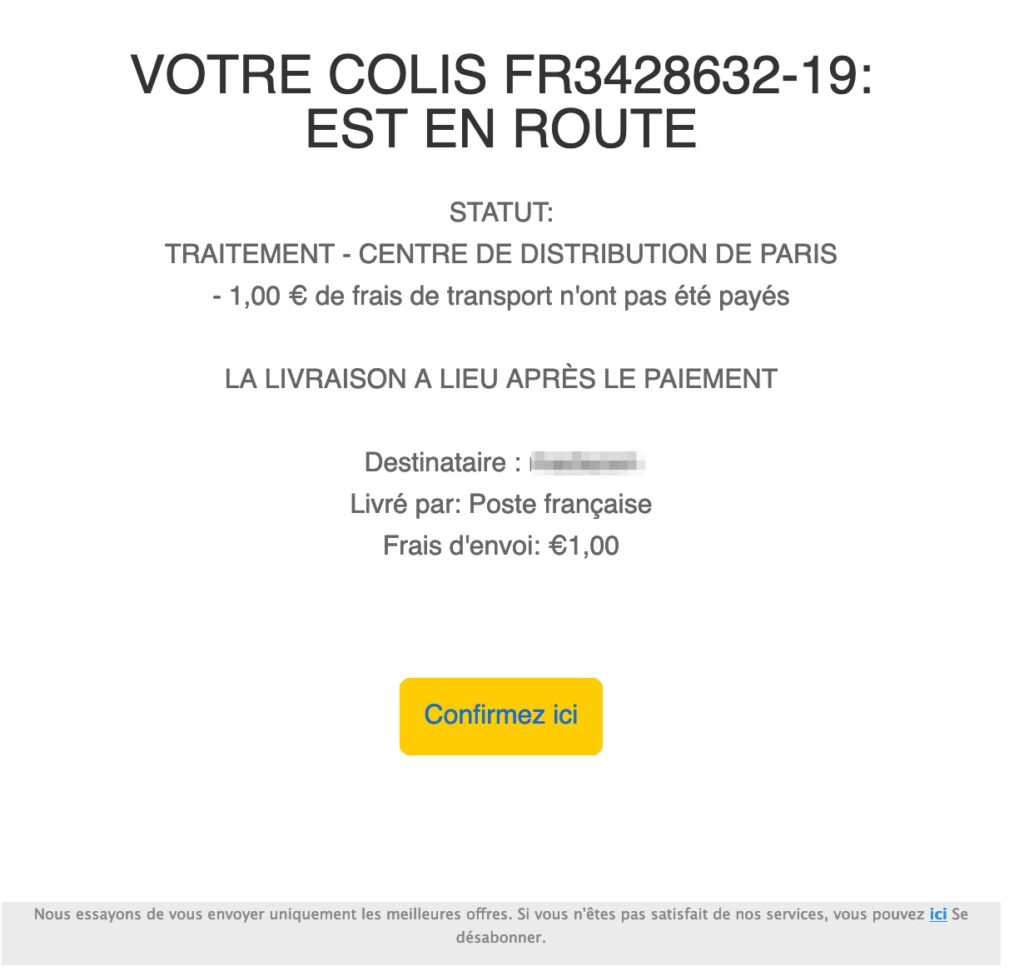
That’s not all: the message prompts you to make the payment ” within 24 hours Otherwise you may never get the precious package back. The sense of urgency is one of the tricks most used by thugs : It aims to hasten the decision of victims and make them less attentive to the shady details of phishing.
If criminals use package phishing so much, it is because it makes it possible to target a very large number of victims:
- People who buy a lot online are often waiting for a package;
- Those who never shop online might still receive a package from friends or even a business.
Keep in mind that criminals send their phishing to lists of emails and phone numbers that they have taken more or less at random. They often have little specific information about the victims – possibly names and addresses – and they do not know if they are customers of a particular company when they launch their mass scam message. They therefore have to imitate an organization with which the largest number of people are confronted, such as taxes, major brands, social security or even delivery companies.
False messages from La Poste
When we click on the link offered by phishing, a form opens. ” Unpaid delivery charges », Warns us a message in the center of the page. We allegedly have 50 minutes to act ” urgently “.

From this first message, the scenario of the thugs crumbles. The tracking number is no longer the same, we are no longer told about programming costs, and the site address seems frankly suspicious. We still click on the button ” following »: The site asks us to “Update our tracking information With our name and phone number. Once informed, we can finally proceed to the payment of the delivery costs of 1.00 euro.
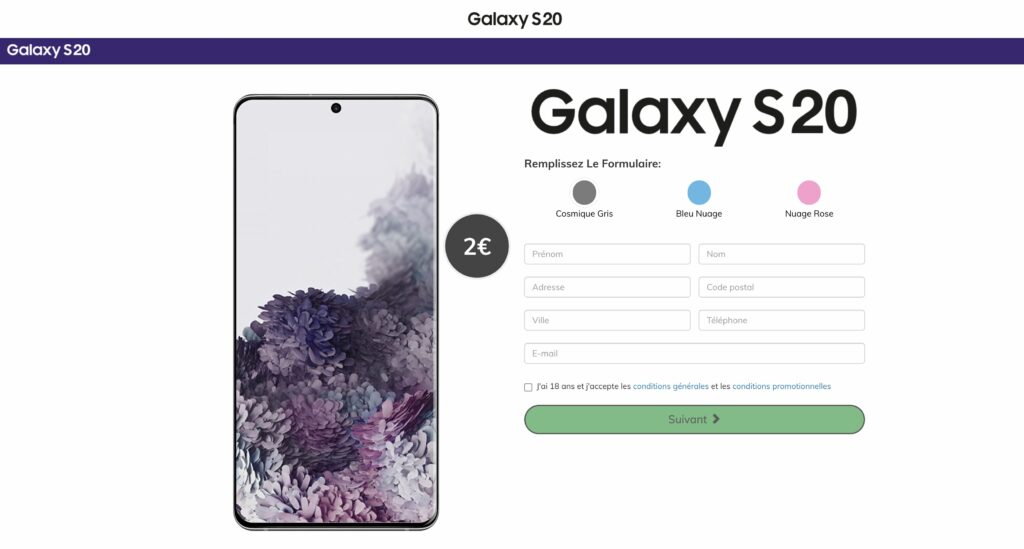
This is where phishing turns into nonsense. It redirects us to a fake Samsung Galaxy S20 smartphone sales page, unrelated to La Poste or parcels. This site makes believe that it would be enough to spend 2 euros to obtain the device which costs several hundred. Except that if the victim enters their information in a form, they subscribe for an indefinite period to a third-party service, here “spendometer.io”, a ” online personal spending planner “.
This kind of weird turn is common: another parcel scam took us to an online yoga class site, for example. It may be due to the amateurism of thugs, who assemble ready-made phishing pieces the wrong way; or it may be due to failed redirection games between the different phishing campaigns of the same operator.
Either way, the inconsistency of the message sequence makes phishing much less dangerous, and that’s a good thing. But beware of phishing at “reprogramming costs”, no doubt that it will be used again. And next time, he might be armed with malware.



