The objective of a firewall is to allow or block connection attempts, prevent unauthorized users from sending us different types of packets, we can also view and block any traffic carried out by the applications installed on our computer, in addition, we could also configure a detection system and intrusion prevention, with the aim of increasing its functionalities.
Today there are both software and hardware firewalls, logically hardware firewalls include an operating system with all the necessary functionalities to evaluate the network traffic to be allowed or blocked. However, there are different types of firewalls depending on how we configure them and what features they have. Next, we are going to explain in detail the different types that exist today.
types of firewalls
Currently we have different types, both for the Windows operating system as well as other software specifically oriented to firewalls. Knowing the difference between the different types is very important to choose the one that interests us.
Stateless Firewall or Stateless Firewall
This type of firewall is the most basic there is, it is known as “stateless firewall” or “firewall with packet filtering”. This is the oldest and simplest type we have, this type of firewall is usually installed within the perimeter of the network, it does not route any type of packet nor does it know if the different connections that are allowed have been established or not. This type of firewall works based on some basic predefined rules, where we must accept or deny the different packets, but never checking if the connection has been established, if it is related to other ports as it happens with the passive FTP protocol, nor if the connection is invalid.
Advantages
- It doesn’t cost a lot of money to do maintenance.
- Easy to set up in small networks, provided you have basic networking skills.
- Packet processing is very fast, it simply controls the headers where the destination source IP is, and also the TCP or UDP ports among other protocols.
- A single team can take care of filtering all the traffic on a network.
Disadvantages
- If your network is medium or large, it may be difficult to set up and maintain.
- It does not control established, related or invalid connections.
- If attacks are carried out at the application level, it is not capable of detecting and mitigating it.
- It does not have protection against all the attacks on data networks that exist.
If you want to have good security and prevent intrusions, our recommendation is that you do not use this type, without using the SPI (Stateful Packet Inspection).
Stateful Packet Inspection
This type of firewall is more advanced than the previous one, this type is known as “stateful”, and it is capable of knowing if a connection has been established, is related or even invalid. This type is the minimum that we should have to be quite protected against external threats. Being a stateful firewall, it is able to monitor the active connection, track and even limit the number of simultaneous connections on a given computer to protect against DoS attacks. Other very important features are that it is capable of preventing malicious traffic from gaining access to the internal network, since it can monitor connections in real time and even detect unauthorized access attempts.
Advantages
- It protects us much better than a stateless or stateless one.
- It is capable of monitoring and supervising incoming and outgoing connections.
- It knows if a connection has been established, and even how many concurrent connections there are.
- It allows you to record all traffic efficiently and quickly.
Disadvantages
- It is more complicated to configure than a stateless one.
- It does not protect against application level attacks.
- Some protocols do not have state information, such as UDP, so it is not able to check if these connections have been established.
- It consumes more computer resources by having to save the state of all connections.
This type of firewall is the one that is usually used when we use dedicated hardware, a Linux server and other devices. It is always recommended to use this instead of the previous one.
Application-Level Gateway Firewall
An application level firewall (ALG) is a kind of proxy that provides us with application security, the objective of this type of firewall is to filter incoming traffic based on certain rules. Not all applications that we use regularly are supported by ALG, for example, FTP, SIP, various VPN protocols, RSTP and BitTorrent protocol do support it. The way ALG works is as follows:
- When a client wants to connect to a remote application, the client actually connects to the proxy server, never directly to the end application.
- The proxy server will be in charge of connecting with the application, it will be the one that establishes communication with the main server.
- There will be communication between client and main server, but always going through the proxy.
Below, you can see the advantages and disadvantages:
Advantages
- Logging of all traffic is made easy as everything goes through the proxy.
- Easy to configure in certain cases, since we usually have a graphical user interface.
- Direct connection from outside the local network is not allowed, improves security.
Disadvantages
- It does not support all the applications that exist.
- Performance can be affected by using a proxy in between.
We have this ALG type available in most domestic routers, and, of course, also in professional ones.
Next-Generation Firewall
The Next-Generation Firewall or also known as NG-Firewall are very technologically advanced firewalls. They have Stateful Packet Inspection technologies, in addition, they carry out a deep inspection of all the packets that goes beyond looking at the header of the IP, TCP or UDP packet among other protocols, it is capable of seeing the payload that is sent with the objective protect us against more sophisticated attacks. These types of firewalls offer application-level inspection, which is why we go all the way down to layer 7 of the OSI model.
Although it generally offers the same benefits as an SPI firewall, it is more advanced by allowing dynamic and static packet filtering policies to be applied, along with advanced VPN support in order to protect all incoming and outgoing network connections. NGFWs are the most used in medium and large companies to protect all communications.
Advantages
- They are the safest.
- Very detailed record of everything that happens.
- Supports deep packet inspection, including at OSI level L7 for seamless protection.
Disadvantages
- It is very expensive, both hardware and software license and maintenance.
- It needs more hardware resources than a traditional one.
- To limit false negatives or positives, a training time is necessary to adjust it correctly.
This type is the most recommended for use in the business environment, since it incorporates the best of SPI and ALG, since it supports absolutely everything in addition to adding additional features in order to protect the network.
Conclusions
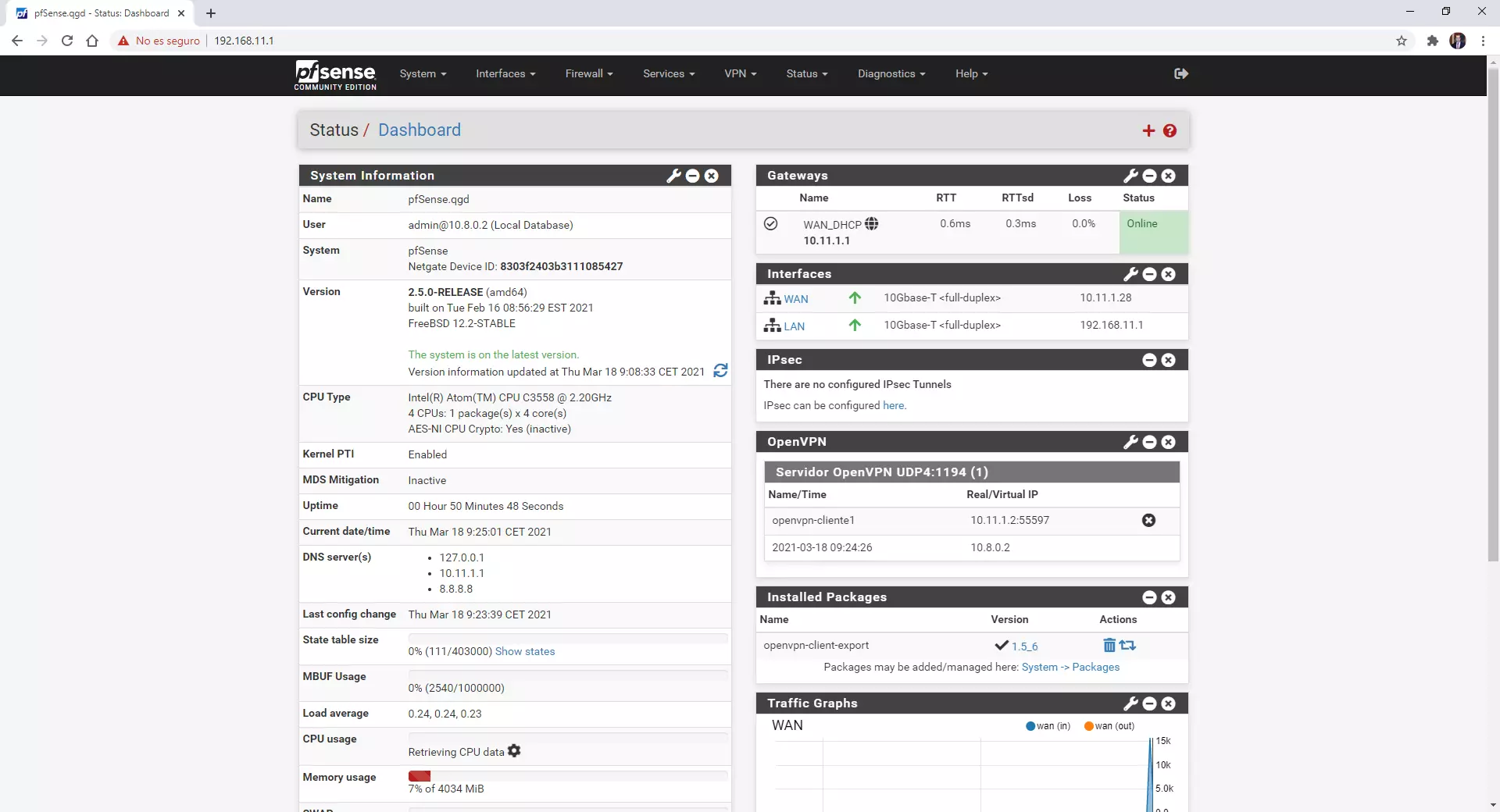
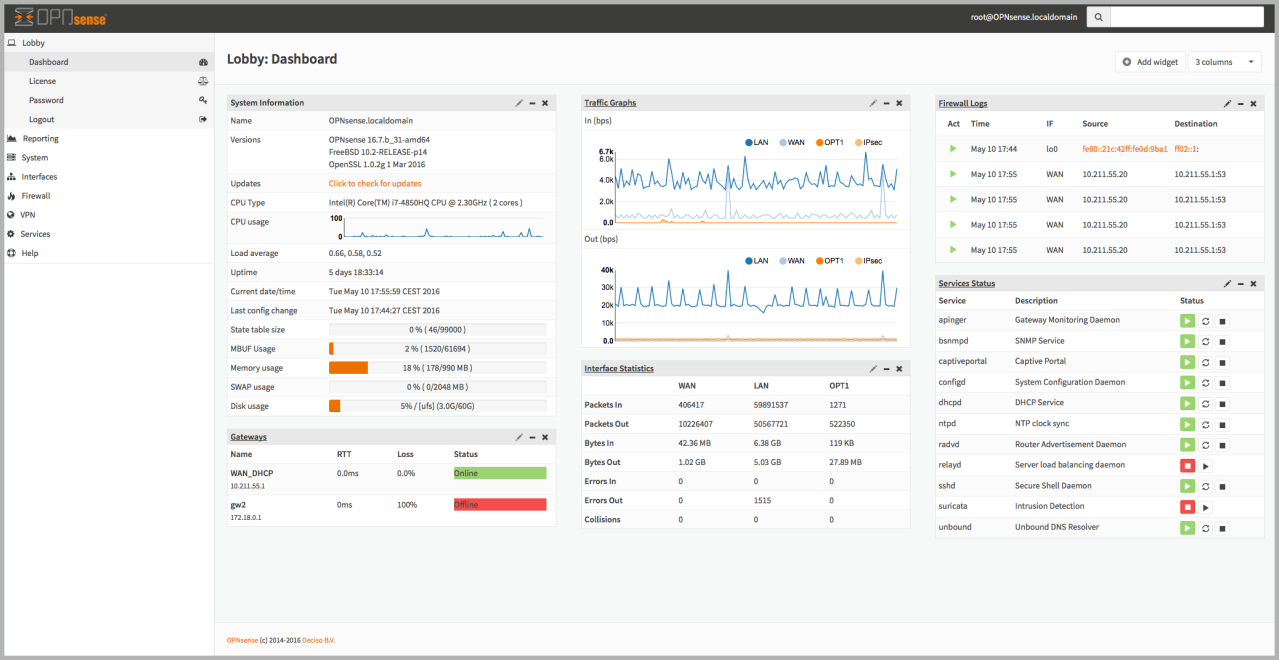
Having a firewall on our computer is something very basic and even the Windows or Linux operating system itself incorporates it. In domestic environments with WiFi routers, we have it integrated into the equipment itself, with iptables being the most used since the firmware of all routers is based on Linux, which is why it has this type of SPI (Stateful Packet Inspection) firewall. If we are in a somewhat more advanced environment and we want to protect everything at the network level, having a hardware firewall such as the Netgate appliances with pfSense or similar platforms is highly recommended, especially since they incorporate additional features such as IDS and IPS, in addition to be able to install and configure VPN servers easily and quickly.
Any computer or local network must have at least one SPI firewall, of course, medium and large companies always use NGFW that are much more advanced and allow us a greater ability to detect attacks and is even capable of mitigating malware, since They are responsible for performing a deep packet inspection at the L7 level, with the aim of protecting all the computers on the professional local network.